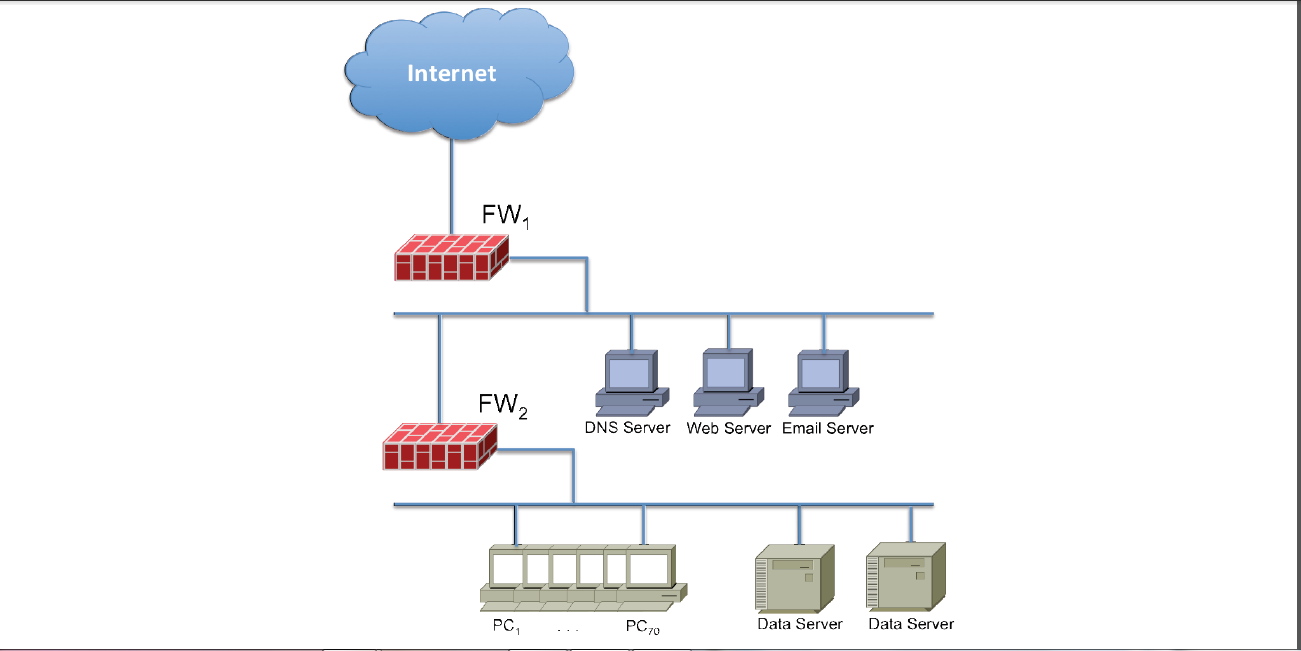
The Rockets4You Company is a large model rocket manufacturer mostly catering to the amateur market. It also has a Research and Development (R&D) department that works on next-generation model rockets. You are a newly appointed (and sole) member of the network security team for the R&D department. There are 50 employees working in the department, with over 70 PCs and 5 different servers: one DNS, Web, and Email server, and two replicated Data servers. The Web and Email servers are used as part of their research activity to engage with the amateur rocket community, and the data servers host their research data. They currently have two firewalls and the following diagram describes the overall network infrastructure of the department:
Information Technology Assignment Questions Questions
a) What is the main rationale for such network infrastructure and what are the main security threats that can be mitigated by this infrastructure? (a good answer would probably take 1-2 pages) (1 Page Answer)
b) List and discuss reasonable security policies that could be enforced in this network, in particular, how different network services (e.g., DNS, web, and email) can be accessed from the Internet and from the PCs. What policies should be enforced by FW1 and FW2, respectively? Are there any attacks that a ‘smart’ attacker could launch without being intercepted by the firewalls? (a good answer would probably take 2-3 pages) (2 pages Answer)
c) In addition to firewalls, the department would like to increase security by encrypting communications within the network. What are the main advantages and disadvantages of encrypting communications at the link layer and at the transport layer? What protocols could be used and how would they affect the overall network infrastructure? (a good answer would probably take 3-4 pages) (3 pages Answer)
d) In order to avoid increasing administration costs, the department is considering outsourcing the Data Servers to a third-party cloud service provider and accessing it over the Internet. Outline the main security implications of hosting the data server on a third-party cloud. Building on your analysis in question
discusses the mitigations you would recommend. (a good answer would probably take 2-3 pages) (2 pages Answer)
(e) The department also wants to extend the infrastructure with a WLAN network (assume the original infrastructure as shown in the figure). The wireless network will have two groups of users: employees and guests. The employees should use strong mutual authentication and have access to department data stored on the data server, while the guests should only have access to the Internet. How would you modify the network to incorporate the wireless network? Please include a diagram detailing your proposed changes as well as explaining your design choices. Given the authentication requirements, describe and justify the security mechanism(s) you would recommend. (a good answer would probably take 4-5 pages) (4 pages Answer)
Guidance
A long answer is not necessary: although there are several questions, it would be surprising if your final submission were more than twenty pages long; it might be somewhat shorter. Be sure, however, to answer thoroughly and (where appropriate) realistically.
The questions are progressively more-and-more open-ended. Answers which pursue the loose ends are of course those more likely to gain distinction-level grades. The questions are not all equally weighted.
Any discussion of the security of real/realistic systems is likely to be covered in-depth on a range of web sites. You are not expected to show a thorough knowledge of these, and you should certainly not make extensive quotes from websites or books. Of course, if you do refer to external sources of information, you must make clear what you have referred to, and the extent of any quote.
Information Technology Assignment Questions Sample Answers
- The Rockets4You company has a well-built network infrastructure for all their departments. The network is solely built based on the ethernet technology where all their department’s system, servers and other networking devices are connected via ethernet cables, as shows in the network diagram. Their research and development department are equipped with 70 PCs and five servers namely DNS, Email, Web and two replicated data servers which works for and used by 50 employees working there. They use a basic network design with basic networking equipment where they install two firewalls. One works for securing the three servers (DNS, Web and Email servers) and another is protecting all the PCs and data servers. The used network infrastructure by Rockets4You company is able to provide basic threat protection to the internal devices (servers and PCs). The level of security will depend upon the placement and configuration of firewall rules (access control). But, using two firewalls will offer a good level of protection to their internal systems and protect LAN from denial-of-service attacks. This configuration will no doubt, increase complexity of maintaining the network by the network administrator. Where they need different policies, patching and backup of the firewall rules, separately for both the firewalls (one? et al., 2020).
Using firewalls for protection and using limited network devices will provide them a good level of threat protection. Because both the servers and PCs are saved behind different firewalls. Both firewalls will log incoming and outgoing network traffic, manage access to internal resources via authentication certificates and secured logins. By this way, it prevents unauthorized access of the private network of the company. The major benefits of this network infrastructure are providing access control features, prevent unauthorize user to access and enter into the network and defend against various network and cyber threats which can attack on a network. As firewalls are evolving day by day, it is capable to provide protection against different types of threats. Some specific functions of a firewall are defending the network gateway, regulating and apply security policies, logging network activities for all internal and external users for the entire network, hiding the least protected devices or equipment via network address translation or NAT and report on and threat related activities identified in the network. Having these approaches, their designed network infrastructure is capable of handling their day-to-day business and all other activities (“What Firewall Do And What Firewalls Don’t Do”, 2020).