Application select lab user task test the rbac role assignment
AZ-300T03
Understanding Cloud Architect Technology Solutions
Contents
| ■ | Module 0 Start Here . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | ||||||
|---|---|---|---|---|---|---|---|
| ■ | Welcome to Understanding Cloud Architect Technology Solutions . . . . . . . . . . . . . . . . . . . . . . . . . . . . | ||||||
| Module 1 Module Selecting Compute and Storage Solutions . . . . . . . . . . . . . . . . . . . . . . . . . . . | |||||||
| ■ | Design and Connectivity Patterns . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | ||||||
| Online Lab - Implementing Azure Storage Access Controls . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
|
||||||
| Review Question . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
|
||||||
| Module 2 Module Hybrid Networking . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | |||||||
| ■ | Hybrid Networking . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | ||||||
| . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | |||||||
| Review Question . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
|
||||||
| Module 3 Module Measure Throughput and Structure of Data Access . . . . . . . . . . . . . . . . . . . |
|
||||||
| ■ | Address Durability of Data and Caching . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | ||||||
| Measure Throughput and Structure of Data Access . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | |||||||
| Online Lab - Implementing Azure Load Balancer Standard . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | |||||||
| Review Question . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | |||||||
| Module 4 Module Implementing Authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
|
||||||
| ■ | Implementing authentication in applications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
|
|||||
| Implement multi-factor authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | |||||||
| Claims-based authorization . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | |||||||
| Role-based access control (RBAC) authorization . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | |||||||
| Implement OAuth2 authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | |||||||
| Implement managed identities for Azure resources . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
|
||||||
| Online Lab - Implementing Custom Role Based Access Control (RBAC) Roles . . . . . . . . . . . . . . . . . . . |
|
||||||
| Review Questions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | |||||||
| . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | |||||||
| ■ | Encryption options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | ||||||
|
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
|
|||||
| . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | |||||||
| Implement SSL and TLS communications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | |||||||
| Manage cryptographic keys in Azure Key Vault . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . | |||||||
| Review Questions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
|
||||||
|
. . . . . . . . . . . . . . . . . . . . . . . . . | ||||||
Welcome to Understanding Cloud Architect Technology Solutions
Course Overview: Understanding Cloud Architect Technol-ogy Solutions
| ED | 2 |
|
||
|---|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT |
|
|||
| ● | ||||
| ● | ||||
| ● |
|
|||
| ● |
|
|||
| ● | ||||
| ● |
|
|||
| ● |
|
|||
| ● | ||||
| ● | ||||
|
||||
|
||||
| ● | ||||
| ● | ||||
| ● | ||||
| ● | ||||
|
||||
|
||||
| ● | ||||
| ● | ||||
| ● |
|
|||
| ● |
|
|||
| This module contains the online lab Implementing Custom Role Based Access Control (RBAC) Roles. | ||||
| ● | ||||
| ● | ||||
Welcome to Understanding Cloud Architect Technology Solutions 3
What You’ll Learn:
Azure Architecture Center
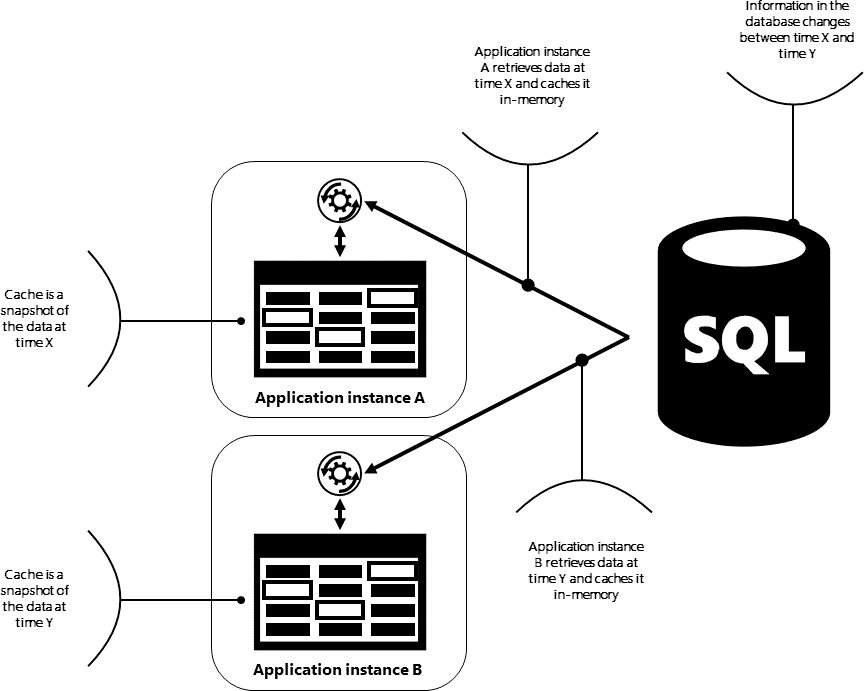
The cloud is changing the way applications are designed. Instead of being monoliths, applications are decomposed into smaller, decentralized services. These services communicate through APIs or by using asynchronous messaging or eventing. Applications scale horizontally, adding new instances as demand requires.
|
|
|---|
Other configuration options, such as affinity or stickiness, exist for load balancers. For example, stickiness allows you to determine whether a subsequent request from the same client machine should be routed to the same service instance. This might be required in scenarios where your application servers have a concept of state.
Transient fault handling
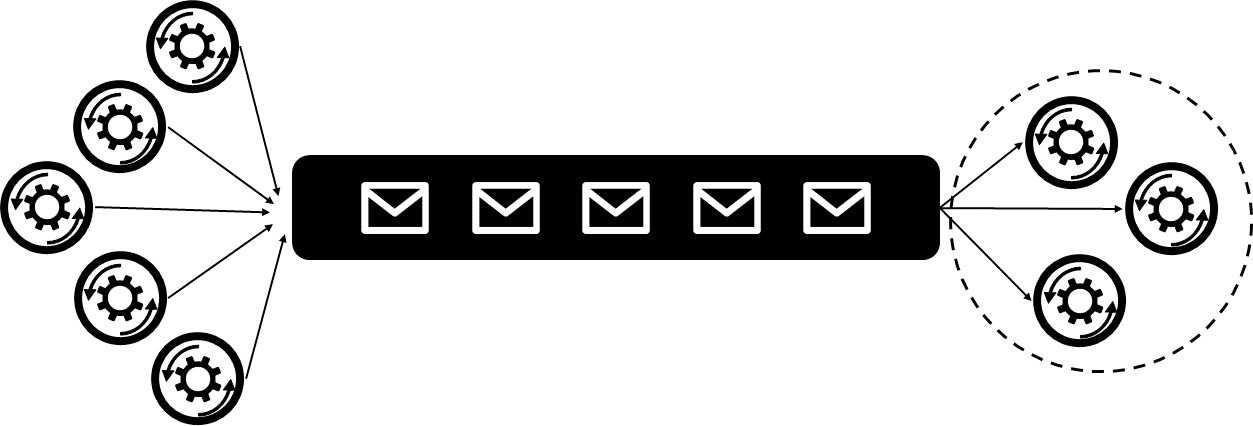
Queueing is both a mathematical theory and a messaging concept in computer science. In cloud applica-tions, queues are critical for managing requests between application modules in a manner such that they provide a degree of consistency regardless of the behavior of the modules.
An application might already have a direct connection to other application modules using direct method invocation, a two-way service, or any other streaming mechanism. If one of the application modules experiences a transient issue, this connection is severed and causes an immediate application failure. You can use a third-party queue to persist the requests beyond a temporary failure. Requests can also be audited independently of the primary application, because they are stored in the queue mechanism.
| ED | 8 | |
|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | ||
|
||
|
||
| to components and services, the temporary unavailability of a service, or timeouts that arise when a | ||
|
||
|
||
|
||
|
||
|
||
|
||
Problem: handling variable quantities of requests
A message queue can be used to implement the communication channel between the application and the instances of the consumer service. To handle fluctuating workloads, the system can run multiple instances of the consumer service. The application posts requests in the form of messages to the queue, and the consumer service instances receive messages from the queue and process them. This approach enables the same pool of consumer service instances to handle messages from any instance of the application.
Design and Connectivity Patterns 11
● Storage space. A data store for a large-scale cloud application may be expected to contain a huge volume of data that could increase significantly over time. A server typically provides only a finite amount of disk storage, but it may be possible to replace existing disks with larger ones or to add disks to a machine as data volumes grow. However, the system will eventually reach a hard limit whereby it is not possible to easily increase the storage capacity on a given server.
● Computing resources. A cloud application may be required to support a large number of concurrent users, each of whom runs queries that retrieve information from the data store. A single server hosting the data store may not be able to provide the necessary computing power to support this load, resulting in extended response times for users and frequent failures as applications attempting to store and retrieve data time out. It may be possible to add memory or upgrade processors, but the system will reach a limit when it is not possible to increase the compute resources any further.
| ED | 12 | |
|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT |
|
|
|
||
|
||
|
||
|
||
|
||
|
||
|
||
Lab Steps
Online Lab: Implementing Azure Storage access controls NOTE: For the most recent version of this online lab, see: https://github.com/MicrosoftLearning/ AZ-300-MicrosoftAzureArchitectTechnologies
1. Create a storage account in Azure
2. View the properties of the storage account
| ED | 14 | ||
|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | |||
|
|||
|
|||
| ● | |||
| ● | |||
| ● | |||
| ● |
|
||
|
|||
| ● | |||
| ● | |||
| ● | |||
| ● | |||
| ● |
|
||
| ● |
|
||
|
|||
|
|||
|
|||
|
|||
2. From the storage account blade, create a new blob container with the following settings:
2. Start Microsoft Edge and navigate to that URL.
3. Note the ResourceNotFound error message. This is expected since the blob is residing in a private container, which requires authenticated access.
| ED | 16 | ||
|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT |
|
||
|
|||
|
|||
| ● |
|
||
| ● | |||
| ● | |||
| ● | |||
|
|||
|
|||
| ● | |||
| ● | |||
| ● | |||
| ● |
|
||
| ● |
|
||
|
|||
|
|||
|
|||
|
|||
trast-white_scale-400.png' -Context $sasContext
11. Verify that you successfully accessed the blob.
12. Minimize the Cloud Shell pane.5. Verify that you no longer can access the blob.
Result: After you completed this exercise, you have created a blob container, uploaded a file into it, and tested access control by using a SAS token and a stored access policy.
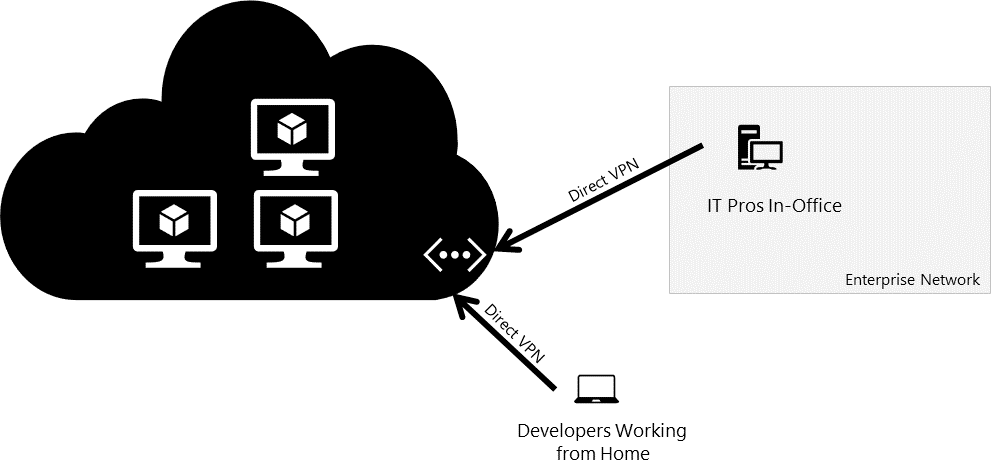
Module 2 Module Hybrid Networking
Hybrid Networking
| ED | 20 | |
|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT |
|
|
|
||
|
||
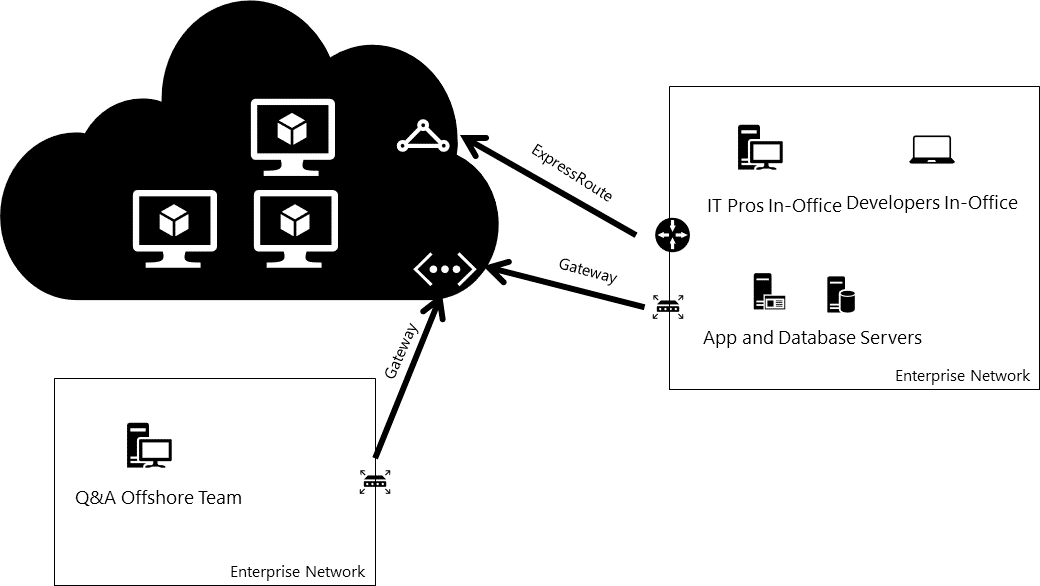
Combining ExpressRoute and site-to-site Con-nectivity
| ● |
|---|
| Hybrid Networking 23 |
|---|
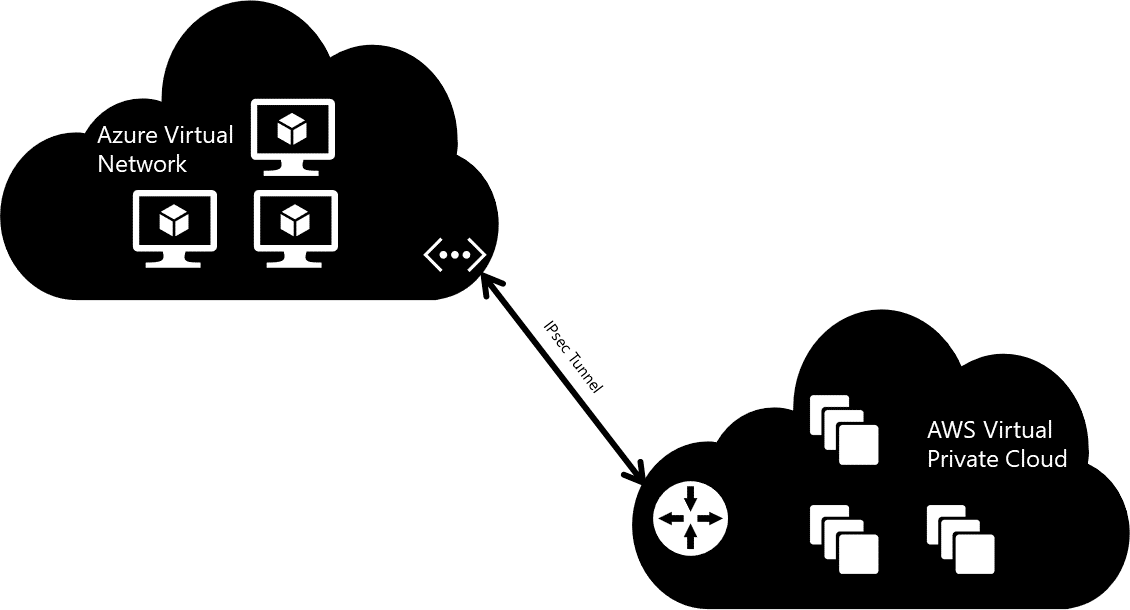
In AWS, you can create a virtual private cloud that provides network capabilities similar to those of a virtual network in Azure. An Amazon Elastic Compute Cloud (EC2) instance with Openswan (VPN soft-ware) can then be created for VPN functionality. After those instances are running, you simply create a gateway on the Azure virtual network side using static routing. The gateway IP address from Azure is then used to configure Openswan for a tunnel connection between the two virtual networks.
Virtual Network-to-Network 25
| ED | 26 | |
|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | ||
|
||
|
||
|
||
|
||
| can then be accessed by an off-shore development team, without exposing internal resources to the | ||
|
Module 3 Module Measure Throughput and Structure of Data Access
● Atomic: A transaction must execute exactly once and must be atomic, meaning all work completes or none of it does. Operations within a transaction usually share a common intent and are interdepend- ent. By performing only a subset of these operations, the system could compromise the overall intent of the transaction. Atomicity eliminates the chance of processing only a subset of operations.
● Consistent: A transaction must preserve the consistency of data, transforming one consistent state of data into another consistent state of data. Typically, the application developer is responsible for maintaining consistency.
Address Durability of Data and Caching 29
| ED | 30 | ||
|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | |||
|
|||
|
|||
| ● |
|
||
| ● |
|
||
| and the larger the number of users that need to access this data, the greater the benefits of caching | |||
|
|||
|
|||
|
|||
|
|||
Alternatively, a cache can be partially or fully populated with data in advance, typically when the applica-tion starts (an approach known as seeding). However, it might not be advisable to implement seeding for a large cache because this approach can impose a sudden, high load on the original data store when the application starts running. Caching typically works well with data that is immutable or that changes infrequently.
Manage data expiration in a cache
Redis Cache is an open-source not only SQL (NoSQL) storage mechanism that is implemented in the key-value pair pattern common among other NoSQL stores. Redis Cache is unique because it allows com-plex data structures for its keys.
Azure Redis Cache is a managed service based on Redis Cache that provides you secure nodes as a service. There are only two tiers for this service currently available:
For example, if your application uses 20 database units today, 40 database units will guarantee you approximately double your performance, while 10 database units will guarantee you half of your perfor-mance.
Let’s look at a few examples of normalized units in Azure and examine how you can use them to compare database service tiers.
| ED | 34 |
|
|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | ||
| and fixed price. All service tiers provide flexibility of changing performance levels without downtime. | ||
Measure Throughput and Structure of Data Access 35
A request unit is a normalized measure of request processing cost. A single request unit represents the processing capacity that’s required to read, via self-link or ID, a single item that is 1 kilobyte (KB) and that consists of 10 unique property values (excluding system properties). A request to create (insert), replace, or delete the same item consumes more processing from the service and thereby requires more request units.
| ● |
|---|
A non-relational database doesn’t use the tabular schema of rows and columns that most traditional database systems use. Rather, non-relational databases utilize an optimized storage model that is based on specific requirements of the type of data it’s story. For example, a non-relational database might store date as simple key/value pairs, as JSON documents, or as a graph consisting of edges and vertices.
What all of these data stores have in common is that they don't use a relational model. Also, they tend to be more specific in the type of data they support and how you can query that data. For example, time series data stores are optimized for queries over time-based sequences of data, while graph data stores are optimized for exploring weighted relationships between entities. Neither format would generalize well to the task of managing transactional data.
| ● |
|---|
Online Lab - Implementing Azure Load Balancer Standard 41
Task 1: Deploy Azure VMs in an availability set by using an Azure Resource Manager template
● Cloud Shell region: the name of the Azure region that is available in your subscription and which is closest to the lab location
● Resource group: the name of a new resource group az3000800-LabRG
5. From the Cloud Shell pane, upload the Azure Resource Manager template \allfiles\AZ-300T03\ Module_03\azuredeploy0801.json into the home directory.
6. From the Cloud Shell pane, upload the parameter file \allfiles\AZ-300T03\Module_03\azurede- ploy0801.parameters.json into the home directory.
9. In the Azure portal, close the Cloud Shell pane.
Task 2: Create an instance of Azure Load Balancer Standard
| ● |
|---|
14. Note: Wait for the operation to complete. This should not take more than 1 minute.
● Name: az3000801-vm0-RDP
● Frontend IP address: select the public IP address assigned to the LoadBalancedFrontEnd from the
5. Back on the az3000801-lb - Inbound NAT rules blade, click + Add.
6. On the Add inbound NAT rule blade, specify the following settings and click OK:
| ED | 44 |
|
|
|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | ● |
|
|
| ● | |||
| ● | |||
| ● | |||
| ● | |||
| ● |
|
||
| ● |
|
||
| ● | |||
|
|||
|
|||
| 4. On the lab computer, right-click Start, click Run, and, from the Open text box, run the following | |||
|
|||
| ● |
|
||
| ● | |||
| (replace the <IP address> placeholder with the IP address you identified earlier in this task): | |||
|
|||
|
|||
| ● | |||
| ● | |||
| 10. Within the Remote Desktop session, start a Windows PowerShell session and run the following to | |||
|
|||
Online Lab - Implementing Azure Load Balancer Standard 45
Exercise 2: Configure outbound SNAT traffic by using Az-ure Load Balancer Standard
The main tasks for this exercise are as follows:
1. Deploy Azure VMs into an existing virtual network by using an Azure Resource Manager template 2. Create an Azure Standard Load Balancer and configure outbound SNAT rules
3. Test outbound rules of Azure Standard Load BalancerTask 1: Deploy Azure VMs into an existing virtual network by using an Azure Resource Manager template
1. From the lab virtual machine, start Microsoft Edge and browse to the Azure portal at http://portal.5. From the Cloud Shell pane, deploy a pair of Azure VMs hosting Windows Server 2016 Datacenter by running:
az group deployment create --resource-group az3000801-LabRG --template-file azuredeploy0802.json --parameters @azuredeploy0802.parameters.json
Online Lab - Implementing Azure Load Balancer Standard 47
Task 3: Verify that the outbound rule took effect
● User name: Student
● Password: Pa55w.rd1234
| ED | 48 |
|
|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT |
|
|
|
||
|
||
| tion. You can create a new Azure Redis Cache instance by using the Azure portal, Azure CLI, or Azure | ||
Implementing authentication in applications
Certificate-based authentication
Certificate-based authentication can be useful in scenarios where your organization has multiple front-end applications communicating with back-end services. Traditionally, the certificates are installed on each server, and the machines trust each other after validating certificates. This same traditional structure can be used for infrastructure in Azure.
With cloud-native applications, you can use certificates to help secure connections in hybrid scenarios. For example, you can restrict access to your Azure web app by enabling different types of authentication for it. One way to do so is to authenticate using a client certificate when the request is over Transport Layer Security (TLS) / Secure Sockets Layer (SSL). This mechanism is called TLS mutual authentication or
| ED | 50 | |
|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | ||
|
||
| governance, and application access management. Azure AD quickly enables single sign-on (SSO) to | ||
|
||
|
||
| If you are already familiar with AD DS, first introduced with Windows 2000 Server, then you probably | ||
|
||
|
||
|
||
| authentication. Windows Server Active Directory enables organizational units (OUs) and Group Policy | ||
|
Azure AD Connect integrates on-premises directories with Azure AD. This allows you to provide a common identity for enterprise users in Office 365, Azure, and software as a service (SaaS) applications.
Azure AD Connect is made up of three primary components: the synchronization services, the optional Active Directory Federation Services (AD FS) component, and the monitoring component named Azure AD Connect Health.
Forms authentication uses an HTML form to send the user's credentials to the server. It is not an internet standard. Forms authentication is appropriate only for web APIs that are called from a web application so that the user can interact with the HTML form. Forms authentication does have a few disadvantages, including:
● It requires a browser client to use the HTML form.
2. If the user is not authenticated, the server returns HTTP 302 (Found) and redirects to a login page.
3. The user enters credentials and submits the form.
| 6. |
|---|
Implementing authentication in applications 55
|
|
|---|
Implement multi-factor authentication 57
|
|
|---|---|
|
|
|
|
It can be used either as a second verification method or as a replacement for a password when using phone sign-in. The Authenticator app fully supports both the Verification code and Notification methods of verification in MFA. The Authenticator app is available for Windows phone, Android, and iOS.
Implementing custom multi-factor authentication using .NET
Claim-based authorization checks are declarative—the developer embeds them within their code, against a controller or an action within a controller, specifying claims that the current user must possess and optionally the value the claim must hold to access the requested resource. Claims requirements are policy based; the developer must build and register a policy expressing the claims requirements.
Claims-based authorization in Microsoft ASP.NET
[Authorize(Policy = "EmployeeOnly")]
public IActionResult VacationBalance()
{
return View();
}Alternatively, the AuthorizeAttribute attribute can be applied to an entire controller; in this instance, only identities matching the policy will be allowed access to any action on the controller:
| ED | 60 | |
|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | ||
|
||
|
||
|
||
|
||
| Most claims come with a value. You can specify a list of allowed values when creating the policy. The | ||
|
||
|
||
| policy.RequireClaim("EmployeeNumber", "1", "2", | ||
|
||
|
||
Role-based authorization is an authorization approach in which user permissions are managed and enforced by an application based on user roles. If a user has a role that is required to perform an action, access is granted; otherwise, access is denied. When an identity is created, it may belong to one or more roles. For example, Holly may belong to the Administrator and User roles, whereas Adam may belong only to the User role. How these roles are created and managed depends on the backing store of the authorization process.
Role-Based authorization in ASP.NET
[Authorize(Roles = "HRManager,Finance")]
public class SalaryController : Controller
{
}This controller would be accessible only by users who are members of the HRManager role or the Finance role.
}
If you want to specify multiple allowed roles in a requirement, you can specify them as parameters to the RequireRole method:
Note: You can mix and match both claims-based authorization and role-based authorization. Is it typical to see the role defined as a special claim. The role claim type is expressed using the following URI: http://schemas.microsoft.com/ws/2008/06/identity/claims/role.
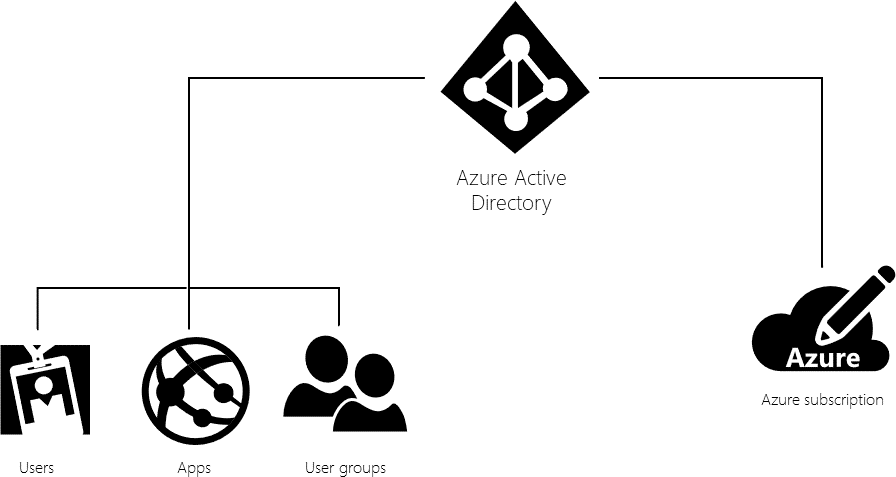
Role-based access control (RBAC)
| ED | 64 |
|
||
|---|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT |
|
|||
| to understand — it’s how permissions are enforced. A role assignment consists of three elements: a | ||||
| ● | ||||
| ● | ||||
|
||||
| ● | A group is a set of users created in Azure Active Directory. When you assign a role to a group, all | |||
|
||||
| ● | ||||
| ● | ||||
|
||||
|
||||
| ● | ||||
|
||||
|
||||
|
||||
|
||||
RBAC in Azure includes over 70 built-in roles. There are four fundamental RBAC roles. The first three apply to all resource types:
The rest of the built-in roles allow the management of specific Azure resources. For example, the Virtual Machine Contributor role allows the user to create and manage virtual machines.
| ED | 66 | |||
|---|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | ||||
|
||||
|
||||
| standard methods to provide identity information. OpenID Connect implements authentication as an | ||||
|
||||
|
||||
| ● | ||||
| ● | ||||
|
||||
|
||||
| ● | ||||
| ● | ||||
| ● | ||||
|
||||
| ● | --For Web Applications, provide the Sign-On URL, which is the base URL of your app, where users can | |||
|
||||
| ● | ||||
| ● | ||||
| ● |
|
|||
|
||||
OpenID Connect metadata document
OpenID Connect describes a metadata document that contains most of the information required for an app to perform sign-in. This includes information such as the URLs to use and the location of the service's public signing keys. The OpenID Connect metadata document can be found at:
|
|
|
|
A space-separated list of scopes. |
|
|
|
| ED | 70 | |
|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT |
Sample response
A sample response, after the user has authenticated, could look like this:
|
|
POST / HTTP/1.1
Host: localhost:12345
Content-Type: application/x-www-form-urlencodederror=access_denied&error_description=the+user+canceled+the+authentication
Implement OAuth2 authentication 73
Validate the id_token
● Ensuring the user has proper authorization/privileges
● Ensuring a certain strength of authentication has occurred, such as multi-factor authentication.
GET https://login.microsoftonline.com/common/oauth2/logout?
post_logout_redirect_uri=http%3A%2F%2Flocalhost%2Fmyapp%2F
|
Single sign-out
Implement OAuth2 authentication 75
|
|
|---|---|
|
|
|
Host: localhost
Content-Type: application/x-www-form-urlencoded
The OAuth2 implicit grant is notorious for being the grant with the longest list of security concerns in the OAuth2 specification. And yet, that is the approach implemented by ADAL JS and the one we recommend when writing SPA applications. What gives? It’s all a matter of tradeoffs: and as it turns out, the implicit grant is the best approach you can pursue for applications that consume a Web API via JavaScript from a browser.
What is the OAuth2 implicit grant?
| ED | 76 | ||
|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | |||
|
|||
|
|||
| token (and id_token, when using OpenId Connect) directly from the authorization endpoint, without | |||
| contacting the token endpoint nor authenticating the client. This variant was designed for JavaScript | |||
|
|||
|
|||
|
|||
|
|||
| Access: when you select a message from your inbox, only the message visualization panel changes to | |||
| or SPAs. The idea is that these applications only serve an initial HTML page and associated JavaScript, | |||
|
|||
|
|||
|
|||
|
|||
| tion. The implicit flow provides a convenient mechanism for JavaScript applications to obtain access | |||
|
|||
| ● | Tokens can be reliably obtained without any need for cross origin calls – mandatory registration of the | ||
|
|||
| ● | |||
| ● | |||
| ● |
|
||
Implement OAuth2 authentication 77
The implicit grant presents more risks than other grants. However, the higher risk profile is largely due to the fact that it is meant to enable applications that execute active code, served by a remote resource to a browser. If you are planning an SPA architecture, have no backend components or intend to invoke a Web API via JavaScript, use of the implicit flow for token acquisition is recommended.
If your application is a native client, the implicit flow isn’t a great fit. The absence of the Azure AD session cookie in the context of a native client deprives your application from the means of maintaining a long lived session. Which means your application will repeatedly prompt the user when obtaining access tokens for new resources.
|
||
|---|---|---|
|
||
|
|
|
|
|
|
| ED | 80 | |
|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT |
Implement OAuth2 authentication 81
| ED | 82 |
|
|||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT |
|
||||||||||
|
|||||||||||
|
|||||||||||
|
|||||||||||
|
|||||||||||
|
|||||||||||
|
|||||||||||
error=access_denied
&error_description=the+user+canceled+the+authentication
|
|
|---|---|
|
|
|
|
||
|---|---|---|
|
||
|
|
|
|
|
|
|
|
| ED | 86 | |
|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | ||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
| ED | 88 | |||||||
|---|---|---|---|---|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT |
|
|||||||
| The token issuance endpoint errors are HTTP error codes, because the client calls the token issuance | ||||||||
|
||||||||
|
||||||||
|
||||||||
|
||||||||
|
||||||||
|
||||||||
|
||
|---|---|---|
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
Use the access token to access the resource
Now that you've successfully acquired an access_token, you can use the token in requests to Web APIs, by including it in the Authorization header.
| ED | 90 | |
|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | ||
|
||
|
||
|
||
|
||
|
||
|
||
| Secured resources that implement RFC 6750 issue HTTP status codes. If the request does not include | ||
|
||
|
||
|
||
|
||
Implement OAuth2 authentication 91
A sample request to the tenant-specific endpoint (you can also use the common endpoint) to get a new access token using a refresh token looks like this:
// Line breaks for legibility only
|
|
|
|
|
|
|
microsoft.com/mail.read was not found in the tenant named 295e01fc-0c56-4ac3-ac57-5d0ed568f872. This can happen if the application has not been installed by the administrator of the tenant or consented to by any user in the tenant. You might have sent your authentication request to the wrong tenant.\r\nTrace ID: ef1f89f6-a14f-49de-9868-61bd4072f0a9\r\nCorrelation ID: b6908274-2c58-4e91-aea9-1f6b9c99347c\r\nTimestamp: 2016-04-11
18:59:01Z",
"error_codes": [
50001
],
"timestamp": "2016-04-11 18:59:01Z",
"trace_id": "ef1f89f6-a14f-49de-9868-61bd4072f0a9",
"correlation_id": "b6908274-2c58-4e91-aea9-1f6b9c99347c"
}
|
|
|
|---|---|---|
|
|
|
|
|
| ED | 96 | |
|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT |
|
|
|
||
| the client_secret parameter is replaced by two parameters: a client_assertion_type and | ||
Example
The following HTTP POST requests an access token for the https://service.contoso.com/ web service with a certificate. The client_id identifies the web service that requests the access token.
| ED | 98 |
|
|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT |
|
|
|
||
|
||
| i1CWRjJghORC1B1-fah_yWx6Cjuf4QE8xJcu-ZHX0pVZNPX22PHYV5Km-vPTq2HtIqd- | ||
|
||
|
||
Implement managed identities for Azure re-sources
Managed identities for Azure resources over-view
Note: Managed identities for Azure resources is the new name for the service formerly known as Man-aged Service Identity (MSI).
Terminology
How the managed identities for Azure resources works
There are two types of managed identities:
| ED | 100 | |||
|---|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | it's enabled on. If the instance is deleted, Azure automatically cleans up the credentials and the | |||
| ● |
|
|||
|
||||
|
||||
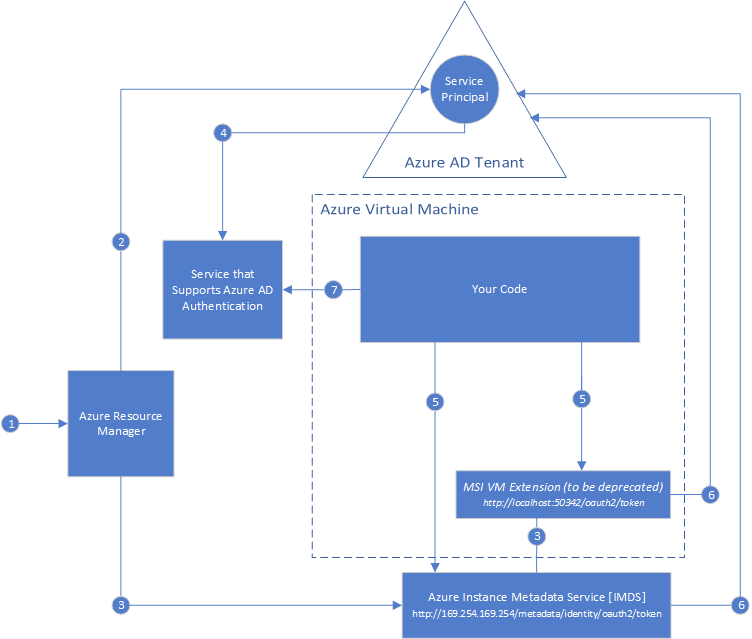
| The following diagram shows how managed service identities work with Azure virtual machines (VMs): | ||||
| 1. Azure Resource Manager receives a request to enable the system-assigned managed identity on a | ||||
|
||||
| ● | Updates the Azure Instance Metadata Service identity endpoint with the service principal client ID | |||
|
||||
5. Your code that's running on the VM can request a token from two endpoints that are accessible only from within the VM:
● Azure Instance Metadata Service identity endpoint (recommended):
oauth2/token
● The resource parameter specifies the service to which the token is sent. To authenticate to Azure Resource Manager, use resource=https://management.azure.com/.
2. Azure Resource Manager creates a service principal in Azure AD for the user-assigned managed identity. The service principal is created in the Azure AD tenant that's trusted by the subscription.
3. Azure Resource Manager receives a request to configure the user-assigned managed identity on a VM:
| ED | 102 |
|
||
|---|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT |
|
|||
| ● | ||||
| ● | ||||
| Azure Resource Manager, use resource=https://management.azure.com/. | ||||
| ● |
|
|||
|
||||
| ● | ||||
| ● | VM extension endpoint (planned for deprecation in January 2019): http://localhost:50342/ | |||
| ● | ||||
| Azure Resource Manager, use resource=https://management.azure.com/. | ||||
| ● |
|
|||
|
||||
| 7. A call is made to Azure AD to request an access token (as specified in step 5) by using the client ID | ||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
2016datacenter --generate-ssh-keys --assign-identity --admin-username
azureuser --admin-password myPassword12
To disable system-assigned managed identity on a VM, your account needs the Virtual Machine Contrib-utor role assignment. No additional Azure AD directory role assignments are required.
If you have a Virtual Machine that no longer needs the system-assigned identity, but still needs user-as-signed identities, use the following command:
To remove the managed identity for Azure resources VM extension (planned for deprecation in January 2019), user -n ManagedIdentityExtensionForWindows or -n ManagedIdentityExtension-ForLinux switch (depending on the type of VM):
az vm identity --resource-group myResourceGroup --vm-name myVm -n Manage-
1. Create a user-assigned identity using az identity create. The -g parameter specifies the resource group where the user-assigned identity is created, and the -n parameter specifies its name. Be sure to replace the <RESOURCE GROUP> and <USER ASSIGNED IDENTITY NAME> parameter values with your own values:
az identity create -g <RESOURCE GROUP> -n <USER ASSIGNED IDENTITY NAME>
Remove a user-assigned managed identity from an Azure VM
To remove a user-assigned identity to a VM, your account needs the Virtual Machine Contributor role assignment.
| ED | 106 | |
|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | ||
|
||
|
||
|
||
|
||
| az vm update -n myVM -g myResourceGroup --set identity.type='SystemAs- | ||
|
||
|
||
| accessing a given resource. The token is based on the managed identities for Azure resources service | ||
| The fundamental interface for acquiring an access token is based on REST, making it accessible to any | ||
|
||
| programming model, except the client uses an endpoint on the virtual machine (vs an Azure AD end- | ||
|
||
Implement managed identities for Azure resources 107
|
|
|---|---|
|
|
|
|---|---|---|
|
|
|
|
||
|---|---|---|---|
|
|
||
| Required metadata header not specified |
| ED | 110 |
|
|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT |
For retry, we recommend the following strategy:
After you've enabled managed identity on an Azure resource, such as an Azure virtual machine:
1. If you're using the Azure CLI in a local console, first sign in to Azure using az login. Use an account that is associated with the Azure subscription under which you would like to deploy the VM:
spID=$(az resource list -n DevTestVMSS --query [*].identity.principalId
--out tsv)
| ED | 112 | |
|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | ||
|
Online Lab - Implementing Custom Role Based Access Control (RBAC) Roles 113
Objectives
After completing this lab, you will be able to:
Exercise 1: Define a custom RBAC role The main tasks for this exercise are as follows:
1. Deploy an Azure VM by using an Azure Resource Manager template
| ED | 114 | ||
|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | |||
|
|||
|
|||
| ● |
|
||
| ● |
|
||
| ● | |||
| ● | |||
| ● | |||
|
|||
|
|||
| 6. From the Cloud Shell pane, upload the parameter file \allfiles\AZ-300T03\Module_04\azurede- | |||
|
|||
|
|||
|
|||
|
|||
Online Lab - Implementing Custom Role Based Access Control (RBAC) Roles 115
5. On the Owner blade, click Permissions.
1. On the lab computer, open the file \allfiles\AZ-300T03\Module_04\customRoleDefinition09.json and review its content:
{
"Name": "Virtual Machine Operator (Custom)",
"Id": null,
"IsCustom": true,
"Description": "Allows to start and stop (deallocate) Azure VMs", "Actions": [
"Microsoft.Compute/*/read",
"Microsoft.Compute/virtualMachines/deallocate/action",
"Microsoft.Compute/virtualMachines/start/action"
],
"NotActions": [
],
"AssignableScopes": [
"/subscriptions/SUBSCRIPTION_ID"
]
}5. From the Cloud Shell pane, run the following to create the custom role definition:
New-AzRoleDefinition -InputFile $HOME/customRoleDefinition09.json
|
|---|
Task 3: Test the RBAC role assignment
1. Start a new in-private Microsoft Edge window, browse to the Azure portal at http://portal.azure.com and sign in by using the newly created user account:5. Stop the virtual machine and verify that the action completed successfully.
Result: After you completed this exercise, you have assigned and tested a custom RBAC role
| Review Questions 119 |
|---|
Suggested Answer ↓
In security best practices, it is recommended to use two or more factors when authenticating users. This practice is referred to as multi-factor authentication. Using an enterprise as an example, the company could require employees to scan their badges and then enter their passwords as two factors of authenti-cation. In the world of security, it is often recommended to have two of the following factors:
Encryption
Encryption is the process of translating plain text data (plaintext) into something that appears to be random and meaningless (ciphertext). Decryption is the process of converting ciphertext back to plain-text. To encrypt more than a small amount of data, symmetric encryption is used. A symmetric key is used during both the encryption and the decryption process. To decrypt a particular piece of ciphertext, the key that was used to encrypt the data must be used.
| Encryption options 123 |
|---|
encryption. All Azure Storage services enable server-side encryption by default using service-managed keys, which is transparent to the application.
Storage Service Encryption is enabled for all new and existing storage accounts and cannot be disabled. Because your data is security enhanced by default, you don't need to modify your code or applications to take advantage of Storage Service Encryption.
Implement Azure confidential computing 125
Note: In some online articles, TEEs are commonly referred to as enclaves.
● Frameworks – The Microsoft Research team has developer frameworks, such as the Confidential Consortium Blockchain Framework, to help jumpstart new projects that need to run in TEEs.
| ED | 126 |
|
|
|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | |||
|
|||
|
|||
| ● | |||
| ● | |||
| ● | |||
| ● | |||
| ● |
|
||
|
|||
| SSL 1.0, 2.0 and 3.0 have been found to be vulnerable, and they have been prohibited by an Internet | |||
|
|||
|
|||
|
|||
|
|||
|
|||
Manage cryptographic keys in Azure Key Vault 127
Key Vault streamlines the key management process and enables you to maintain control of keys that access and encrypt your data. Developers can create keys for development and testing in minutes and then seamlessly migrate them to production keys. Security administrators can grant (and revoke) permis-sion to keys as needed.
Accessing Key Vault in Azure CLI
az keyvault create --name contosovault --resource-group SecurityGroup
--location westus
At this point, your Azure account is the only one authorized to perform any operations on this new vault.
az keyvault secret show --vault-name contosovault --name DatabasePassword
| ED | 128 |
|
|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | ||
|
||
|
||
|
||
| protect sensitive data at rest on the server, during movement between client and server, and while the | ||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
Business Continuity and Resilience in Azure
NOTE: The content in this module serves as an informal checklist of considerations for sustaining busi-ness continuity and resilience in Azure and is the result of real-world implementations.
| ED | 132 |
|
|
|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT |
|
||
| ● | High availability (HA) is the ability of the application to continue running in a healthy state despite | ||
| ● | Disaster recovery (DR) is the ability to recover from major incidents, such as service disruption that | ||
|
|||
|
|||
| For example, an order processing application might be considered operational if a customer is able to | |||
|
|||
|
|||
| Data backup is a critical part of DR. If the stateless components of an application fail, you can always | |||
|
|||
|
|||
Resiliency Checklist
Use the following checklist to incorporate resiliency requirements into your application throughout its lifecycle.
Identify the expected and the actual Service Level Agreements. In Azure, a Service Level Agreement (SLA) describes Microsoft’s commitments to maintain uptime and connectivity. If the SLA for a particular service is 99.9%, it means you should expect the service to be available 99.9% of the time. The Azure SLAs also include provisions for obtaining a service credit if the SLA is not met, along with specific definitions of "availability" for each service. That aspect of the SLA acts as an enforcement policy.
You should identify the expected target SLAs for each workload in your solution. An SLA makes it possi-ble to evaluate whether the architecture meets the business requirements. For example, if a workload requires 99.99% uptime, but depends on a service with a 99.9% SLA, that service cannot be a single-point of failure in the system. One remedy is to have a fallback path in case the service fails, or take other measures to recover from a failure of that service.
|
|
||
|---|---|---|---|
|
|||
|
|||
|
|
||
|
|||
|
| Application Design 135 |
|---|
Failure Mode Analysis (FMA)
Perform a failure mode analysis (FMA) for your application. FMA is a process for building resiliency into an application early in the design stage. The goals of an FMA include:
Avoid any single point of failure. All components, services, resources, and compute instances should be deployed as multiple instances to prevent a single point of failure from affecting availability. This includes authentication mechanisms. Design the application to be configurable to use multiple instances, and to automatically detect failures and redirect requests to non-failed instances where the platform does not do this automatically.
Azure has a number of features to make an application redundant at every level of failure, from an individual VM to an entire region.
| Application Design 137 |
|---|
● Create and track orders.
● View recommendations.
Enhancing Security
Enhancing security
| Application Design 139 |
|---|
Additional Considerations for Testing, Deployment, and Maintenance
Have a rollback plan for deployment. It's possible that your application deployment could fail and cause your application to become unavailable. Design a rollback process to go back to a last known good version and minimize downtime.
Run tests in production using both synthetic and real user data. Test and production are rarely identical, so it's important to use blue/green or a canary deployment and test your application in produc-tion. This allows you to test your application in production under real load and ensure it will function as expected when fully deployed.
Establish a process for interacting with Azure support. If the process for contacting Azure support is not set before the need to contact support arises, downtime will be prolonged as the support process is navigated for the first time. Include the process for contacting support and escalating issues as part of your application's resiliency from the outset.
| ED | 142 | |
|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | ||
Replicating Data
Data Management
● For VMs, do not rely on RA-GRS replication to restore the VM disks (VHD files). Instead, use Azure Backup. In addition, consider using managed disks. Managed disks provide enhanced resiliency for VMs in an availability set, because the disks are sufficiently isolated from each other to avoid single points of failure. In addition, managed disks eliminate the need to account for the storage account-level IOPS limits.
Additional Data Management Considerations
| ED | 144 |
|
|
|---|---|---|---|
| MCT USE ONLY. STUDENT USE PROHIBIT | ● | Periodic backup and point-in-time restore. Regularly and automatically back up data and verify | |
|
|||
| ● | Ensure that no single user account has access to both production and backup data. Your data | ||
|
|||
|
|||
| ● | |||
|
|||
Monitoring and Disaster Recovery 145
Measure remote call statistics and make the information available to the application team. If you don't track and report remote call statistics in real time and provide an easy way to review this informa-tion, the operations team will not have an instantaneous view into the health of your application. And if you only measure average remote call time, you will not have enough information to reveal issues in the services. Summarize remote call metrics such as latency, throughput, and errors in the 99 and 95 percen-tiles. Perform statistical analysis on the metrics to uncover errors that occur within each percentile.
Track the number of transient exceptions and retries over an appropriate timeframe. If you don't track and monitor transient exceptions and retry attempts over time, it's possible that an issue or failure could be hidden by your application's retry logic.
● Log events at service boundaries. Include a correlation ID that flows across service boundaries. If a transaction flows through multiple services and one of them fails, the correlation ID will help you pinpoint why the transaction failed.
● Use semantic logging, also known as structured logging. Unstructured logs make it hard to automate the consumption and analysis of the log data, which is needed at cloud scale.