And edit storage resources view and edit blob
AZ-300T01
Deploying and Configuring Infrastructure
Contents
| ■ | Module 0 Start Here . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| ■ | Welcome to Deploying and Configuring Infrastructure . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | |||||||||
| . . . . . . . . . . . . . . . . . . . . . . . | ||||||||||
| ■ |
|
|
||||||||
| . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | ||||||||||
| . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
|
|||||||||
| Network Watcher . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
|
|||||||||
| Subscriptions and Accounts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | ||||||||||
| . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | ||||||||||
| Review Questions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | ||||||||||
|
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
|
||||||||
| ■ | . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | |||||||||
| Data Replication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | ||||||||||
| Storing and Accessing Data . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | ||||||||||
|
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
|
||||||||
| Review Questions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | ||||||||||
| Module 3 Module Deploying and Managing Virtual Machines (VMs) . . . . . . . . . . . . . . . . . . . . | ||||||||||
| ■ | Creating Virtual Machines . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | |||||||||
| Backup and Restore . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | ||||||||||
| Virtual Machine Extensions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
|
|||||||||
| Monitoring Virtual Machines . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
|
|||||||||
| Review Questions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | ||||||||||
| Module 4 Module Configuring and Managing Virtual Networks . . . . . . . . . . . . . . . . . . . . . . . . |
|
|||||||||
| ■ |
|
|||||||||
| Review of IP Addressing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | ||||||||||
| Network Routing |
|
|||||||||
| Intersite Connectivity . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
|
|||||||||
| Virtual Network Peering . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | ||||||||||
| Review Questions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | ||||||||||
| . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | ||||||||||
| Managing Azure Active Directory (AAD) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
|
|||||||||
| Implementing and Managing Hybrid Identities . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
|
|||||||||
Welcome to Deploying and Configuring Infra-structure
About This Course: Deploying and Configuring Infrastruc-ture
| ED | 2 |
|
|
|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT |
|
||
| Alerts and Activity Logs. In addition to alerts and logs, you will be introduced to Log Analytics as an | |||
| effective data analytics solution for understanding system status and health. And perhaps the most | |||
| exciting thing you will discover is how to utilize the Azure Resource Manager deployment model to | |||
|
|||
|
|||
|
|||
|
|||
| ● | |||
|
|||
|
|||
| ● | |||
| ● | |||
| ● | |||
| ● | |||
| ● |
|
||
|
|||
| ● | |||
|
|||
|
|||
| ● | |||
| ● | |||
| ● |
|
||
| ● |
|
||
Module 5 online lab:
● This module contains the lab Implementing User-Assigned Managed Identities.
Module 1 Module Managing Azure Subscrip-tions and Resources
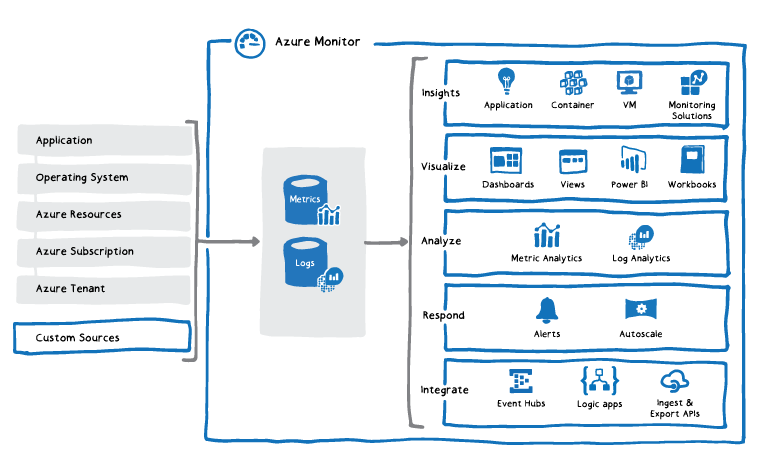
Exploring Monitoring Capabilities in Azure
| ED | 6 |
|
|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | ||
|
||
|
||
|
||
|
||
|
||
| Azure portal. Have a look at any virtual machine for example, and you'll see several charts displaying | ||
|
||
Exploring Monitoring Capabilities in Azure 7
Analytics page in the Azure portal and then either directly analyze the data using these tools or save queries for use with visualizations or alert rules.
● Guest OS monitoring data: Data about the operating system on which your application is running. This could be running in Azure, another cloud, or on-premises.
● Azure resource monitoring data: Data about the operation of an Azure resource.
Add an instrumentation package to your application, to enable Application Insights to collect detailed information about your application including page views, application requests, and exceptions. Further verify the availability of your application by configuring an availability test to simulate user traffic.
Custom sources
Exploring Monitoring Capabilities in Azure 9
| ● | Logs contain different kinds of data organized into records with different sets of properties for each |
|---|
Log data collected by Azure Monitor is stored in Log Analytics which includes a rich query language2 to quickly retrieve, consolidate, and analyze collected data. You can create and test queries using the Log Analytics page in the Azure portal and then either directly analyze the data using these tools or save queries for use with visualizations or alert rules.
Azure Monitor uses a version of the Data Explorer3 query language that is suitable for simple log queries but also includes advanced functionality such as aggregations, joins, and smart analytics. You can quickly learn the query language using multiple lessons. Particular guidance is provided to users who are already familiar with SQL and Splunk.
| ED | 10 |
|
|
|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | ● | ||
| ● | |||
| ● | |||
|
|||
| ● |
|
||
|
|||
|
|||
|
|||
|
|||
| Azure Fridays, Azure Monitor - https://channel9.msdn.com/Shows/Azure-Friday/Azure-Monitor/ | |||
|
|||
|
|||
| ● | |||
| ● | |||
| ● |
|
||
| ● |
|
||
| ● | |||
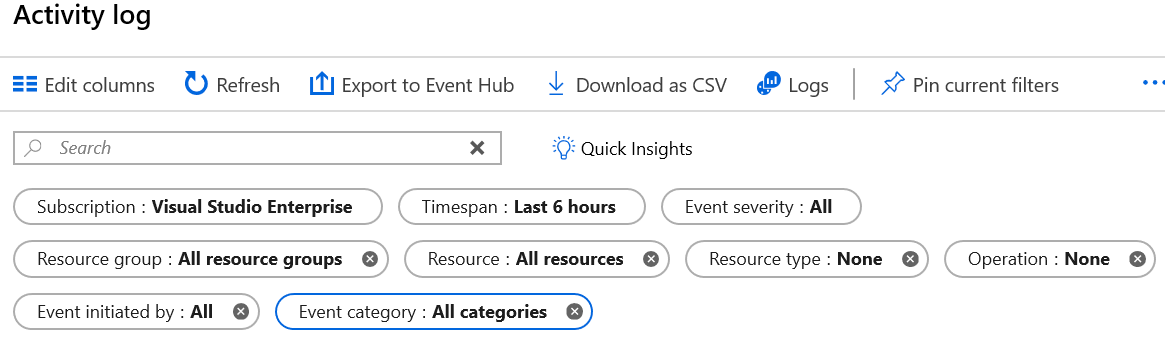
Query the Activity Log
| ● |
|
|---|
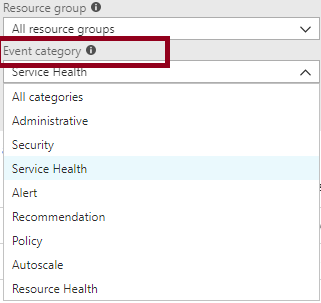
● Administrative. This category contains the record of all create, update, delete, and action operations performed through Resource Manager. Examples of the types of events you would see in this catego- ry include “create virtual machine” and "delete network security group". The Administrative category also includes any changes to role-based access control in a subscription.
● Security. This category contains the record of any alerts generated by Azure Security Center. An example of the type of event you would see in this category is “Suspicious double extension file executed.”
● Policy and Resource Health. These categories do not contain any events; they are reserved for future use.
| ED | 14 | ||
|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | |||
|
|||
| ● | |||
| ● | |||
| ● |
|
||
|
|||
| ● | Separation of Fired Alerts and Alert Rules. Alert Rules (the definition of the condition that triggers | ||
| ● | Better workflow. The new alerts authoring experience guides the user along the process of configur- | ||
|
|||
|
|||
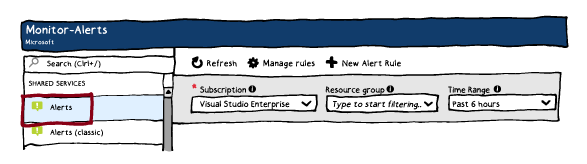
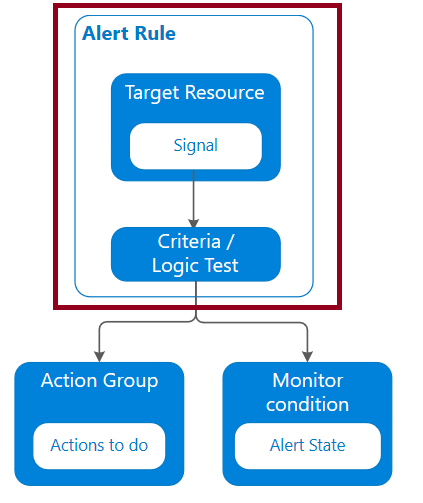
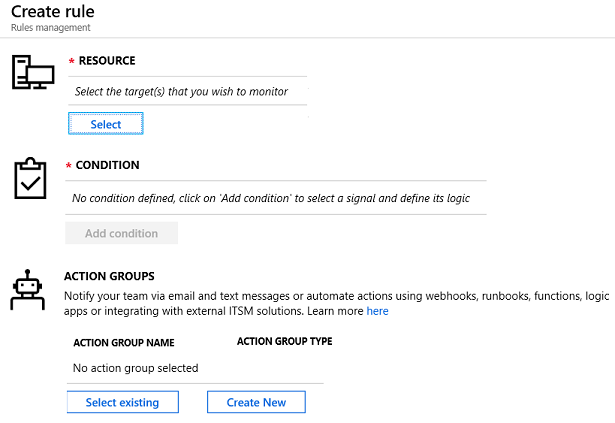
Alert rules are separated from alerts and the actions that are taken when an alert fires. The alert rule captures the target and criteria for alerting. The alert rule can be in an enabled or a disabled state. Alerts only fire when enabled. The key attributes of an alert rule are:
● Target Resource – Defines the scope and signals available for alerting. A target can be any Azure resource. Example targets: a virtual machine, a storage account, a virtual machine scale set, a Log Analytics workspace, or an Application Insights resource. For certain resources (like Virtual Machines), you can specify multiple resources as the target of the alert rule.● Severity – The severity of the alert once the criteria specified in the alert rule is met. Severity can range from 0 to 4.
● Action – A specific action taken when the alert is fired. See the Action Groups topic coming up.
| ED | 16 | ||
|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | |||
|
|||
|
|||
| Alert rules are separated from alerts and the actions that are taken when an alert fires. The alert rule | |||
| ● | |||
|
|||
|
|||
| ● | |||
| ● | |||
| Percentage CPU > 70%; Server Response Time > 4 ms; and Result count of a log query > 100. | |||
| ● |
|
||
| ● |
|
||
| ● | |||
An action group is a collection of notification preferences defined by the owner of an Azure subscription.
Azure Monitor and Service Health alerts use action groups to notify users that an alert has been trig-
● Email – Emails will be sent to the email addresses. Ensure that your email filtering is configured
● Function App – The function keys for Function Apps configured as actions are read through the
Functions API.
period for a response is 10 seconds. The webhook call will be retried a maximum of 2 times when the
following HTTP status codes are returned: 408, 429, 503, 504 or the HTTP endpoint does not respond.
| Azure Alerts 19 |
|---|
|
|
|---|---|
|
|
|
|
| Azure Alerts 21 |
|---|
5. Define the Alert logic. This will determine the logic which the metric alert rule will evaluate. 6. If you are using a static threshold, the metric chart can help determine what might be a reasonable threshold. If you are using a Dynamic Thresholds, the metric chart will display the calculated thresh- olds based on recent data.
7. Click Done.
● Administrative - This category contains the record of all create, update, delete, and action operations performed through Resource Manager. Examples of the types of events you would see in this catego- ry include "create virtual machine" and "delete network security group" Every action taken by a user or application using Resource Manager is modeled as an operation on a particular resource type. If the operation type is Write, Delete, or Action, the records of both the start and success or fail of that operation are recorded in the Administrative category. The Administrative category also includes any changes to role-based access control in a subscription.
● Service Health - This category contains the record of any service health incidents that have occurred in Azure. An example of the type of event you would see in this category is "SQL Azure in East US is experiencing downtime." Service health events come in five varieties: Action Required, Assisted Recovery, Incident, Maintenance, Information, or Security, and only appear if you have a resource in the subscription that would be impacted by the event.
● Security - This category contains the record of any alerts generated by Azure Security Center. An example of the type of event you would see in this category is "Suspicious double extension file executed."
| ● |
|
|---|---|
| 5 |
Azure Activity Logs and Log Analytics 25
Export the Activity Log with a Log Profile9
● How long the Activity Log should be retained in a Storage Account.
● A retention of zero days means logs are kept forever. Otherwise, the value can be any number of days between 1 and 2147483647.
Log Analytics Scenarios
One of the challenges with any broad data analytics solution is figuring out where you’re going to see value for your organization. Out of all the things that are possible, what does your business need? What we hear from customers is that the following areas all have the potential to deliver significant business value:
| 9 |
|---|
10 https://docs.microsoft.com/en-us/azure/monitoring-and-diagnostics/monitoring-overview-activity-logs
Azure Activity Logs and Log Analytics 27
Connected Sources
Ensure you can locate each of the following.
● The Log Analytics service (1) collects data and stores it in the OMS repository (2). The OMS Repository is hosted in Azure. Connected Sources provide information to the Log Analytics service.
| ED | 28 |
|
|---|---|---|
|
||
|
||
|
||
| When you configure the Log Analytics settings you can see the data sources that are available. Data | ||
|
||
|
||
|
||
|
||
To give a quick graphical view of the health of your overall environment, you can add visualizations for saved log searches to your dashboard. To analyze data outside of Log Analytics, you can export the data from the repository into tools such as Power BI or Excel. You can also leverage the Log Search API to build custom solutions that leverage Log Analytics data or to integrate with other systems.
The main query tables are: Event, Syslog, Heartbeat, and Alert.
Demonstration - Log Analytics
In this demonstration, you will work with the Log Analytics query language.Access the demonstration environment
1. Access the Log Analytics Querying Demonstration17 page.5. As you have time experiment with other Favorites and also Saved Queries.
✔️ Is there a particular query you are interested in?
|
|---|
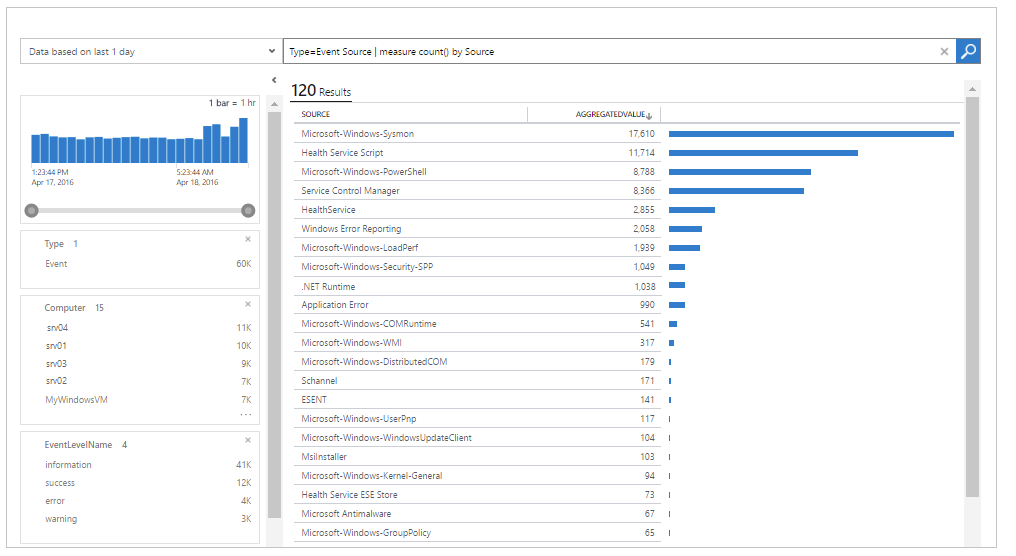
Take a few minutes to access the Log Analytics Querying Demonstration23 page. This page provides a live demonstration workspace where you can run and test queries. Some of the testing queries are:● See the volume of data collected in the last 24 hours in intervals of 30 minutes.
| ED | 34 |
|
|
|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT |
|
||
| ● | |||
|
|||
|
|||
| ● | |||
| helps you gather data for compliance, auditing and monitoring your network security profile. | |||
| ● | |||
|
|||
|
|||
|
|||
|
|||
| machine and an endpoint. The connection monitor capability monitors communication at a regular | |||
|
|||
| in your organization may, unknown to you, apply a custom route or network security rule to the web | |||
|
|||
| If an endpoint becomes unreachable, connection troubleshoot informs you of the reason. Potential | |||
| reasons might be DNS name resolution problem, the CPU, memory, or firewall within the operating | |||
Network performance monitor is a cloud-based hybrid network monitoring solution that helps you monitor network performance between various points in your network infrastructure. It also helps you monitor network connectivity to service and application endpoints and monitor the performance of Azure ExpressRoute. Network performance monitor detects network issues like traffic blackholing, routing errors, and issues that conventional network monitoring methods aren't able to detect. The solution generates alerts and notifies you when a threshold is breached for a network link. It also ensures timely detection of network performance issues and localizes the source of the problem to a particular network segment or device.
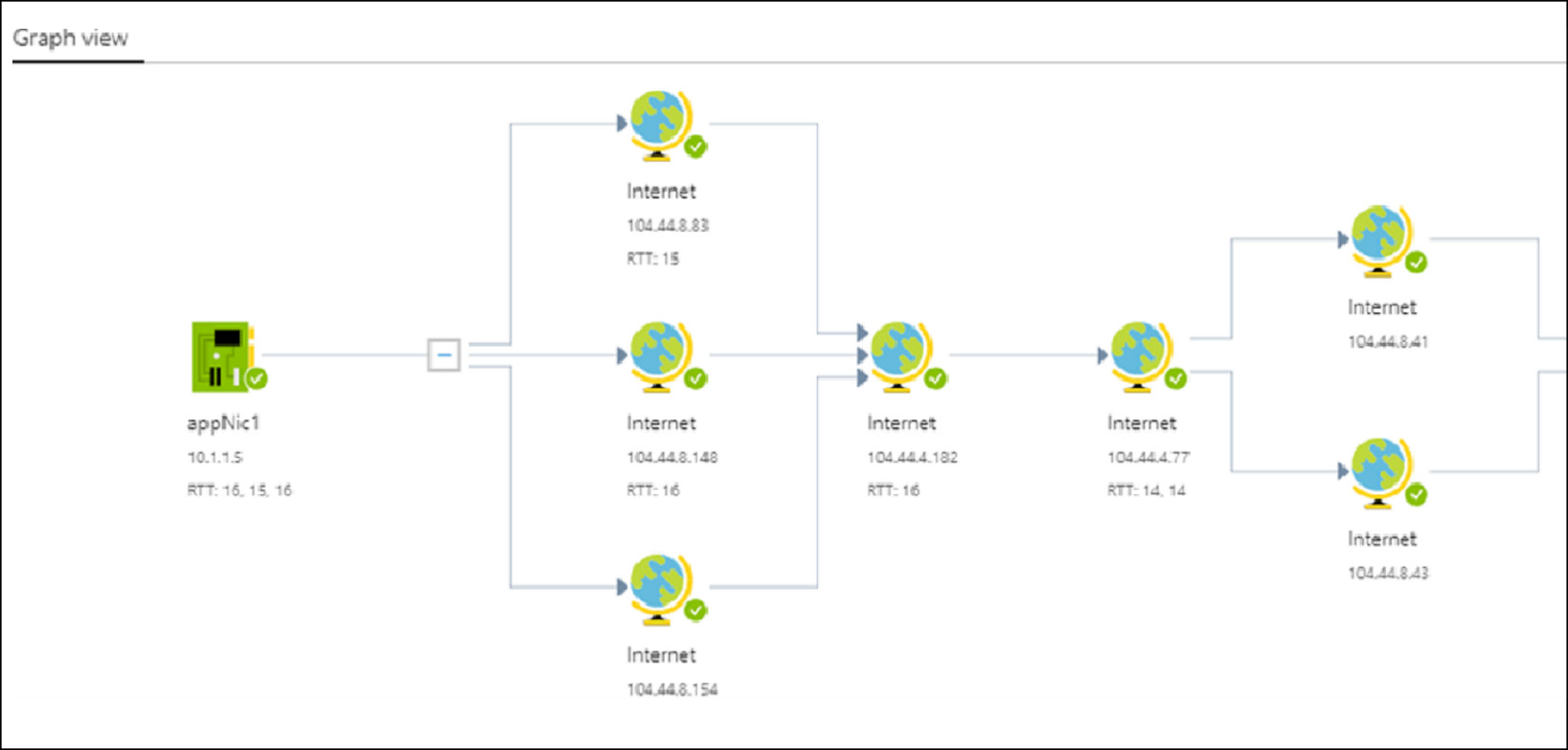
Topology
Verify IP Flow Purpose: Quickly diagnose connectivity issues from or to the internet and from or to the on-premises environment. For example, confirming if a security rule is blocking ingress or egress traffic to or from a virtual machine.
Example
| ED | 36 | |
|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | ||
| If IP flow verify does not return the expected behavior you can investigate the security rule that was | ||
|
||
|
||
|
||
| outbound traffic from all resources, such as VMs, deployed in a virtual network, are routed based on | ||
|
||
|
||
VPN Diagnostics Purpose: Troubleshoot gateways and connections.
Example
| ED | 38 |
|
|
|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT |
|
||
|
|||
|
|||
|
|||
| of networking tools and capabilities. Connection Troubleshoot enables you to troubleshoot network | |||
| ● | |||
| ● |
|
||
| ● |
|
||
| ● | |||
| ● | |||
| ● | |||
| ● | |||
|
|||
Further examples of different supported network troubleshooting scenarios include:
● Checking the connectivity and latency to a remote endpoint, such as for websites and storage end- points.
| ED | 40 | |
|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT |
|
|
|
● Organizational alignment for your Azure subscriptions through custom hierarchies and grouping.
● Targeting of policies and spend budgets across subscriptions and inheritance down the hierarchies.
For more information, you can see:
Organize your resources with Azure management groups - https://docs.microsoft.com/en-us/azure/ azure-resource-manager/management-groups-overview
Typically to grant a user access to your Azure resources, you would add them to the Azure AD directory associated with your subscription. The user will now have access to all the resources in your subscription. This is an all-or-nothing operation that may give that user access to more resources than you anticipated.
✔️ Do you know how many subscriptions your organization has? Do you know how resources are organized into resource groups?
Any Enterprise Agreement25 customer can add Azure to their agreement by making an upfront mone-tary commitment to Azure. That commitment is consumed throughout the year by using any combina-tion of the wide variety of cloud services Azure offers from its global datacenters. Enterprise agreements have a 99.95% monthly SLA.
Reseller
25 https://azure.microsoft.com/en-us/pricing/enterprise-agreement/
26 https://www.microsoft.com/en-us/licensing/licensing-programs/open-license.aspx
27 https://azure.microsoft.com/en-us/offers/ms-azr-0111p/
28 https://azure.microsoft.com/en-us/partners/directory/
| ED | 44 |
|
|
|---|---|---|---|
|
|||
|
|||
| ● | |||
| ● |
|
||
| ● |
|
||
| ● | |||
|
|||
|
|||
|
|||
|
|||
| agreement, with discounts for new licenses and Software Assurance. It's targeted at enterprise-scale | |||
|
|||
|
|||
|
|||
|
|||
There are three roles related to Azure accounts and subscriptions:
Account administrator
✔️ Account Administrators using a Microsoft account must log in every 2 years (or more frequently) to keep the account active. Inactive accounts are cancelled, and the related subscriptions removed. There are no login requirements if using a work or school account.
Check Resource Limits
| ED | 46 | ||
|---|---|---|---|
| The limits shown are the limits for your subscription. If you need to increase a default limit, there is a | |||
|
|||
|
|||
| “Development” to your resources. After creating your tags, you associate them with the appropriate | |||
|
|||
|
|||
| Perhaps one of the best uses of tags is to group billing data. When you download the usage CSV for | |||
| services, the tags appear in the Tags column. For example, you could group virtual machines by cost | |||
|
|||
| ● |
|
||
| ● | |||
|
|||
Subscriptions and Accounts 47
Reservations helps you save money by pre-paying for one-year or three-years of virtual machine, SQL Database compute capacity, Azure Cosmos DB throughput, or other Azure resources. Pre-paying allows you to get a discount on the resources you use. Reservations can significantly reduce your virtual ma-chine, SQL database compute, Azure Cosmos DB, or other resource costs up to 72% on pay-as-you-go prices. Reservations provide a billing discount and don't affect the runtime state of your resources.
Online Lab - Exploring Monitoring Capabilities in Azure 49
Online Lab - Exploring Monitoring Capabilities in Azure
● Deploy Azure VM scale sets
● Implement monitoring and alerting by using Azure Monitor
1. Deploy an Azure VM scale set by using an Azure QuickStart template
2. Review autoscaling settings of the Azure VM scale set
● Subsciption: the name of the target Azure subscription
● Cloud Shell region: the name of the Azure region that is available in your subscription and which is closest to the lab location
| ED | 50 | ||
|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | ● | ||
| ● | |||
| ● | |||
|
|||
|
|||
|
|||
|
|||
|
|||
| 9. In the Azure Portal, on the Deploy VM Scale Set with Python Bottle server & AutoScale blade, | |||
|
|||
| ● | |||
| ● | |||
| ● | |||
| ● |
|
||
| ● | Vmss Name: the custom label you identified when running Test-AzDnsAvailability earlier in | ||
|
|||
| ● | |||
| ● | |||
| ● | |||
|
|||
|
|||
| ● | |||
| ● |
|
||
| ● |
|
||
Exercise 2: Implementing monitoring and alerting by us-ing Azure Monitor
The main tasks for this exercise are as follows:
1. Create Azure VM scale set metrics-based alerts
2. Configure Azure VM scale set autoscaling-based notifications
3. Test Azure VM scale set monitoring and alerting.Task 1: Create Azure VM scale set metrics-based alerts 1. In the Azure portal, navigate to the blade representing the newly deployed Azure VM scale set and, from there, switch to the Monitoring - Metrics blade.
7. In the Condition section, click Add condition, select the Percentage CPU metric, leave the dimen-sion settings and condition type with their default values, set the condition to Greater than, set the time aggregation to Average, set the threshold to 60, set the period (grain) to Over the last 1 minutes, set the frequency to Every 1 minute and click done.
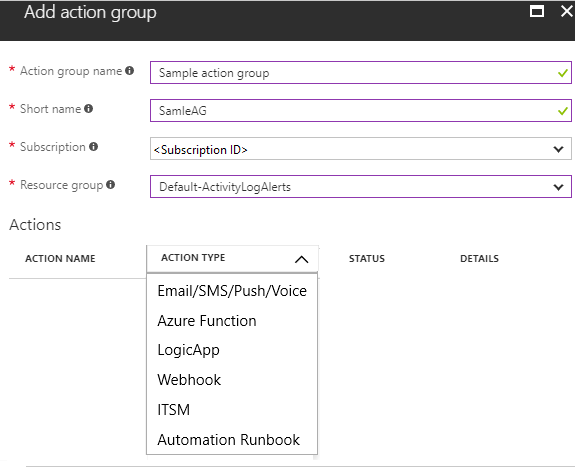
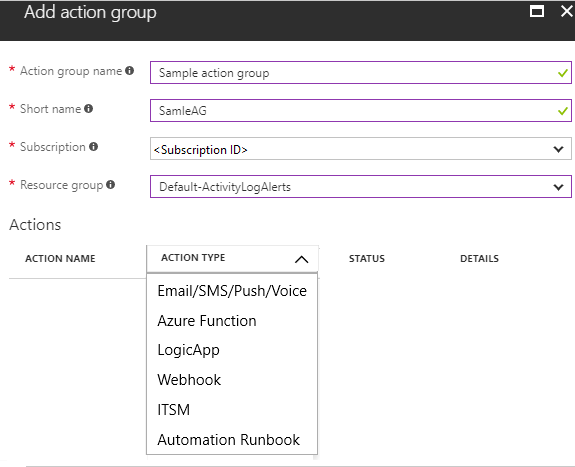
8. In the Action Groups section, click Create new, set the action group name to az30001 action group, set short name: az30001, select the Azure subscription you used in the previous exercise, accept the default name of the resource group of Default-ActivityLogAlerts (to be created), set the action name: az30001-email, and set the action type to Email/SMS/Push/Voice.
| ED | 52 |
|
|
|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT |
|
||
| ● | |||
| ● | |||
| ● | |||
|
|||
|
|||
| 1. In the Azure portal, navigate to the blade representing the Load balancer set you deployed in the | |||
| 3. From the lab computer, start Microsoft Edge and browse to *http://Public IP address*:9000 (where | |||
|
|||
| 5. Use the CPU (average) chart on the VM scale set blade to monitor changes to the CPU utilization. | |||
| 6. Note: Alternatively, you can navigate back to the Monitoring - Metrics blade and use the filter to | |||
|
|||
| 9. Note: Alternatively, you can navigate back to the Scaling blade, in the list of resources capable of | |||
|
|||
|
|||
|
|||
|
|||
|
|||
|
|||
Result: After you completed this exercise, you removed the resources used in this lab.
| Review Questions 55 |
|---|
You should use Azure Monitor and Azure Advisor.
Azure Monitor provides the fastest metrics pipeline (5 minute down to 1 minute), so you should use it for time critical alerts and notifications. These metrics can be sent to Azure Log Analytics for trending and detailed analysis.
Azure Storage is Microsoft's cloud storage solution for modern data storage scenarios. Azure Storage offers a massively scalable object store for data objects, a file system service for the cloud, a messaging store for reliable messaging, and a NoSQL store. Azure Storage is:
● Durable and highly available. Redundancy ensures that your data is safe in the event of transient hardware failures. You can also opt to replicate data across datacenters or geographical regions for additional protection from local catastrophe or natural disaster. Data replicated in this way remains highly available in the event of an unexpected outage.
Microsoft provides SDKs for Azure Storage in a variety of languages – .NET, Java, Node.js, Python, PHP, Ruby, Go, and others – as well as a mature REST API. Azure Storage supports scripting in Azure PowerShell or Azure CLI. And the Azure portal and Azure Storage Explorer offer easy visual solutions for working with your data.
Azure Storage is a service that you can use to store files, messages, tables, and other types of informa-tion. You can use Azure storage on its own—for example as a file share—but it is often used by develop-ers as a store for working data. Such stores can be used by websites, mobile apps, desktop applications,
| Azure Storage Accounts 59 |
|---|
● Configuration files can be stored on a file share and accessed from multiple VMs. Tools and utilities used by multiple developers in a group can be stored on a file share, ensuring that everybody can find them, and that they use the same version.
● Diagnostic logs, metrics, and crash dumps are just three examples of data that can be written to a file share and processed or analyzed later.
Table storage
Azure Table storage is now part of Azure Cosmos DB. To see Azure Table storage documentation, see the Azure Table Storage Overview. In addition to the existing Azure Table storage service, there is a new Azure Cosmos DB Table API offering that provides throughput-optimized tables, global distribution, and automatic secondary indexes. To learn more and try out the new premium experience, please check out Azure Cosmos DB Table API.
Premium storage accounts are backed by solid state drives (SSD) and offer consistent low-latency perfor-mance. They can only be used with Azure virtual machine disks and are best for I/O-intensive applica-tions, like databases. Additionally, virtual machines that use Premium storage for all disks qualify for a 99.99% SLA, even when running outside an availability set.
| Azure Storage Accounts 61 |
|---|
Storage Account Endpoints
Every object that you store in Azure Storage has a unique URL address. The storage account name forms the subdomain of that address. The combination of subdomain and domain name, which is specific to each service, forms an endpoint for your storage account.
✔️A Blob storage account only exposes the Blob service endpoint. And, you can also configure a custom domain name to use with your storage account.
For more information, you can see:
|
|
|---|---|
| Azure Storage Accounts 63 |
|---|
2. On the Storage Accounts window that appears, choose Add.
3. Select the subscription in which to create the storage account.
8. Leave these fields set to their default values:
9. Select Review + Create to review your storage account settings and create the account.
2. On the Storage Accounts window that appears, choose Add.
3. Select the subscription in which to create the storage account.
| 5 6 |
|---|
| Azure Storage Accounts 65 |
|---|
view and edit Blob,
Queue, Table, File, Cosmos DB storage and Data Lake storage. Storage Explorer is available for Windows, Mac, and Linux.Table storage
● Query entities with OData or query builder.Add, edit, and delete entities.●
● Import and export tables and query results.● View, add, and dequeue messages.
Clear queue.●
File storage
● Navigate files through directories.
Azure Storage Explorer has many uses when it comes to managing your storage. See the following articles to learn more.
| ● | |
|---|---|
| 7 8 |
| Azure Storage Accounts 67 | |
|---|---|
| ● |
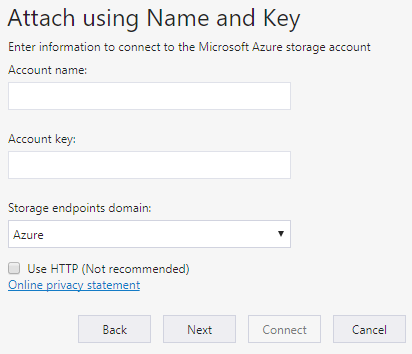
As mentioned previously, Storage Explorer lets you attach to external storage accounts so that storage accounts can be easily shared. To create the connection you will need the storage Account name and Account key. In the portal, the account key is called key1.
Demonstration - Storage Explorer
Note: If you have an older version of the Storage Explorer, be sure to upgrade. These steps use version 1.6.2.
2. After the installation, launch the tool.
3. Review the Release Notes and menu options.
| Data Replication 69 |
|---|
Data Replication
Replication Options
Are there any costs to changing my account's replication strategy?
| Data Replication 71 |
|---|
Zone Redundant Storage (ZRS) synchronously replicates your data across three (3) storage clusters in a single region. Each storage cluster is physically separated from the others and resides in its own availabili-ty zone. Each availability zone, and the ZRS cluster within it, is autonomous, with separate utilities and networking capabilities.
● ZRS may not protect your data against a regional disaster where multiple zones are permanently affected. Instead, ZRS offers resiliency for your data in the case of unavailability.
Support coverage and regional availability
ZRS currently supports standard general-purpose v2 account types. ZRS is available for block blobs, non-disk page blobs, files, tables, and queues.✔️Consider ZRS for scenarios that require strong consistency, strong durability, and high availability even if an outage or natural disaster renders a zonal data center unavailable.
Geo-redundant storage
| Data Replication 73 |
|---|
|
|
|---|---|
|
|
Create a storage account - https://docs.microsoft.com/en-us/azure/storage/common/storage-pow-ershell-guide-full#create-a-storage-account14
13 https://docs.microsoft.com/en-us/azure/storage/common/storage-redundancy-grs 14 https://docs.microsoft.com/en-us/azure/storage/common/storage-powershell-guide-full
Storing and Accessing Data 75
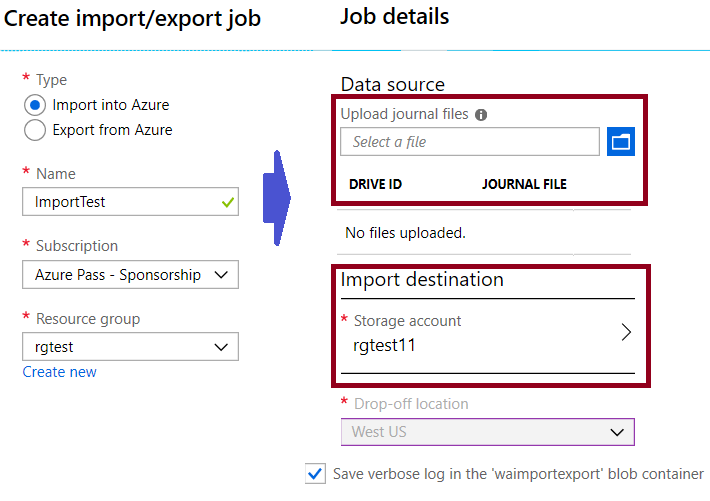
● Disk Drives. You can ship Solid-state drives (SSDs) or Hard disk drives (HDDs) to the Azure datacenter.
When creating an import job, you ship disk drives containing your data. When creating an export job, you ship empty drives to the Azure datacenter.
Supported disks
Import and Export Tool
The Microsoft Azure Import/Export Tool is the drive preparation and repair tool that you can use with the Microsoft Azure Import/Export service. You can use the tool for the following functions:
● Before creating an import job, you can use this tool to copy data to the hard drives you are going to ship to an Azure datacenter.● After an import job has completed, you can use this tool to repair any blobs that were corrupted, were missing, or conflicted with other blobs.
| ED | 76 | ||
|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | |||
|
|||
|
|||
| session. The state of the copy session is written to the journal file. If a copy session is interrupted (for | |||
|
|||
| For each hard drive that you prepare with the Azure Import/Export Tool, the tool will create a single | |||
|
|||
|
|||
| ● |
|
||
| ● | JournalFile. Path to the journal file that will be created. A journal file tracks a set of drives and records | ||
| ● | |||
| ● | DataSet. A CSV file that contains a list of directories and/or a list of files to be copied to target drives. | ||
|
|||
|
|||
Storing and Accessing Data 77
| ED | 78 | ||
|---|---|---|---|
| ● |
|
||
|
|||
|
|||
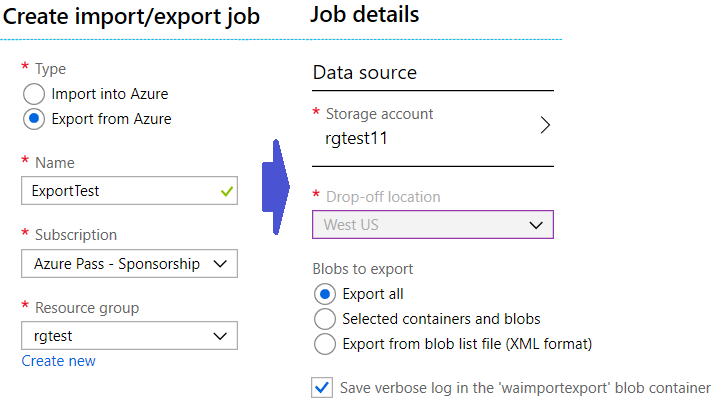
● Create an export job in your source storage account using the Azure portal or the Import/Export REST API.
● Specify the source blobs or container paths of your data in the export job.
17 https://docs.microsoft.com/en-us/azure/storage/common/storage-import-export-service
| ED | 80 |
|
|
|---|---|---|---|
| ● |
|
||
| ● |
|
||
| ● | |||
| ● | |||
| ● | |||
| ● |
|
||
| ● | Improved resiliency: every AzCopy instance will create a job order and a related log file. You can view | ||
|
|||
| ● | |||
| ● | |||
|
|||
|
|||
| ● | |||
|
|||
|
|||
|
|||
|
|||
|
|||
|
|||
azcopy /?
1. Scroll to the top of the Help information and read about the Common options, like: source, destina- tion, source key, and destination key.
3. Select Access keys and copy the Key Key1 value. This will be the sourcekey: value.
4. Drill down to the blob of interest, and view the file Properties.
2. Verify the blob was downloaded to your local directory.
Upload files to Azure blob storage
Note: The example continues from the previous example and requires a local directory with files. 1. The source: for the command will be a local directory with files.1. If you have errors, read them carefully and make corrections.
2. Verify your local files were copied to the Azure container.
Storing and Accessing Data 83
How CDN Works
3. The origin returns the file to the edge server, including optional HTTP headers describing the file's Time-to-Live (TTL).
4. The edge server caches the file and returns the file to the original requestor (Alice). The file remains cached on the edge server until the TTL expires. Azure CDN automatically applies a default TTL of seven days unless you've set up caching rules in the Azure portal.
Overview of the Azure Content Delivery Network - https://docs.microsoft.com/en-us/azure/cdn/ cdn-overview
Azure CDN POP locations by region - https://docs.microsoft.com/en-us/azure/cdn/cdn-pop-loca-tions
| ED | 84 | |
|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | ||
|
||
|
||
| The CDN service is global and not bound to a location, however you must specify a resource group | ||
| Several pricing tiers are available. At the time of this writing, there are three tiers: Premium Verizon, | ||
|
||
|
||
|
||
|
||
There are four choices for Origin type: Storage, Cloud Service, Web App, and Custom origin. In this course we are focusing on storage CDNs.
Create a new CDN endpoint - https://docs.microsoft.com/en-us/azure/cdn/cdn-create-new-end-point#create-a-new-cdn-endpoint19
Troubleshooting CDN endpoints returning 404 statuses - https://docs.microsoft.com/en-us/azure/ cdn/cdn-troubleshoot-endpoint
Storing and Accessing Data 87
Compression behavior tables - https://docs.microsoft.com/en-us/azure/cdn/cdn-improve-perfor-mance#compression-behavior-tables22
Troubleshooting CDN file compression - https://docs.microsoft.com/en-us/azure/cdn/cdn-trouble-shoot-compression
● Create a new CDN endpoint25.
Set Azure CDN caching rules
| ● |
|---|
| Monitoring Storage 89 |
|---|
Azure Monitor provides unified user interfaces for monitoring across different Azure services. Azure Storage integrates Azure Monitor by sending metric data to the Azure Monitor platform. With metrics on Azure Storage, you can analyze usage trends, trace requests, and diagnose issues with your storage account.
Azure Monitor provides multiple ways to access metrics. You can access them from the Azure Portal, Monitor APIs (REST, and .Net) and analysis solutions such as the Operation Management Suite and Event Hubs. Metrics are enabled by default, and you can access the past 30 days of data. If you need to retain data for a longer period, you can archive metrics data to an Azure Storage account.
Azure Storage metrics in Azure Monitor - https://docs.microsoft.com/en-us/azure/storage/common/ storage-metrics-in-azure-monitor?toc=%2fazure%2fstorage%2fblobs%2ftoc.json
Monitoring Azure applications and resources - https://docs.microsoft.com/en-us/azure/monitor-ing-and-diagnostics/monitoring-overview
| Monitoring Storage 91 | |
|---|---|
| ● |
For more information, you can see:
The new alerts experience in Azure Monitor - https://docs.microsoft.com/en-us/azure/monitor-ing-and-diagnostics/monitoring-overview-unified-alerts
● Target Resource – Defines the scope and signals available for alerting. A target can be any Azure resource. Example targets: a virtual machine, a storage account, a virtual machine scale set, a Log Analytics workspace, or an Application Insights resource. For certain resources (like Virtual Machines), you can specify multiple resources as the target of the alert rule.
● Signal – Signals are emitted by the target resource and can be of several types. Metric, Activity log, Application Insights, and Log.
| Monitoring Storage 93 |
|---|
Each action type is different in the details that must be provided. Here is a screenshot for the Email and SMS configuration.
● Email – Emails will be sent to the email addresses. Ensure that your email filtering is configured appropriately. You may have up to 1000 email actions in an Action Group.
| Monitoring Storage 95 |
|---|
● Resource. Select the resource you want to monitor. For example, resource group, virtual machine, or storage account.
| ED | 96 | ||
|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | ● | ||
| ● | |||
| ● |
|
||
| ● |
|
||
| ● | |||
|
|||
|
|||
|
|||
|
|||
|
|||
|
|||
|
|||
|
|||
|
|||
|
|||
3. Click Done to save the metric alert rule.
Signal Types and Metrics
● Support for multi-dimensional metrics: You can alert on dimensional metrics allowing you to monitor an interesting segment of the metric.
● More control over metric conditions: You can define richer alert rules. The newer alerts support monitoring the maximum, minimum, average, and total values of metrics.
Activity Log
The Azure Activity Log is a subscription log that provides insight into subscription-level events that have occurred in Azure. This includes a range of data, from Azure Resource Manager operational data to updates on Service Health events. The Activity Log was previously known as “Audit Logs” or “Operational Logs”.
| ED | 98 | ||
|---|---|---|---|
|
|||
|
|||
| ● | |||
| ● |
|
||
| ● |
|
||
| ● | |||
| ● | |||
|
|||
|
|||
| ● | |||
| ● | |||
| ● |
|
||
| ● |
|
||
|
|
|---|
Once you have defined a set of filters, you can save it as a query that is persisted across sessions if you ever need to perform the same query with those filters applied again in the future. You can also pin a query to your Azure dashboard to always keep an eye on specific events.
For more information, you can see:
● Administrative - This category contains the record of all create, update, delete, and action operations performed through Resource Manager. Examples of the types of events you would see in this catego- ry include “create virtual machine” and "delete network security group". The Administrative category also includes any changes to role-based access control in a subscription.
● Service Health - This category contains the record of any service health incidents that have occurred in Azure. An example of the type of event you would see in this category is “SQL Azure in East US is experiencing downtime.” Service health events come in five varieties: Action Required, Assisted Recovery, Incident, Maintenance, Information, or Security.
| Monitoring Storage 101 |
|---|
✔️ Log Analytics collects activity logs free of charge and stores the logs for 90 days free of charge. If you store logs for longer than 90 days, you will incur data retention charges for the data stored longer than 90 days. When you're on the Free pricing tier, activity logs do not apply to your daily data consumption.
For more information, you can see:
Advantages of this approach include:
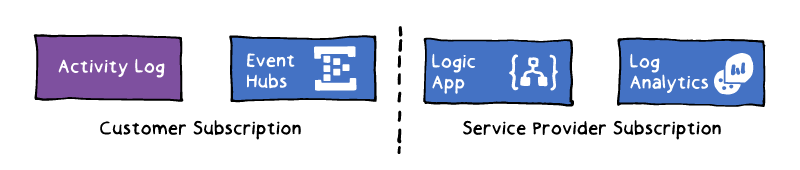
Collect Azure Activity Logs into Log Analytics across subscriptions - https://docs.microsoft.com/en-us/ azure/log-analytics/log-analytics-activity-logs-subscriptions
39 https://docs.microsoft.com/en-us/azure/event-hubs/event-hubs-what-is-event-hubs 40 https://docs.microsoft.com/en-us/azure/logic-apps/logic-apps-overview
| ED | 102 | |
|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | ||
|
||
|
||
|
||
|
||
|
||
|
||
Pricing for GPv2 accounts has been designed to deliver the lowest per gigabyte prices, and industry competitive transaction prices.
You can upgrade your GPv1 or Blob storage account to a GPv2 account using Azure portal, PowerShell, or Azure CLI.
Which tool should you use? How should you connect to client resources?
Suggested Answer ↓
Microsoft Azure Storage Explorer is a standalone app from Microsoft that allows you to easily work with Azure Storage data.• Available for Windows, Mac, and Linux.
Module 3 Module Deploying and Managing Virtual Machines (VMs)
1. Select an image or disk to use for your new virtual machine. The image is from the Marketplace. The disk is a VHD you have created.
2. Provide required information such as host name, user name, and password for the new virtual machine.
| ED | 106 | ||
|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | |||
|
|||
|
|||
|
|||
| Guest config - Add additional configuration, agents, scripts or applications via virtual machine exten- | |||
|
|||
| ● |
|
||
| ● | |||
| ● | Faster innovation for applications enabling Developers and IT Pros to create new and modernize their | ||
| ● | |||
Creating Virtual Machines 107
Terms of Use

| ED | 108 |
|
||
|---|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | ||||
| ● |
|
|||
|
||||
|
||||
|
||||
| ● | ||||
|
||||
|
||||
| ● | ||||
| ● | ||||
| ● | ||||
| ● |
|
|||
| ● |
|
|||
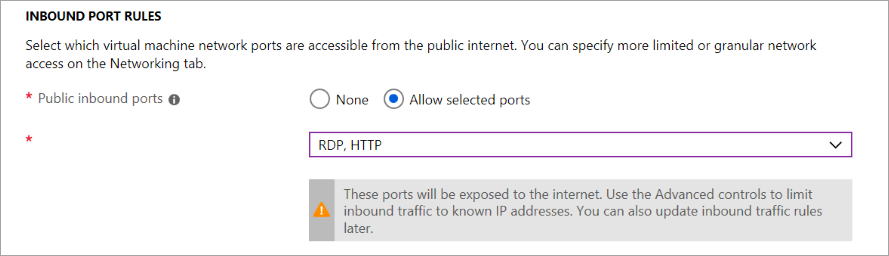
| WinRM uses by TCP port 5986 by default, but you can change it to a custom value. In either case, you | ||||
| must ensure that no network security groups are blocking inbound traffic on the port that you choose. | ||||
|
||||
|
||||
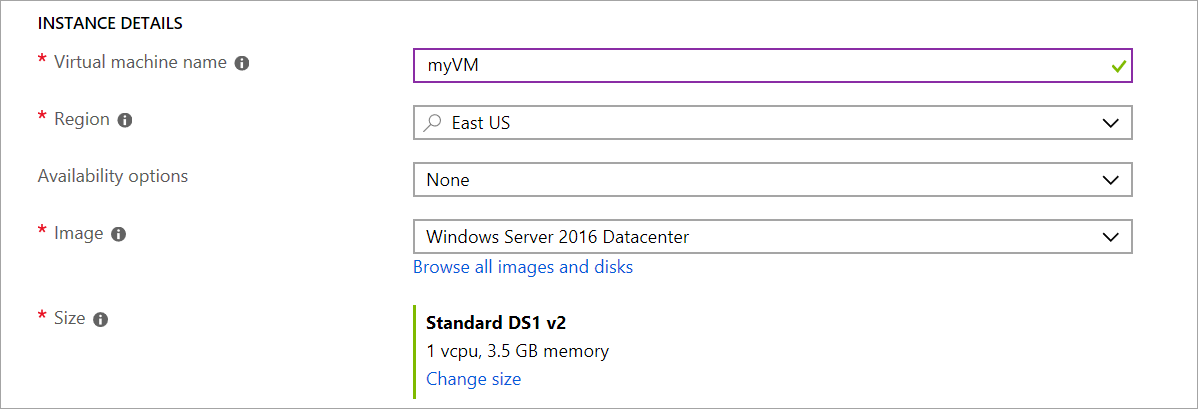
5. Under Instance details, type myVM for the Virtual machine name and choose East US for your Location. Leave the other defaults.
| 6. |
|---|
| ED | 110 | |
|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT |
|
|
| 11. Move to the Management tab, and under Monitoring turn Off Boot Diagnostics. This will eliminate | ||
| 12. Leave the remaining defaults and then select the Review + create button at the bottom of the page. | ||
|
||
| Create a remote desktop connection to the virtual machine. These directions tell you how to connect to | ||
| your VM from a Windows computer. On a Mac, you need to install an RDP client from the Mac App Store. | ||
|
||
| 4. In the Windows Security window, select More choices and then Use a different account. Type the | ||
|
||
| 5. You may receive a certificate warning during the sign-in process. Select Yes or Continue to create the | ||
|
||
|
||
|
✔️ When no longer needed, you can delete the resource group, virtual machine, and all related resourc-es. To do so, select the resource group for the virtual machine, select Delete, then confirm the name of the resource group to delete.
PowerShell - Example (Part 1)
2. Create the initial configuration for the virtual machine with New-AzVMConfig:
In this demonstration, we will create a virtual machine using PowerShell.
Create the virtual machine
# create a resource group
New-AzResourceGroup -Name myResourceGroup -Location EastUS# create the virtual machine
# when prompted, provide a username and password to be used as the logon credentials for the VM
New-AzVm `
-ResourceGroupName "myResourceGroup" `
-Name "myVM" `
-Location "East US" `
-VirtualNetworkName "myVnet" `
-SubnetName "mySubnet" `
-SecurityGroupName "myNetworkSecurityGroup" `
-PublicIpAddressName "myPublicIpAddress" `
-OpenPorts 80,33894. Notice this is a Windows machine in a new VNet and subnet.
5. Notice the command started the machine.
2. Create an RDP session from your local machine. Replace the IP address with the public IP address of your VM. This command runs from a cmd window.
| ED | 114 |
|
|
|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | |||
|
|||
|
|||
|
|||
|
|||
| ● | |||
| ● | |||
|
|||
|
|||
|
|||
|
|||
SSH is an encrypted connection protocol that allows secure sign-ins over unsecured connections. SSH is the default connection protocol for Linux VMs hosted in Azure. Although SSH itself provides an encrypt-ed connection, using passwords with SSH connections still leaves the VM vulnerable to brute-force attacks or guessing of passwords. A more secure and preferred method of connecting to a VM using SSH is by using a public-private key pair, also known as SSH keys.
● The public key is placed on your Linux VM, or any other service that you wish to use with public-key cryptography.
✔️ Azure currently requires at least a 2048-bit key length and the SSH-RSA format for public and private keys.
Demonstration - Connect to Linux Virtual Ma-chines
In this demonstration, we will create a Linux machine and access the machine with SSL.4. Click the Generate button.
5. Move your mouse around the blank area in the window to generate some randomness.
| Backup and Restore 117 |
|---|
Backup and Restore
Azure Site Recovery
● VMware Virtual Machine Replication. You can perform the replication of virtual machines by VMware to a secondary site that is also running VMware. You also can replicate to Azure.
● Physical Windows and Linux machines. You can replicate physical machines running either Windows or Linux to a secondary site or to Azure.
● Automatically replicate to Azure. Automate the orderly recovery of services in the event of a site outage at the primary datacenter. Automate the orderly recovery of services in the event of a site outage at the primary datacenter.
● Safeguard against outages of complex workloads. Protect applications in SQL Server, SharePoint, SAP, and Oracle.
| Backup and Restore 119 |
|---|
It's important to understand the difference between images and snapshots. With managed disks, you can take an image of a generalized VM that has been deallocated. This image includes all of the disks at-tached to the VM. You can use this image to create a VM, and it includes all of the disks.
● A snapshot is a copy of a disk at the point in time the snapshot is taken. It applies only to one disk. If you have a VM that has one disk (the OS disk), you can take a snapshot or an image of it and create a VM from either the snapshot or the image.
There are several methods for backing up virtual machines.
1. Enable backup for individual Azure VMs. When you enable backup, Azure Backup installs an extension to the Azure VM agent that's running on the VM. The agent backs up the entire VM.
| Backup and Restore 121 |
|---|
4. When you initiate a failover, the VMs are created in the target resource group, target virtual network, target subnet, and in the target availability set. During a failover, you can use any recovery point.
Recovery Services Vault VM Backup Options
| ED | 122 | |
|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | ||
|
||
|
||
| 1. Create a recovery services vault. To back up your files and folders, you need to create a Recovery | ||
|
||
|
||
|
||
|
||
|
||
|
Once you trigger the restore operation, the Backup service creates a job for tracking the restore opera-tion. The Backup service also creates and temporarily displays notifications, so you monitor how the backup is proceeding.
Azure Backup Server
● Backing up to MABS/DPM provides app-aware backups optimized for common apps such as SQL Server, Exchange, and SharePoint, in additional to file/folder/volume backups, and machine state backups (bare-metal, system state).
| Backup and Restore 125 |
|---|
| ED | 126 |
|
|
|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT |
|
||
|
|||
|
|||
| ● | |||
| ● |
|
||
|
|||
|
|||
|
|||
| Virtual machine extensions and features for Linux - https://docs.microsoft.com/en-us/azure/virtu- | |||
|
|||
|
|||
| Custom Script Extension (CSE) can be used to automatically launch and execute virtual machine cus- | |||
| tomization tasks post configuration. Your script extension may perform very simple tasks such as stop- | |||
|
|||
|
|||
Set-AzVmCustomScriptExtension -FileUri https://scriptstore.blob.core.
windows.net/scripts/Install_IIS.ps1 -Run "PowerShell.exe" -VmName vmName
● Failure events. Be sure to account for any errors that might occur when running your script. For example, running out of disk space, or security and access restrictions. What will the script do if there is an error?
● Sensitive data. Your extension may need sensitive information such as credentials, storage account names, and storage account access keys. How will you protect/encrypt this information?
In this example we are installing IIS on the localhost. The configuration will saved as a .ps1 file.
configuration IISInstall
Virtual Machine Extensions 129
Get-WindowsFeature -name Web-Server
Note: You could also use the PowerShell Set-AzVmCustomScriptExtension command to deploy the extension. You would need to upload the script to blob container and use the URI. We will do this in the next demonstration.
| ED | 130 | ||
|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | |||
|
|||
|
|||
| ● | Logical components of Azure VMs that run Windows and Linux: Are measured against pre-configured | ||
|
|||
| ● |
|
||
| ● | |||
|
|||
|
|||
|
|||
| ● |
|
||
| ● | |||
|
|||
|
|||
|
|||
|
|||
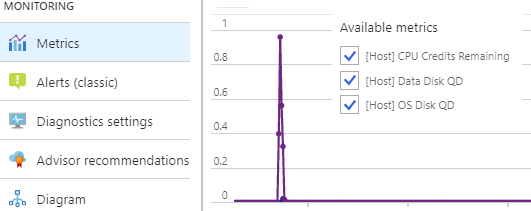
Monitoring Virtual Machines 131
Monitoring
✔️Take a few minutes to navigate the Overview page and the Monitoring section to see what is available for your virtual machine.
Online Lab - Implementing custom Azure VM images 133
Objectives
After completing this lab, you will be able to:● Install and configure HashiCorp Packer
Password: Pa55w.rd
Exercise 1: Installing and configuring HashiCorp Packer The main tasks for this exercise are as follows:
2. In the Azure portal, in the Microsoft Edge window, start a Bash session within the Cloud Shell.
3. If you are presented with the You have no storage mounted message, configure storage using the following settings:
| ED | 134 | ||
|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | ● | ||
| ● |
|
||
| ● |
|
||
|
|||
|
|||
|
|||
|
|||
| Result: After you completed this exercise, you have downloaded HashiCorp Packer and configured its | |||
|
|||
|
|||
|
|||
|
|||
TENANT_ID=$(echo $AAD_SP | jq .tenant | tr -d '"')
4. From the Cloud Shell pane, run the following to retrieve the value of the subscription ID and store it in a variable:
SUBSCRIPTION_ID=$(az account show --query id | tr -d '"')9. From the Cloud Shell pane, run the following to replace the placeholder for the value of the tenant_id parameter with the value of the $TENANT_ID variable in the Packer template:
sed -i.bak3 's/"$TENANT_ID"/"'"$TENANT_ID"'"/' ~/template03.json10. From the Cloud Shell pane, run the following to replace the placeholder for the value of the subscrip-tion_id parameter with the value of the $SUBSCRIPTION_ID variable in the Packer template: sed -i.bak4 's/"$SUBSCRIPTION_ID"/"'"$SUBSCRIPTION_ID"'"/' ~/template03.
3. Note: The build process might take about 10 minutes.
Result: After you completed this exercise, you have created a Packer template and used it to build a custom image.
| xargs -L1 bash -c 'az group delete --name $0 --no-wait --yes'
2. Close the Cloud Shell prompt at the bottom of the portal. Result: In this exercise, you removed the resources used in this lab.
| ED | 138 | |
|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | ||
|
||
|
||
|
||
|
||
|
||
| $nsgRuleRDP = New-AzureRmNetworkSecurityRuleConfig -Name myNetworkSecurityGroupRuleRDP | ||
|
||
|
||
|
||
|
||
| Set-AzureRmVMSourceImage -PublisherName MicrosoftWindowsServer -Offer WindowsServer -Skus | ||
|
||
|
||
|
||
You need to move a VM that supports an application to Azure.
What steps should you perform? Which configuration options should you consider?
You need to move the classic VMs to Azure Resource Groups to improve administration and delegation.
How can you move the VMs to resource groups? What restrictions are there to moving the VMS?
Azure Networking Components
A major incentive for adopting cloud solutions such as Azure is to enable information technology (IT) departments to move server resources to the cloud. This can save money and simplify operations by removing the need to maintain expensive datacenters with uninterruptible power supplies, generators, multiple fail-safes, clustered database servers, and so on. For small and medium-sized companies, which might not have the expertise to maintain their own robust infrastructure, moving to the cloud is particu-larly appealing.
| ED | 142 | |
|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | ||
|
||
|
||
|
Azure Virtual Networks 143
● Enable hybrid cloud scenarios. VNets give you the flexibility to support a range of hybrid cloud scenarios. You can securely connect cloud-based applications to any type of on-premises system such as mainframes and Unix systems.
For more information, you can see:
✔️ Always plan to use an address space that is not already in use in your organization, either on-premis-es or in other VNets. Even if you plan for a VNet to be cloud-only, you may want to make a VPN connec-tion to it later. If there is any overlap in address spaces at that point, you will have to reconfigure or recreate the VNet. The next lesson will focus on IP addressing.
For more information, you can see:
What is Azure Virtual Network - https://docs.microsoft.com/en-us/azure/virtual-network/virtu-al-networks-overview
Networking Limits - https://docs.microsoft.com/en-us/azure/azure-subscription-service-limits#net-working-limits-1
|
|
|---|
3. Leave the rest of the default settings and select Create.
4. Verify your virtual network was created.Create a virtual network using PowerShell
1. Create a virtual network. Use values as appropriate.
| ● |
|
|---|
The following limitations are applicable when using the multiple NIC feature:
Demonstration - Create VMs with Multiple NICs
In this demonstration, you will learn how to create and configure multiple NICs and then attach those NICs to a VM. You can replace example parameter names with your own values if you prefer.
1. Using az network vnet subnet create a subnet for the back-end traffic named mySubnetBackEnd:
az network vnet subnet create \
--resource-group myResourceGroup \
--vnet-name myVnet \
--name mySubnetBackEnd \
--address-prefix 10.0.2.0/24
| ED | 148 |
|
|
|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | |||
|
|||
|
|||
| ● | |||
|
|||
|
|||
|
|||
|
|||
Overview of IP Addressing
You can assign IP addresses to Azure resources to communicate with other Azure resources, your on-premises network, and the Internet. There are two types of IP addresses you can use in Azure. Virtual networks can contain both public and private IP address spaces.
A public IP address resource can be associated with virtual machine network interfaces, internet-facing load balancers, VPN gateways, and application gateways. Azure can provide an IP address (dynamic assignment) or you can assign the IP address (static assignment). The type of resource affects the assign-ment.
|
|||
|---|---|---|---|
|
|
||
| Front-end configuration | |||
|
|
||
| Front-end configuration |
|
Address SKUs
Review of IP Addressing 151
2. Notice in the IpConfigurations area there is a PrivateIPAddress and the PrivateIpAllocationMethod is static.
Remove a static private IP address
1. Review the output.
2. Notice in the IpConfigurations area, The PrivateIPAllocationMethod is now Dynamic.
Why use a service endpoint?
● Improved security for your Azure service resources. VNet private address space can be overlap- ping and so, cannot be used to uniquely identify traffic originating from your VNet. Service endpoints provide the ability to secure Azure service resources to your virtual network, by extending VNet identity to the service. Once service endpoints are enabled in your virtual network, you can secure Azure service resources to your virtual network by adding a virtual network rule to the resources. This provides improved security by fully removing public Internet access to resources, and allowing traffic only from your virtual network.
| ED | 152 | ||
|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | ● | ||
|
|||
| ● |
|
||
| forced-tunneling, without impacting service traffic. Learn more about user-defined routes and | |||
| ● | Simple to set up with less management overhead. You no longer need reserved, public IP address- | ||
|
|||
|
|||
|
|||
|
|||
|
|||
|
|||
| Azure Database for PostgreSQL server and MySQL. Generally available in Azure regions where data- | |||
|
|||
|
|||
| to allow access only from a specific subnet of virtual network (VNet). By enabling Service endpoint to | |||
| access Azure Cosmos DB on the subnet within a virtual network, the traffic from that subnet is sent to | |||
Azure Service Bus and Azure Event Hubs. Generally available in all Azure regions. The integration of Service Bus with Virtual Network (VNet) service endpoints enables secure access to messaging capabili-ties from workloads like virtual machines that are bound to virtual networks, with the network traffic path being secured on both ends.
Azure Data Lake Store Gen 1. Generally available in all Azure regions where ADLS Gen1 is available. This feature helps to secure your Data Lake Storage account from external threats.
✔️ It is important to test and ensure the service endpoint is limiting access as expected.
Demonstration - Service Endpoints
2. Within the Storage Account, create a file share, and upload a file.
3. For the Storage Account, use the Shared Access Signature blade to Generate SAS and connection string.
| Network Routing 155 |
|---|
Network Routing
Information about the system routes is recorded in a route table. A route table contains a set of rules, called routes, that specifies how packets should be routed in a virtual network. Route tables are associat-ed to subnets, and each packet leaving a subnet is handled based on the associated route table. Packets are matched to routes using the destination. The destination can be an IP address, a virtual network gateway, a virtual appliance, or the internet. If a matching route can't be found, then the packet is dropped.
For more information, you can see:
| ED | 156 | |
|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | ||
|
||
|
||
|
||
|
||
|
||
✔️ There is practice exercise that includes a complete set of steps for this scenario, including creating the virtual appliance and testing.
Create Route Table
Border gateway protocol - https://docs.microsoft.com/en-us/azure/virtual-network/virtual-net-works-udr-overview#border-gateway-protocol
Overview of BGP with Azure VPN Gateways - https://docs.microsoft.com/en-us/azure/vpn-gateway/ vpn-gateway-bgp-overview?toc=%2fazure%2fvirtual-network%2ftoc.json
| ED | 158 | |
|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | ||
|
||
|
||
|
||
|
||
|
||
|
||
|
|
|
Route priorities
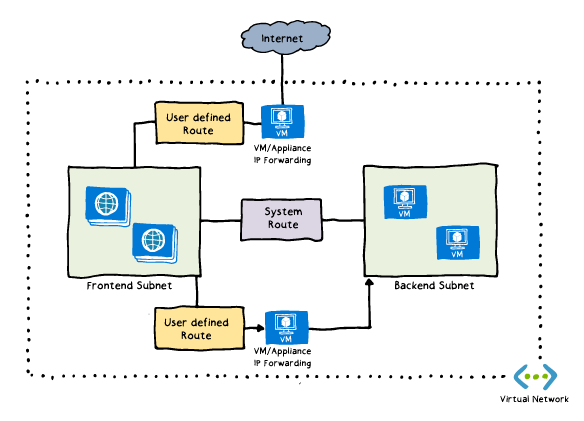
When the address prefixes are the same, Azure selects the route type, based on the following priority: 1. User-defined route
2. BGP route
3. System route
In our example, address 10.0.0.5, Azure selects the route with the User source, because user-defined routes are higher priority than system default routes.
Note: This demonstration requires a virtual network with at least one subnet.
Create a routing table
1. Access the Azure portal.
4. Select Create.
5. Wait for the new routing table to be deployed.
| Intersite Connectivity 161 |
|---|
VNet-to-VNet Connections
You can connect your VNets with a VNet-to-VNet VPN connection. Using this connection method, you create a VPN gateway in each virtual network. The VPN gateway can also be used to provide a connec-tion to an on-premises network. This is called a Site-to-Site (S2S) connection. In both cases a secure tunnel using IPsec/IKE provides the communication between the networks.
Regional multi-tier applications with isolation or administrative boundary
● Within the same region, you can set up multi-tier applications with multiple virtual networks connect- ed together due to isolation or administrative requirements.
VNet-to-VNet Connectivity - https://docs.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-howto-vnet-vnet-resource-manager-portal#vnet-to-vnet
Site-to-Site Connectivity - https://docs.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-how-to-site-to-site-resource-manager-portal
| ED | 162 | ||
|---|---|---|---|
|
|||
|
|||
| ● | |||
| ● |
|
||
| ● |
|
||
| ● | |||
|
|||
| ● |
|
||
|
|||
|
|||
| 2 | |||
Configuring Gateway Connections
Once your VPN gateways are created, you can create the connection between them. If your VNets are in the same subscription, you can use the portal.
For more information, you can see:
Configure the TestVNet1 gateway connection - https://docs.microsoft.com/en-us/azure/vpn-gate-way/vpn-gateway-howto-vnet-vnet-resource-manager-portal#TestVNet1Connection
| 3 |
|---|
| Intersite Connectivity 165 |
|---|
● Name and Gateway Type. Name your gateway and use the VPN Gateway type.
● VPN Type. Most VPN types are Route-based.
✔️ After the gateway is created, view the IP address that has been assigned to it by looking at the virtual network in the portal. The gateway should appear as a connected device. In this last step you will create a connection for the device.
VPN Types
● Policy-based VPNs. Policy-based VPNs encrypt and direct packets through IPsec tunnels based on the IPsec policies configured with the combinations of address prefixes between your on-premises
| ED | 166 |
|
||
|---|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | ||||
| ● | ||||
| ● |
|
|||
| ● |
|
|||
| ● | ||||
|
||||
|
||||
|
||||
| These connection limits are separate. For example, you can have 128 SSTP connections and also 250 | ||||
| ✔️ The Basic SKU is considered a legacy SKU. The Basic SKU has certain feature limitations. You can't | ||||
|
||||
|
||||
IP Address. The public IP address of the local gateway.
Address Space. One or more IP address ranges (in CIDR notation) that define your local network's address space. For example: 192.168.0.0/16. If you plan to use this local network gateway in a BGP-ena-bled connection, then the minimum prefix you need to declare is the host address of your BGP Peer IP address on your VPN device.
● A shared key. This is the same shared key that you will specify when creating the VPN connection (next step).
● The public IP address of your VPN gateway. When you created the VPN gateway you may have configured a new public IP address or used an existing IP address.
| 4 |
|---|
| Intersite Connectivity 169 |
|---|
PowerShell
To verify your connection with PowerShell, use the Get-AzVirtualNetworkGatewayConnection cmdlet. For example,Get-AzVirtualNetworkGatewayConnection -Name MyGWConnection -ResourceGroupN-ame MyRG
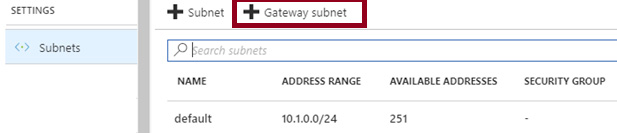
2. Select + Gateway subnet.
Notice the name of the subnet cannot be changed.
Perhaps the simplest and quickest way to connect your VNets is to use VNet peering. Virtual network peering enables you to seamlessly connect two Azure virtual networks6. Once peered, the virtual networks appear as one, for connectivity purposes. There are two types of VNet peering.
● Regional VNet peering connects Azure virtual networks in the same region.
● Performance. A low-latency, high-bandwidth connection between resources in different virtual networks.
● Communication. The ability for resources in one virtual network to communicate with resources in a different virtual network, once the virtual networks are peered.
Virtual network peering - https://docs.microsoft.com/en-us/azure/virtual-network/virtual-net-work-peering-overview
Configure VNet Peering
| 6 |
|---|
To deploy a gateway in your virtual network simply add a gateway subnet.
PowerShell Example - https://docs.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-peer-ing-gateway-transit?toc=%2fazure%2fvirtual-network%2ftoc.json#powershell-sample7
Hub and spoke - https://docs.microsoft.com/en-us/azure/architecture/reference-architectures/ hybrid-networking/hub-spoke
● Initiated. When you create the peering to the second virtual network from the first virtual network, the peering status is Initiated.
● Connected. When you create the peering from the second virtual network to the first virtual network, its peering status is Connected. If you view the peering status for the first virtual network, you see its status changed from Initiated to Connected.
| 7 |
|---|
User-defined routes and service chaining
Virtual network peering enables the next hop in a user-defined route to be the IP address of a virtual
| ED | 176 | |
|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT |
|
|
|
||
|
||
|
||
| You manage the Azure environment for your organization. You deploy a new application server virtual | ||
|
||
|
||
|
||
|
||
| You manage the Azure environment for your organization. You deploy a new server application virtual | ||
|
||
|
||
| al routes to a subnet's route table. In Azure, you create a route table, then associate the route table to | ||
|
Module 5 Module Managing Identities
Identity manage capabilities and integration
| ED | 180 | ||
|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | |||
|
|||
|
|||
|
|||
|
|||
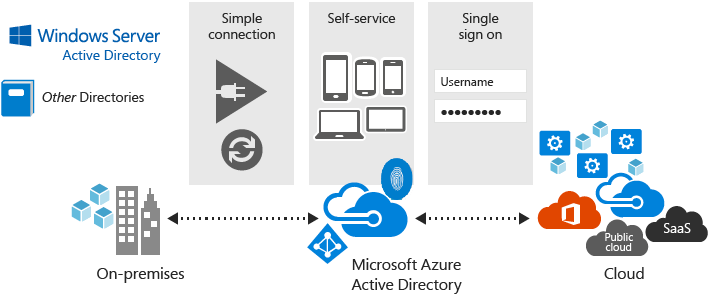
| ● | Single sign-on to any cloud or on-premises web app. Azure Active Directory provides secure single | ||
| ● | |||
|
|||
|
|||
| ● | |||
| ● |
|
||
|
|||
| ● | |||
|
|||
| ● | Reduce costs and enhance security with self-service capabilities. Delegate important tasks such as | ||
|
|||
✔️ What reasons do you have for considering Azure Active Directory?
Active Directory Domain Services (AD DS)
● Identity solution. Azure AD is primarily an identity solution, and it is designed for Internet-based applications by using HTTP and HTTPS communications.
● REST API Querying. Because Azure AD is HTTP/HTTPS based, it cannot be queried through LDAP. Instead, Azure AD uses the REST API over HTTP and HTTPS.
Choosing Between Azure AD and Azure AD DS
One of the main differences between Azure AD and Azure AD DS is the way devices are registered and joined.
|
|---|
Azure AD Directories (Tenants)
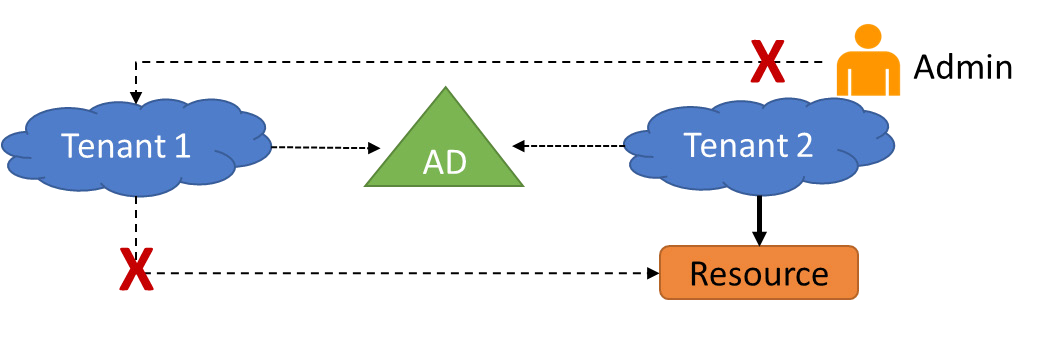
A tenant is a dedicated instance of an Azure AD directory which is created whenever you sign up for a Microsoft cloud service, such as Office 365 or Azure. It is important to note; a tenant is not the same as a subscription. A subscription is typically tied to a credit card for billing, where a tenant is an instance of Active Directory. You can have multiple tenants in your organization, such as Contoso1.com and Conto-so2.com .
| ED | 184 | ||
|---|---|---|---|
|
|||
| ● | If you create or delete a resource in one tenant, it has no impact on any resource in another tenant, | ||
| ● | |||
| ● |
|
||
|
|||
| ● | |||
| Synchronization independence. You can configure each Azure AD tenant independently to get data | |||
|
|||
| Azure AD provides many built-in roles2 to cover the most common security scenarios. To understand | |||
|
|||
| ● | |||
| ● | |||
| ● | |||
|
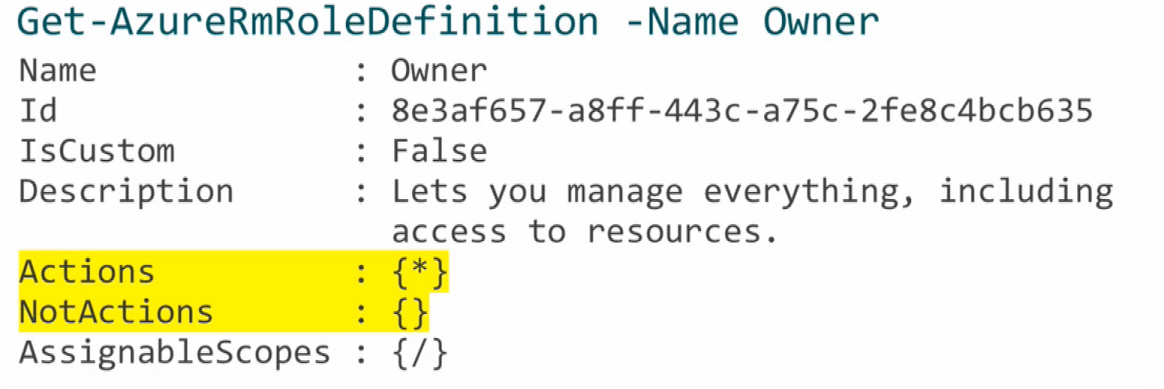
|||
| tion. It also includes the allowable permissions (Actions), denied permissions (NotActions), and scope | |||
|
|||
| For the Owner role that means all (*) actions, no denied actions, and all (/) scopes. This information is | |||
| 2 | |||
✔️ Take a minute to open the Azure Portal, open the Subscriptions or Resource Group blade, and click Access Control (IAM). Click Add and take a few minutes to review the built-in roles and see which role you would be most interested in using.
Role Definitions
Actions and NotActions
AssignableScopes
| ED | 186 | ||
|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | |||
|
|||
| ● |
|
||
| ● | |||
| ● | |||
|
|||
|
|||
|
|||
|
|||
|
|||
|
|||
|
|||
|
|||
| az role assignment create –role $roleName –assignee $assigneeName –re- | |||
#PowerShell
New-AzureRmRoleDefinition -InputFile .\sysops.json
To configure self-service password reset, you first determine who will be enabled to use self-service password reset. From your existing Azure AD tenant, on the Azure Portal under Azure Active Directory select Password reset.
In the Password reset properties there are three options: None, Selected, and All.
After enabling password reset for user and groups, you pick the number of authentication methods required to reset a password and the number of authentication methods available to users.
At least one authentication method is required to reset a password, but it is a good idea to have addi-tional methods available. You can choose from email notification, a text or code sent to user’s mobile or office phone, or a set of security questions.
1. On the Ready to configure page, select Configure and wait for the process to finish.
2. When you see the configuration finish, select Exit.
| ED | 190 | ||
|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | |||
|
|||
|
|||
| ● | Password hash synchronization. A sign-in method that synchronizes a hash of a users on-premises | ||
|
|||
| ● |
|
||
| ● | |||
| management capabilities such as certificate renewal and additional AD FS server deployments. | |||
| ● |
|
||
|
|||
| ● | |||
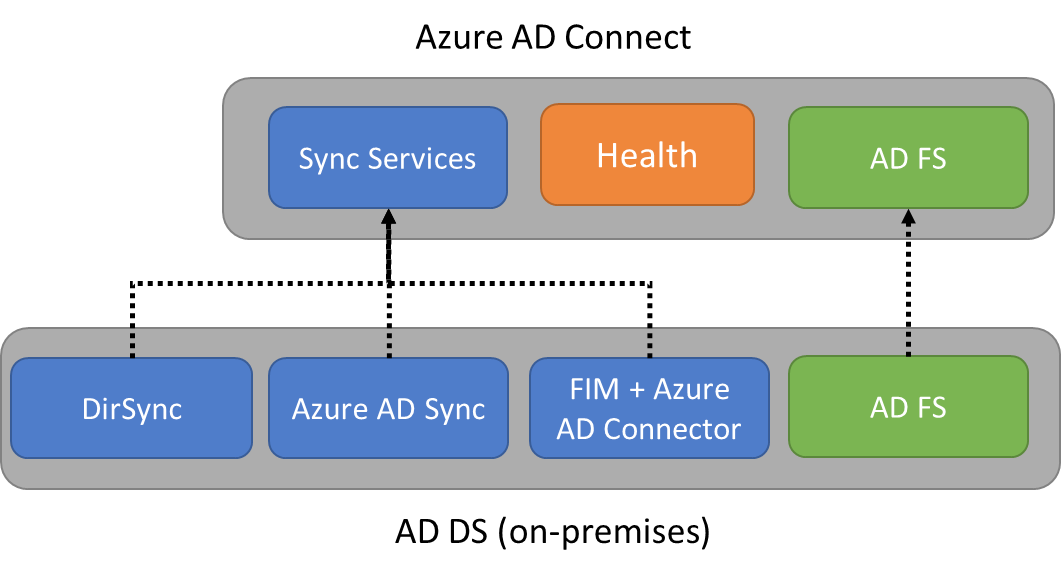
Sync Services. This component is responsible for creating users, groups, and other objects. It is also responsible for making sure identity information for your on-premises users and groups matches what’s in the cloud.
Authentication Options
Choosing an Azure AD Authentication method is important as it is one of the first important decisions when moving to the cloud as it will be the foundation of your cloud environment and is difficult to change at a later date.
Implementing and Managing Hybrid Identities 193
● Reduce your helpdesk costs.
How does this work?
Azure AD Pass-through Authentication (PTA) is an alternative to Azure AD Password Hash Synchroniza-tion, and provides the same benefit of cloud authentication to organizations. PTA allows users to sign in to both on-premises and cloud-based applications using the same user account and passwords. When users sign-in using Azure AD, Pass-through authentication validates the users’ passwords directly against an organizations on-premise Active Directory.
| ED | 194 |
|
|
|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | |||
| ● | Supports user sign-in into all web browser-based applications and into Microsoft Office client applica- | ||
| ● | |||
|
|||
| ● | Works seamlessly with conditional access features such as Multi-Factor Authentication to help secure | ||
|
|||
| ● | |||
| on-premises Active Directory and password protection by banning commonly used passwords. | |||
| ● | |||
| ● | |||
| ● |
|
||
| ● |
|
||
| ● | |||
| ● | |||
|
|||
|
|||
| directory where their users exist. How does Microsoft support keeping traditional on-premises Active | |||
|
|||
|
|||
● Zero-delay feedback. Password writeback is a synchronous operation. Your users are notified imme- diately if their password did not meet the policy or could not be reset or changed for any reason.
● Supports password changes from the access panel and Office 365. When federated or password hash synchronized users come to change their expired or non-expired passwords, those passwords are written back to your local Active Directory environment.
Federation is a collection of domains that have established trust. The level of trust may vary, but typically includes authentication and almost always includes authorization. A typical federation might include a number of organizations that have established trust for shared access to a set of resources.
Azure AD Connect Health
When you integrate your on-premises directories with Azure AD, your users are more productive because there's a common identity to access both cloud and on-premises resources. However, this integration creates the challenge of ensuring that this environment is healthy so that users can reliably access resources both on premises and in the cloud from any device.
With Azure AD Connect the key data you need is easily accessible. You can view and act on alerts, setup email notifications for critical alerts, and view performance data.
Azure Active Directory (Azure AD) enables single sign-on to devices, apps, and services from anywhere.
The proliferation of devices - including Bring Your Own Device (BYOD) – empowers end users to be productive wherever and whenever. But, IT administrators must ensure corporate assets are protected and that devices meet standards for security and compliance.
Online Lab - Implementing User-Assigned Managed Identities for Azure Resources 199
Objectives
After completing this lab, you will be able to:● Create and configure user-assigned managed identities
Exercise 1: Creating and configuring a user-assigned man-aged identity.
The main tasks for this exercise are as follows:
Task 1: Deploy an Azure VM running Windows Server 2016 Datacenter
1. From the lab virtual machine, start Microsoft Edge and browse to the Azure portal at http://portal.azure.com and sign in by using the Microsoft account that has the Owner role in the target Azure subscription.
| ED | 200 | ||
|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | |||
| ● |
|
||
| ● |
|
||
| ● | |||
| ● | |||
| ● | |||
|
|||
|
|||
| 6. From the Cloud Shell pane, upload the parameter file \allfiles\AZ-300T01\Module_05\azurede- | |||
|
|||
|
|||
|
|||
|
|||
| 2. From the Cloud Shell pane, run the following to assign the user-assigned managed identity to the | |||
|
|||
| 1. From the Cloud Shell pane, run the following to create a resource group (replace the <Azure re- | |||
|
|||
3. From the az3000502-LabRG - Access control (IAM) blade, assign the Owner role to the newly created user-assigned managed identity.
Result: After you completed this exercise, you have created and configured a user-assigned managed identity.
Task 1: Configure an Azure VM for authenticating via user-as-signed managed identity.
1. In the Azure portal, navigate to the az3000501-vm blade.
4. From the PowerShell prompt, run the following to install the latest version of the PowerShellGet module (press Enter if prompted for confirmation):
Install-Module -Name PowerShellGet -Force
Install-Module -Name PowerShellGet -AllowPrerelease
8. From the PowerShell prompt, run the following to install the the pre-release version of the AzureRM. ManagedServiceIdentity module:
Online Lab - Implementing User-Assigned Managed Identities for Azure Resources 203
3. Verify that the output contains only the resource groups you created in this lab. These groups will be
xargs -L1 bash -c 'az group delete --name $0 --no-wait --yes'
2. Close the Cloud Shell prompt at the bottom of the portal.
| ED | 204 | |
|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | ||
|
||
| You manage the Azure subscription for an organization. You migrate an on-premises service to Azure. | ||
|
||
|
||
|
||
|
||
|
||
| At least one authentication method is required to reset a password, but it is a good idea to have addi- | ||
|
||
|
||
| in parallel with an on-premises Active Directory Domain Services (AD DS) environment. You configure | ||
|
||
|
||
• Monitor and gain insights into AD FS servers, Azure AD Connect, and AD domain controllers.
• Monitor and gain insights into the synchronizations that occur between your on-premises AD DS and Azure AD.