ACCT 513 Accounting for Information Systems
Workshop 4 – Problem Document
Instructions:
- The following pages have answer areas for the chapter problems from the chapters for this workshop.
- Locate the problems in your textbook.
- Your instructor will evaluate your submitted work and determine the points you will earn for this activity.
- For all written responses use complete sentences, APA, proper grammar and cite sources when appropriate.
For workshop 1, complete the following problems for each chapter noted:
Chapter 12: 12.2 and 12.8; Chapter 13: 13.10; Chapter 14: 14.2 and Case 14-1
12.2What internal control procedure(s) would provide protection against the following threats?
- Theft of goods by the shipping dock workers, who claim that the inventory shortages reflect errors in the inventory records.
Counting goods when they are received and when they are sent to inventory storage as well as when goods leave inventory storage and are sent to shipping helps maintain control over inventory. Reconciling the two sets of counts makes it more difficult for employees to steal inventory as it is received and shipped.
- Posting the sales amount to the wrong customer account because a customer account number was incorrectly keyed into the system.
Using closed loop verification could help with this problem. For example, when the employee enters the account number the system could retrieve and display the account name so the employee can verify the correct account number had been entered (Romney & Steinbart, 2015). Additionally, including a portion of the company name with the account number for each client can help with batch posting because the system can verify the name matches after finding a match for the customer number prior to posting the sale. It is important to note that a validity check would not work for this specific problem because the account number entered exists; it just belongs to a different customer.
- Making a credit sale to a customer who is already four months behind in making payments on his account.
Careful monitoring of accounts receivable with up-to-date credit records would help with this problem. Having a current account receivable aging schedule will help identify which customers are current and which have fallen behind on payments and should not be allowed to purchase merchandise on credit. In addition, the company could program the system to flag a credit sale to a customer with a past due balance over a specific number of days.
- Authorizing a credit memo for a sales return when the goods were never actually returned.
To prevent this problem from occurring “the system should be configured to block credit memos for which there does not exist validated documentation that the goods have been returned by the customer” (Romney & Steinbart, 2015, p. 362).
- Writing off a customer’s accounts receivable balance as uncollectible to conceal the theft of subsequent cash payments from that customer.
To prevent this issue, having the proper segregation of duties is necessary. The same person that collects payments should not have the authorization to write off uncollectible accounts-one person should handle cash payments from customers and another should handle write-offs.
- Billing customers for the quantity ordered when the quantity shipped was actually less due to back ordering of some items.
The shipping order and packing slip should show the actual quantity shipped and the quantity backordered. Not only does this allow the billing to reflect the correct quantity shipped but it also helps to initiate the back ordering of the missing items. In addition, the system should be programmed to bill for quantity shipped not quantity ordered if the amounts are not the same.
- Theft of checks by the mailroom clerk, who then endorsed the checks for deposit into the clerk’s personal bank account.
The best way to prevent this problem is proper segregation of duties. The mailroom clerk should not have the responsibility for opening the mail, recording payments, and maintaining the receivables. In addition, having customers pay electronically, using two people assigned to open mail, utilizing a lockbox, or having the mailroom monitored by video cameras could prevent this problem.
- Theft of funds by the cashier, who cashed several checks from customers.
One way to prevent this issue is to have the mailroom create a cash prelist, send checks to the cashier and a copy of the cash prelist to a 3rd party. The cashier prepares a deposit slip for the checks-one goes to the bank with the check and one is sent to the 3rd party. The bank deposits the checks and send a validated deposit slip to the 3rd party. The 3rd party then compares the cash prelist, deposit slip, and validated deposit slip to be certain the cash received is the amount deposited.
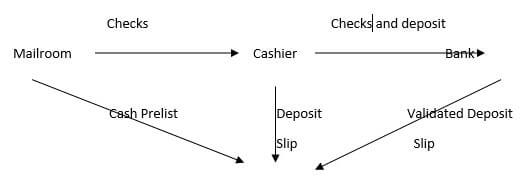
3rd Party compares cash prelist, deposit slip
from cashier, and validated deposit slip from bank
- Theft of cash by a waiter who destroyed the customer sales ticket for customers who paid cash.
Utilizing pre-numbered sales tickets could prevent this problem-both manual and automated. If the system is automated, the company could also incorporate a procedure where the kitchen does not prepare food until an order is entered, require staff to use authentication controls like an ID badge or smart card, and utilize reasonableness tests that compare inventory of food with sales from the tickets.
- Shipping goods to a customer but then failing to bill that customer.
To prevent this issue, segregating the shipping and billing functions is important. In addition, the system should be configured to compare sales orders, packing tickets, and shipping documents with sales invoices on a regular basis to determine if shipped items have been invoiced. For paper-based systems, pre-numbering all documents and periodically accounting for them identifies shipments that have not been invoiced (Romney & Steinbart, 2015).
- Lost sales because of stockouts of several products for which the computer records indicated there was adequate quantity on hand.
To prevent this issue, the company should do a regular physical inventories and compare them to the computer inventory records. In addition, incorporating sales forecasts can help a company better predict inventory needs and reduce the risk of stockouts (Romney & Steinbart, 215).
- Unauthorized disclosure of buying habits of several well-known customers.
Encrypting the data, restricting access by using authentication controls like passwords, and training employees on the importance of information privacy and confidentiality should help prevent this issue.
- Loss of all information about amounts owed by customers in New York City because the master database for that office was destroyed in a fire.
To prevent this issue, the company should do regular backups and store the most current off-site. In addition, having a cold or hot site and a well-developed disaster recovery plan is helpful.
- The company’s Web site was unavailable for seven hours because of a power outage.
The company should have a back-up generator that can run the site or use real-time mirroring so the system can immediately switch to the other site.
- Interception and theft of customers’ credit card numbers while being sent to the company’s Web site.
Encryption of credit card information prior to transmitting over the Internet. Typically this involves using SSL.
- A sales clerk sold a $7,000 wide-screen TV to a friend and altered the price to $700.
RFID tags and barcodes that automatically enter the pricing will help with this issue as would having a master list of prices and allowed discounts in the system. In addition, the sales clerk should not have authorization to change pricing unless it is approved by a manager and a log should be generated that shows the price changes, who approved them, and who rang them up.
- A shipping clerk who was quitting to start a competing business copied the names of the company’s 500 largest customers and offered them lower prices and better terms if they purchased the same product from the clerk’s new company.
To prevent this issue, the shipping clerk should be restricted from accessing the customer list. In addition, a log analysis would provide an audit trail of system access or attempted access.
- A fire in the office next door damaged the company’s servers and all optical and magnetic media in the server room. The company immediately implemented its disaster recovery procedures and shifted to a backup center several miles away. The company had made full daily backups of all files and stored a copy at the backup center. However, none of the backup copies were readable.
In order to prevent this issue the company should occasionally check to verify that the backups are readable and that they are capable of restoring the optical and media information.
12.8Parktown Medical Center, Inc. is a small health care provider owned by a publicly held corporation. It employs seven salaried physicians, ten nurses, three support staff, and three clerical workers. The clerical workers perform such tasks as reception, correspondence, cash receipts, billing, and appointment scheduling. All are adequately bonded.
Most patients pay for services rendered by cash or check on the day of their visit. Sometimes, however, the physician who is to perform the respective services approves credit based on an interview. When credit is approved, the physician files a memo with one of the clerks to set up the receivable using data the physician generates.
The servicing physician prepares a charge slip that is given to one of the clerks for pricing and preparation of the patient’s bill. At the end of the day, one of the clerks uses the bills to prepare a revenue summary and, in cases of credit sales, to update the accounts receivable subsidiary ledger.
The front office clerks receive cash and checks directly from patients and give each patient a prenumbered receipt. The clerks take turns opening the mail. The clerk who opens that day’s mail immediately stamps all checks “for deposit only.” Each day, just before lunch, one of the clerks prepares a list of all cash and checks to be deposited in Parktown’s bank account. The office is closed from 12 noon until 2:00 p.m. for lunch. During that time, the office manager takes the daily deposit to the bank. During the lunch hour, the clerk who opened the mail that day uses the list of cash receipts and checks to update patient accounts.
The clerks take turns preparing and mailing monthly statements to patients with unpaid balances. One of the clerks writes off uncollectible accounts only after the physician who performed the respective services believes the account will not pay and communicates that belief to the office manager. The office manager then issues a credit memo to write off the account, which the clerk processes.
The office manager supervises the clerks, issues write-off memos, schedules appointments for the doctors, makes bank deposits, reconciles bank statements, and performs general correspondence duties.
Additional services are performed monthly by a local accountant who posts summaries prepared by the clerks to the general ledger, prepares income statements, and files the appropriate payroll forms and tax returns.
Required:
- Identify at least three control weaknesses at Parktown. Describe the potential threat and exposure associated with each weakness, and recommend how to best correct them.
The weaknesses are identified for you. Describe the threat and the provide a recommendation.
- Weakness: The employees who perform services are permitted to approve credit without an external credit check.
Threat: Approving credit sales that become uncollectable.
Control: Perform an external credit check to establish credit limits. This should be done by someone other than the doctor providing the service.
- Weakness: The physician who approves credit also approves the write-off of uncollectible accounts.
Threat: Write-offs could be approved for accounts that can collected and not approved for accounts that cannot be collected. This would result in accounts receivable and bad debt expense being overstated or understated, depending on the scenario.
Control: Segregation of duties where one person approves credit for customer and another approves write-off of uncollectible accounts.
- Weakness: The employee who initially handles cash receipts also prepares billings and maintains accounts receivable.
Threat: Accounts receivable lapping is an issue if the employee decides to steal the cash and cover up the crime.
Control: Segregation of duties where one person handles the cash receipt, one handles the billing, and still another maintains accounts receivable.
- Weakness: The employee who makes bank deposits also reconciles bank statements.
Threat: Theft of cash from the deposit, which could result in overstatement of the cash balance.
Control: Segregation of duties where one person makes the bank deposit and another reconciles the bank statement.
- Weakness: The employee who makes bank deposits also issues credit memos.
Threat: The employee could steal from the deposit and issue a credit memo to cover up the theft.
Control: Segregation of duties where one employee makes the deposit and another issues credit memos.
- Weakness: Trial balances of the accounts receivable subsidiary ledger are not prepared independently of, or verified and reconciled to, the accounts receivable control account in the general ledger.
Threat: Without verification/reconciliation of the subsidiary ledger and the general ledger, earnings, cash receipts, and uncollectible accounts could be under or overstated. In addition, earnings, cash, and accounts receivable could be inaccurate because they were not recorded or recorded incorrectly.
Control: The accounts receivable subsidiary ledger should be reconciled and verified to the accounts receivable in the general ledger on a consistent basis.
13.10Last year the Diamond Manufacturing Company purchased over $10 million worth of office equipment under its “special ordering” system, with individual orders ranging from $5,000 to $30,000. Special orders are for low-volume items that have been included in a department manager’s budget. The budget, which limits the types and dollar amounts of office equipment a department head can requisition, is approved at the beginning of the year by the board of directors. The special ordering system functions as follows:
Purchasing A purchase requisition form is prepared and sent to the purchasing department. Upon receiving a purchase requisition, one of the five purchasing agents (buyers) verifies that the requester is indeed a department head. The buyer next selects the appropriate supplier by searching the various catalogs on file. The buyer then phones the supplier, requests a price quote, and places a verbal order. A prenumbered purchase order is processed, with the original sent to the supplier and copies to the department head, receiving, and accounts payable. One copy is also filed in the open-requisition file. When the receiving department verbally informs the buyer that the item has been received, the purchase order is transferred from the open to the filled file. Once a month, the buyer reviews the unfilled file to follow up on open orders.
Receiving The receiving department gets a copy of each purchase order. When equipment is received, that copy of the purchase order is stamped with the date and, if applicable, any differences between the quantity ordered and the quantity received are noted in red ink. The receiving clerk then forwards the stamped purchase order and equipment to the requisitioning department head and verbally notifies the purchasing department that the goods were received.
Accounts Payable Upon receipt of a purchase order, the accounts payable clerk files it in the open purchase order file. When a vendor invoice is received, it is matched with the applicable purchase order, and a payable is created by debiting the requisitioning department’s equipment account. Unpaid invoices are filed by due date. On the due date, a check is prepared and forwarded to the treasurer for signature. The invoice and purchase order are then filed by purchase order number in the paid invoice file.
Treasurer Checks received daily from the accounts payable department are sorted into two groups: those over and those under $10,000. Checks for less than $10,000 are machine signed. The cashier maintains the check signature machine’s key and signature plate and monitors its use. Both the cashier and the treasurer sign all checks over $10,000.
- Describe the weaknesses relating to purchases and payments of “special orders” by the Diamond Manufacturing Company.
- Recommend control procedures that must be added to overcome weaknesses identified in part a.
- Describe how the control procedures you recommended in part b should be modified if Diamond reengineered its expenditure cycle activities to make maximum use of current IT (e.g., EDI, EFT, bar-code scanning, and electronic forms in place of paper documents).
The Weakness has been identified for you.
|
Weakness |
Control |
Effect of new IT |
|
1. Buyer does not verify that the department head’s request is within budget. |
Compare request to budget amount and against year to date figures. |
IT would have an up to date amount remaining in the budget and can automatically compare the request against that amount. |
|
2. No procedures established to ensure the best price is obtained. |
Get bids and quotes for orders, perhaps set a dollar amount or size requirement. |
Internet or EDI can be used to get bids, |
|
3. Buyer does not check vendor’s past performance. |
Vendor performance reports should be filled out and on suppliers and then reviewed when choosing a vendor. |
Ratings on vendor performance are automatically updated and available to buyers at the click of a finger. |
|
4. Blind counts not made by receiving. |
Purchase orders sent to receiving should have quantity ordered blacked out and having an incentive or reward program for employees that detect errors. |
Receiving should be restricted from access to quantities ordered, bar coding or RFID tagging on purchase items with bar code readers and RFID scanners to check in purchases and incentives for detected discrepancies. |
|
5. Written notice of equipment receipt not sent to purchasing. |
Written notice of equipment receipt is sent to purchasing. |
Receiving info report entered into system on receiving terminal is sent or routed to purchasing. |
|
6. Written notice of equipment receipt not sent to accounts payable |
Written notice is sent to accounts payable. |
Program system to automatically send receiving report on equipment to accounts payable. |
|
7. Mathematical accuracy of vendor invoice is not verified. |
Verify the accuracy of the math on the vendor invoice. |
The math on the vendor invoice is automatically verified. |
|
8. Invoice quantity not compared to receiving report quantity. |
Compare the quantity received on the receiving report with the quantity on the invoice to verify accuracy. |
IT system automatically compares and verifies invoice quantity with receiving report quantity. |
|
9. Notification of acceptability of equipment from requesting department not obtained prior to recording payable. |
Get confirmation from the requisitioner of acceptability of equipment order prior to recording payable. |
Program system so it requires confirmation of acceptability of equipment before approval of invoice payment. |
|
10. Voucher package not sent to Treasurer. |
Send voucher package to Treasurer . Should include supplier invoice and associated supporting documentation. |
System is programmed to automatically correlate supplier invoice with supporting documentation. |
|
11. Voucher package not cancelled when invoice paid. |
Voucher package marked paid when check is signed. |
Program the system to cancel or mark all documents in the voucher package as paid when check is signed or payment made electronically. |
|
12. No mention of bank reconciliation. |
Consistent bank reconciliation by someone that did not participate in either cash collections or disbursements. |
Consistent bank reconciliation by someone that did not participate in either cash collections or disbursements. |
14.2 What internal control procedure(s) would best prevent or detect the following problems?
- A production order was initiated for a product that was already overstocked in the company’s warehouse.
Base the master production schedule on
- Current and accurate data on customer orders/sales
- Current and accurate sales forecasts
- Inventory levels of finished goods
- Inventory level of goods under production
Maintain accurate _perpetual_____ inventory records.
- A production employee stole items of work-in-process inventory.
- Document all internal movements of inventory (move tickets)
- Physical counts of inventory and reconciliation of those counts to recorded inventory
- Proper supervision by production supervisors
- Have employees sign on the amount released and the amount received for work in process transfers
- The “rush-order” tag on a partially completed production job became detached from the materials and lost, resulting in a costly delay.
- Rush order information included on production schedule
- Status reports from the ERP system to compare production against production schedule to detect problems with timely completion
- Mark materials with rush-order tags
- Monitor progress on rush orders
- A production employee entered a materials requisition form into the system in order to steal $300 worth of parts from the raw materials storeroom.
- Restrict authorization of materials rquistions to department supervisors
- Require signature of production employee for receipt of materials
- Examine differences between expected materials usage and actual usage for work in process
- A production worker entering job-time data on an online terminal mistakenly entered 3,000 instead of 300 in the “quantity-completed” field.
- Incorporate a limit check to validate the quantity entered against a fixed value like time scheduled or expected for the job
- Incorporate programming so that if the data entered is not acceptable it prompts the worker to re-enter until it is
- A production worker entering job-time data on an online terminal mistakenly posted the completion of operation 562 to production order 7569 instead of production order 7596.
- Have workers assigned to specific jobs and use closed loop verification to be certain the production order entered is associated with the worker entering the information
- Use closed loop cerification to verify the operation number correlates with the production order
- A parts storeroom clerk issued parts in quantities 10% lower than those indicated on several materials requisitions and stole the excess quantities.
The discrepancy should show up in an unfavorable materials usage variance, since the shortage will necessitate requesting additional goods. To deter this type of problem:
- Have the recipient of the materials sign for the quantity received
- Have the recipient of the materials held accountable for discrepencies
- A production manager stole several expensive machines and covered up the loss by submitting a form to the accounting department indicating that the missing machines were obsolete and should be written off as worthless.
- Have write offs for assets authorized by two managers
- Have the machinery inspected by a disinterested party before processing the write off
- Restrict authority for expensive machinery to executive management
- Accurately record/document the entire acquisition and disposal processes
- The quantity-on-hand balance for a key component shows a negative balance.
- Reconcile recorded inventory with physical inventory amounts
- Use sign checks to ensure use of the appropriate arithmetic sign
- Investigate errors to detect cause and correct it
- A factory supervisor accessed the operations list file and inflated the standards for work completed in his department. Consequently, future performance reports show favorable budget variances for that department.
- Log all changes to operations list file and review data in a timely way
- Restrict access to the operations list file to management of the engineering/design department
- Analyze variances between the standard usage and actual usage
- A factory supervisor wrote off a robotic assembly machine as being sold for salvage, but actually sold the machine and pocketed the proceeds.
- Authorization for asset write offs should be limited to management or executives
- Accurately record/document the entire asset disposal process
- Require assets for write off be authorized by two managers
- Have the machinery inspected by a disinterested party before processing the write off
- Overproduction of a slow-moving product resulted in excessive inventory that had to eventually be marked down and sold at a loss.
- Utilize information from customer orders, sales forecasts, and current inventory counts to develop an accurate master production schedule.
CASE 14-1 Case 14-1 The Accountant and CIM
Examine issues of the Journal of Accountancy, Strategic Finance, and other business magazines for the past three years to find stories about current developments in factory automation. Write a brief report that discusses the accounting implications of one development: how it affects the efficiency and accuracy of data collection and any new opportunities for improving the quality of performance reports. Also discuss how the development affects the risks of various production cycle threats and the control procedures used to mitigate those risks.
Task requirements:
- describe the development,
- the controller’s role, and
- the effect on production cycle threats.
- For all written responses use complete sentences, APA, proper grammar, include citations within the text and cite sources when appropriate.
Answer below:
Ford Motor Company has developed IntoSite to help address the difficulties of sharing best practices across sites and fostering communication between widely dispersed manufacturing centers (Greenfield, 2014). IntoSite is “a software-as-a service application that uses a cloud-based web application using the Google Earth infrastructure to provide virtual navigation within Ford’s assembly plants” (Greenfield, para. 2). The site, accessible via a web browser, holds 2D and 3D versions of Ford’s assembly plants and allows users to obtain a better understanding of processes by navigating virtually through the plant and workstations (Greenfield). Not only can the user view a video but engineers can also add pins at specific spots to input relevant information on parts, processes, or key issues as well as provide simulations so workers see how to perform a job properly (Greenfield).
IntoSite is also beneficial in financial and accounting areas. The “software allows production managers to look at a job before it becomes a job on the assembly line” (Greenfield, 2015, para. 6). The data gleamed from the software helps manage costs because there is better scheduling of labor hours and ordering of raw materials as well as more control of manufacturing overhead. In addition, controllers have data that is more relevant for the allocation of costs, which are lower because of the efficient streamlining of processes across locations through globally shared databases (Greenfield).
The development and use of IntoSite fosters communication between plants, provides consistency in manufacturing processes for each product, and allows access to documents relating to key issues. However, this development also raises a few concerns for the company. While the processes of assembly may not be patented, they are intellectual property for Ford so there is the concern of hacking by competitors. In addition, there is concern regarding user access. To deal with these issues, “IntoSite lies behind Ford firewalls using the same IT protection applied to all other Ford systems and any user has to be authorized to access the different systems connected to IntoSite, and each layer in the application is permission based” (Greenfield, 2014, para. 8). These steps not only protect Ford from the threat of intellectual property theft but they also provide assurances that only authorized users can view or change processes. This assurance means that unauthorized users cannot remove steps, change steps, or in any way alter the process or components used in the production process, which helps protect Ford from potential production cycle threats.
References:
Greenfield, D. (2014, April 1). Ford uses Google Earth for manufacturing collaboration.Automation World. Retrieved from http://www.automationworld.com
Romney, M & Steinbart, P. (2015). Accounting information systems (13th ed.). Upper Saddle
River, NJ: Pearson Education, Inc.
Buy ACCT 513 Accounting for Information Systems Answers Online
Talk to our expert to get the help with ACCT 513 Accounting for Information Systems to complete your assessment on time and boost your grades now
The main aim/motive of the management assignment help services is to get connect with a greater number of students, and effectively help, and support them in getting completing their assignments the students also get find this a wonderful opportunity where they could effectively learn more about their topics, as the experts also have the best team members with them in which all the members effectively support each other to get complete their diploma assignments. They complete the assessments of the students in an appropriate manner and deliver them back to the students before the due date of the assignment so that the students could timely submit this, and can score higher marks. The experts of the assignment help services at urgenthomework.com are so much skilled, capable, talented, and experienced in their field of programming homework help writing assignments, so, for this, they can effectively write the best economics assignment help services.
Get Online Support for ACCT 513 Accounting for Information Systems Assignment Help Online
Resources
- 24 x 7 Availability.
- Trained and Certified Experts.
- Deadline Guaranteed.
- Plagiarism Free.
- Privacy Guaranteed.
- Free download.
- Online help for all project.
- Homework Help Services
Testimonials
Urgenthomework helped me with finance homework problems and taught math portion of my course as well. Initially, I used a tutor that taught me math course I felt that as if I was not getting the help I needed. With the help of Urgenthomework, I got precisely where I was weak: Sheryl. Read More

