ITNET202A Enterprise Security
| Unit | ITNET202A Enterprise Security |
|---|---|
| Assessment Type | Report |
| Assessment Number | 2 |
| Assessment | Case Study |
| Weighting | 40% |
| Due Date/Time | Week 11 via Moodle Turnitin |
Assessment Description
The Australian Government Department of Social Security (AGDSS) is responsible for the development, maintenance, and delivery of the AU's social security program and of the AU government's policy for child support. The AGDSS currently employs around 90,000 staff and utilizes the largest civilian computer operation in Australia to provide services to its executive agencies, other government bodies, and various Independent Statutory Bodies. One of those executive agencies, the Information Technology Services Agency (ITSA), is responsible for providing the necessary IT systems and services, either internally or through contracts with the private sector.
Social Security spending is approaching $100 billion a year (2000), making it the biggest single spending department in government. At any given time, 70% of the population are in contact with the AGDSS. In 2000 the Department:
• Dealt with 15 million benefit claims, and 33 million changes of circumstances,
• Made nearly a billion payments (a great deal of which were handled electronically)
• Handled upwards of 160 million telephone enquires
Existing IT
Departmental IT systems have tended to be product-based rather than customer-centred. There are separate systems for each AGDSS agency. In the case of the Benefits Agency, there are separate systems for each benefit. Each benefit system has evolved as a series of processes, supported by its own IS/IT. These "Benefit Chimneys" support their own individual processes, and hold their own information. The consequence is unnecessary duplication and inefficiency, between processes and functions that are or could be, common. This is especially the case in the way that the Department uses the information it holds. This belies the fact that these systems have data and functions in common.
Strategic Objectives
Recognizing the problems inherent in a product-based approach, a Corporate IS/IT (CISIT) Strategy was developed to support government objectives for a modern, more responsive social security service. IS and IT are crucial, not just to change the Welfare State, but to fundamentally change, for the better, the way that the AGDSS delivers services. Within the IS/IT arena the changes have shifted the focus to the definition, and purchase, of services rather than products, and promotes a new sourcing strategy. Private sector service providers are expected to play a greater role in the development of the Department's new IS/IT systems to capitalize on their experience, expertise, and self-financing abilities.
The welfare system must be an active system. It must be simpler, more efficient, transparent, and easier to use. It must be better geared towards the needs of the people who actually use it, be they the general public or the Department's staff. IS and IT will have a key part in enabling these changes, in that any services must be:
• More accessible and easier to use than they are now
• More efficient and effective
• More accurate and less vulnerable to fraud
• Simpler and more flexible than they are now
Central to the Corporate IS/IT Strategy is the provision of a single logical data repository capable of supporting all of the Department's core business activities. This will reduce duplication of stored data and, thus costs to the taxpayer and the potential for fraudulent claims. It will also ensure that information common to different benefits only needs to be captured once, so providing an improved service to the public.
The data will be complemented by a set of shared systems which will carry out common functions which need to be consistent, such as capturing information, calculating entitlements, and making payments. Ultimately such functions are also expected to be shared, with the intention that they maximize flexibility for, and responsiveness to, policy changes.
Greater freedom is permitted in local business practices, but local systems are required to work with the common services to provide cohesive end-to-end support of social security administration. The Australian Government as a whole is looking to new technology to improve the way government services are delivered: the Prime Minister has pledged to increase the number of opportunities for customers to access AGDSS services electronically. Using its Corporate IS/IT Strategy, the AGDSS intends to position itself to optimize its use of new technologies in order to provide better, simpler services for AGDSS customers and staff alike. It is also the intention of the AGDSS to modernize the links that exist with other government departments and other relevant organizations, such as Local Authorities. What is needed to be achieved in social security - flexible, easy-to-use and efficient services, based on common information - needs to be achieved across government. This is known as "joined-up" government and is focused on delivering the goals of government as a whole in a seamless, integrated way. This will enable staff to concentrate on delivering a better service to clients, whilst improving efficiency and effectiveness through IT support.
A. Components to deliver:
1. High-level security architecture (SABSA). I suggest that you use reference architectures if you can find these. The purpose of this work product is to show what types of security services you intend to provide, what types of networks and servers are required for AGDSS. In your design, You need to address these requirements for your new system:
• More accessible and easier to use than they are now
• More efficient and effective
• More accurate and less vulnerable to fraud
• Simpler and more flexible than they are now
Indicative example only:
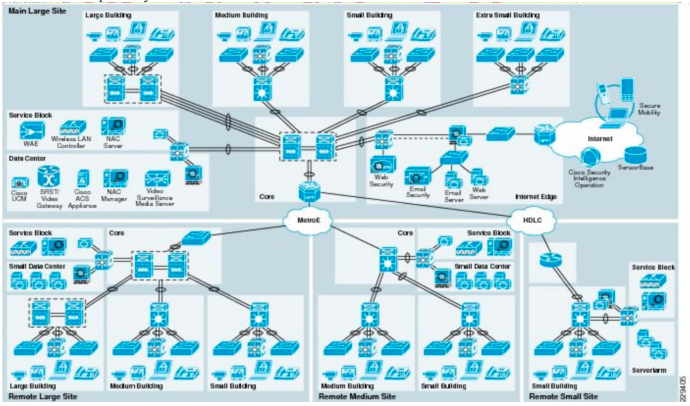
You will need to make reasonable assumptions about sizing, capacity, etc. of the various IT systems, and you need to provide a design for best security practice, i.e. cost is less of an issue than having security exposures and weaknesses.
2. Detailed (SABSA Logical and Physical level only) security architecture for each type of office in AGDSS.This will include specific details of what security services you will provide at office type? what networking technologies are you going to provide? what application systems will be protecting and what tools will be using?
Indicative example only:
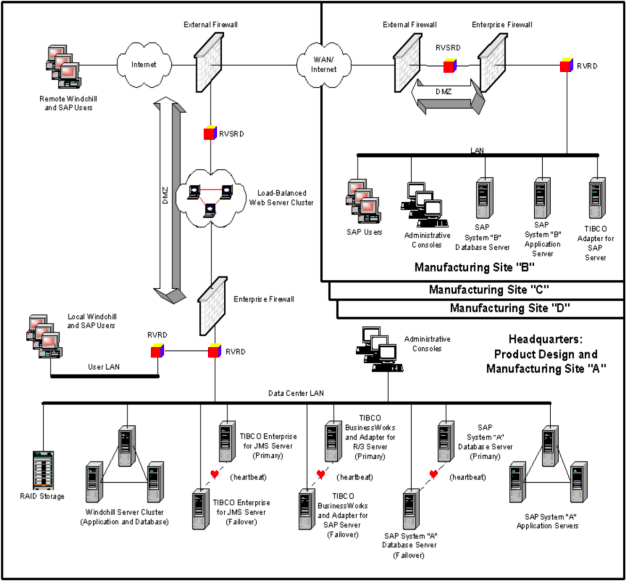
3. Costing estimates (both labour, hardware, and software, both for implementation and operation)
4. Resourcing estimates For these latter components, you would benefit from using the SABSA Framework for Security Service Management.
B. Approach:
Use the SABSA framework as a guide for your work products. Concentrate on the How, Who and Where (Process, People, and Location) columns. You will need to describe the existing AGDSS IT systems for which you will need to provide security services based on your security architecture. That means you have to research how AGDSS would be running its IT systems.
C. Deliverable work products:
Included in the set of work products you need to produce are:
1. Businessrequirements and risk assessments on which you will base your designs.
2. Use cases ,to describe interactions between AGDSS users, systems, and subsystems.
Indicative example only:
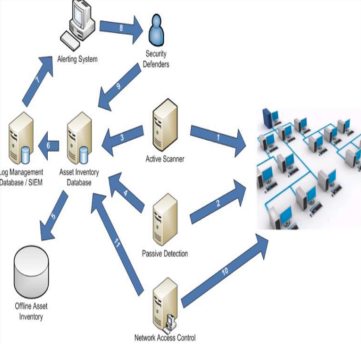
3. High-level security architectural diagrams and explanatory notes.
4. High-level logical network diagram and users interactions
Indicative example only:
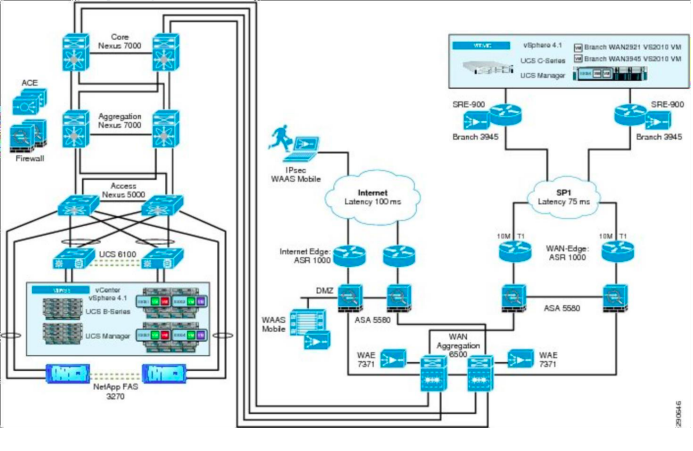
5. Description of the security services, you are planning to provide, why, and where they will be locatedto the AGDSS IT systems and networks.
6. Equipment lists, describing what equipment you will be implemented to provide these security services.
Detailed Submission Requirements
• Submission must be between 2000 – 2500 words (excluding references)
• All students submit the assessment through the Assessment Turnitin link on Moodle page for this
unit.Misconduct
• The assessment will be submitted through Turnitin via your unit page on Moodle.
• Turnitin is plagiarism software, which will identify if you have copied information and included it in your assessment.
• Copying information from others (i.e. websites, partner company information, or other students etc.) without the acknowledging the author is classified as misconduct.
• Engaging someone else to write any part of your assessment for you outside of the group work arrangement is classified as misconduct.
• To avoid being charged with Misconduct, students need to submit their own work and apply APA or Harvard Style Referencing (ask your lecturer (https://courses.highered.tafensw.edu.au/mod/page/view.php?id=48) if you do n know what this means, or you need assistance applying it).
• The TAFE misconduct policy and procedure can be read on the TAFE website ((https://www.tafensw.edu.au/about/policies-procedures/higher-education).
• Use the TAFE referencing guide accessible on Moodle.
Late Submission
• Any assessment submitted past the specific due date and time will be classified as Late.
• Any Late submission will be subject to a reduction of the mark allocated for the assessment item by 5% per day (or part thereof) of the total marks available for the assessment item. A ‘day’ for this purpose is defined as any day of the week including weekends. Assignments submitted later than one (1) week after the du date will not be accepted, unless special consideration is approved as per the formal process.
Special consideration
• Students whose ability to submit or attend an assessment item is affected by sickness, misadventure or other circumstances beyond their control, may be eligible for special consideration. No consideration is given when the condition or event is unrelated to the student's performance in a component of the assessment, or when it is considered not to be serious.
• Students applying for special consideration must submit the form within 3 days o the due date of the assessment item or exam.
• The form can be obtained from the TAFE website (https://courses.highered.tafensw.edu.au/mod/page/view.php?id=48) or on- campus P.4.32.
• The request form must be submitted to Admin Office. Supporting evidence shoul be attached. For further information please refer to the Student Assessment Policy and associated Procedure available on (https://www.tafensw.edu.au/about/policies-procedures/higher-education).
Rubric for Report (40 marks)
| Requirements | Total | High Distinction | Distinction | Credit Pass | Pass | Fail |
|---|---|---|---|---|---|---|
| Depth and
Breadth of
Coverage Demonstrating understanding or interpretation of key concepts of Enterprise security initiatives in the chosen organization, the implementation challenges and criteria for success | 10% | All aspects of the question are addressed in depth. | Most aspects of the question are addressed in depth. | Most aspects of the question are addressed adequately. | Basic aspects of the question are addressed adequately. | Responses are superficial and / or inadequately addressed the question. |
| 8.5 to 10 | 7.5 to 8.4 | 6.5 to 7.4 | 5 to 6.4 | 0 to 4.9 | ||
| Consistency between high level architecture, detailed architectures and detailed designs | 10% | The design covered full detailed enterprise architecture and design | The design covered the most detailed enterprise architecture and design | The design covered some detailed enterprise architecture and design | The design covered partial parts of enterprise architecture and design | The design did not cover enterprise architecture and design |
| 8.5 to 10 | 7.5 to 8.4 | 6.5 to 7.4 | 5 to 6.4 | 0 to 4.9 | ||
| Proof of application of security best practice in your solution | 5% | Your solution fulfills all aspects of company’s security concerns | Your solution fulfills the most aspects of company’s security concerns | Your solution fulfills some aspects of company’s security concerns | Your solution related in aspects of company’s security concerns | Your solution did not fulfill aspects of company’s security concerns |
| 4.3 to 5 | 3.8 to 4.2 | 3.3 to 3.7 | 2.5 to 3.2 | 0 to 2.4 | ||
| Relevance of your architectures and designsto business requirements and use cases | 5% | Demonstrate all related requirements for your solution in higher level. | Demonstrate most of related requirements for your solution in acceptable level | Demonstrate related requirements for your solution in acceptable level | Demonstrate some requirements for your solution | Demonstrate did not fulfill requirements for your solution |
| 4.3 to 5 | 3.8 to 4.2 | 3.3 to 3.7 | 2.5 to 3.2 | 0 to 2.4 | ||
| Critical Elements | 5% | The written work shows great depth of thought, excellent development of argument, logical analysis and insight into the subject. | The written work shows some evidence of analysis, supported by logical argument and insight into the subject. | The written work shows evidence of elementary analysis and the development of argument. | The written work is mainly descriptive, showing basic understanding of the topic. | The written work demonstrates limited understanding of the topic. |
| 4.3 to 5 | 3.8 to 4.2 | 3.3 to 3.7 | 2.5 to 3.2 | 0 to 2.4 | ||
| Structure, Language and References | 5% | All aspects of the written work conform to a high academic / professional standard. Cited references | Most aspects of the written work conform to a high academic / professional standard. Cited references | Most aspects of the written work conform to an acceptable academic / professional standard. | The written work displays basic structure. | The written work is not of an academic / professional standard. |
| 4.3 to 5 | 3.8 to 4.2 | 3.3 to 3.7 | 2.5 to 3.2 | 0 to 2.4 |

