Detective controls – will not prevent errors from occurring but rather they alert those using the system to error and anomalies
StuDocu is not sponsored or endorsed by any college or university
ACCG 2 5 0 : ACCO U N TI N G SYSTEM S D ESI G N & D EV EL O PM EN T
Today Every Company is a Technology Company
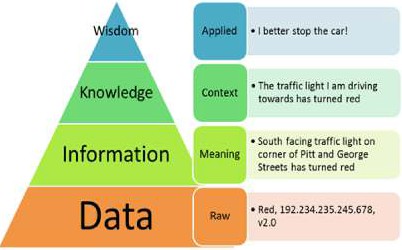
Definitions
|
|
|---|---|
Why should I learn about IS?
Reason 1: Benefits of becoming and informed user
BENEFITS OF BECOMING AN INFORMED USER:
Benefit from organisation’s IT application – you can understand what is behind those applications
Can play a key role in managing the organisation’s IS
Can use IT to start your own business
Reason 2: IT offers Career Opportunities
Business Analyst
Systems Programmer
Reason 3: IT/Information can offer a Competitive Advantage
Overview of Computer-Based Systems
 Computer-based Information
Systems
Computer-based Information
Systems
Hardware – devices accept, process and display data and info
Software – program(s) enable hardware to process data
Major Capabilities of Information Systems
Performs speedy, high-volume calculations
 Provide fast, communication
and collaboration among organisations
Provide fast, communication
and collaboration among organisations
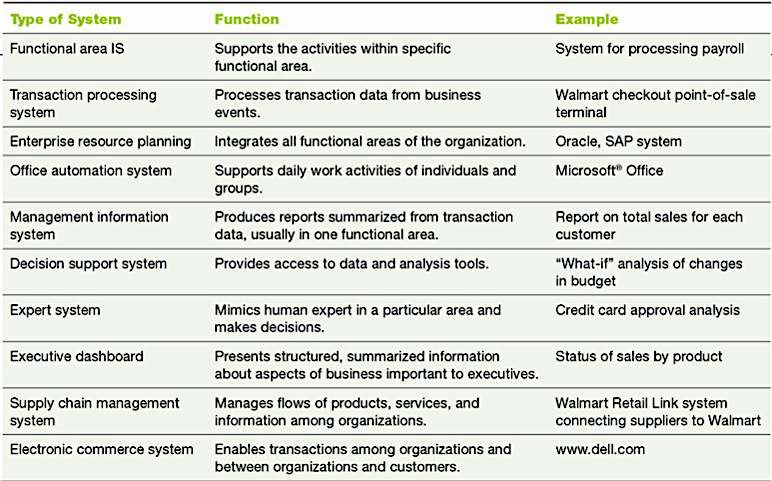
Types of Organisational Information Systems Evolution of AIS
How Does IT Impact Organisations?
IT Reduces the Number of Middle Managers
IT makes managers more productive more people report to one manager Reduces number of middle managers (Fewer promotional opportunities)
IT Changes the Manager’s Job
Will IT Eliminate Jobs?
HOWEVER
IT creates new jobs that requires employees with IT knowledge and skills, e.g. medical record keeping
IT Impacts Employees at Work
|
Ergonomics: science of designing machines and work settings that minimise injury and illness
Importance of Information Systems to Society
IT affects the quality of our life. Here are the positive and negative, societal effects of the increased use of IT:
Business Processes
Business Process = INPUTS + RESOURCES + OUTPUTS
Effective (customer satisfied) and Efficient (less wastage of resources) Business Processes Competitive Advantage
Information Systems & Business Processes
Allows easy exchange of and access to data across processes
IS plays a vital role in 3 areas:
|
|
BP Improvement, BP Reengineering & BP Management
Business Process Reengineering
Popularity grew due to unique capabilities of IT, e.g. automation of process steps
Business Process Improvement
Five basic phases of BPI:
CONTROL – establishes process metrics and monitors the improved process after solution is implemented
SIX SIGMA (Popular methodology for BPI Initiatives)
Six Sigma: goal is to ensure that the process has no more than 3.4 defects per million outputs

|
|||
|---|---|---|---|
|
|||
BPM Decreases costs Increases revenue Improve Org. Flexibility
Business Pressures, Organisational Responses & IT Support
MARKET PRESSURES
Powerful Customers (customers can use the Internet to learn about p/s)
TECHNOLOGY PRESSURES
Technological innovation & obsolescence (e.g. BYOD)
Information overload
Compliance with government regulations
Ethical issues
Organisations are responding to various business pressures by implementing IT such as:
STRATEGIC SYSTEMS helps increase market share, better negotiate with suppliers, prevent new competitors
Competitive Advantage & Strategic IS
Information Systems + Managing Business Processes Efficiently Competitive Advantage
∆ Competitive advantage is essential for your organisation’s survival
∆ Becoming knowledgeable about strategy and how IS can affect strategy and competitive position will help you throughout your career
Porter’s Five Forces Model
Threat of new entrants – new organisations entering an industry create increased competition for the existing participants
Using the 5 forces model, an organisation can analyse its industry to identify opportunities and threats and then develop tactic for these situations.
Porter’s Value Chain Model
Outbound Logistics – delivering finished product to a customer, invoicing, order handling, finishing goods
Marketing and Sales – promotion of product, sales analysis, market research
Product and technology development (R&D) – product and process design production engineering
Procurement and technology – finding vendors, negotiating prices, new techniques and methods Value system: all value chains (supplier’s value chain, business’ value chain, distributor’s value chain) – firm must understand all components of the value system
Strategies for Competitive Advantage
Operational effectiveness – I can do the same thing more efficiently than you can (improving the manner in which a firm executes its internal business processes to perform these activities more effectively than rivals)
Customer-oriented – I treat my customers better than you do
Business-IT Alignment
6 Characteristics of Excellent Business-IT Alignment
Organizations ensure that IT employees understand how the company makes (or loses) money
Organizations create a vibrant and inclusive company culture
Solution: Adopt process perspective of the organisation
Functional Perspective of an Organisation
Functional perspective: one person doing one task, each department on its own

Process Perspective of an Organisation
Process perspective: all departments must communicate to proceed with all stages of the business process
|
|
|---|---|
|
Functional Perspective vs. Process Perspective
TPS helps prevent errors such as overlapping updates and can be used to reverse transactions.
Functional Area Information Systems
A functional area information system supports a functional area by increasing the area’s internal efficiency and effectiveness. Activities supported by FAIS include:
|
|
|
|
Enterprise Resource Planning (ERP) Systems
Historically Functional Area IS developed independently information silos lack of communication & integration
|
|
ERP systems will help an organisation improve its process design when:
The existing process is flawed and the strategy of the organisation is consistent with the ERP approach.
Gather and document current business processes integrate all processes and find the best way of performing those processes, i.e. best practice
Benefits & Limitations of ERP Systems
x Failure to involve affected employees into planning & development phases
x Trying to do too much too fast in conversion process
Implementing ERP Systems
Vanilla approach – implement standard ERP package with little adaptation to org’s business processes
Custom approach – customised ERP system by developing new ERP functions designed specifically for that firm
SOFTWARE-AS-A-SERVICE IMPLEMENTATION
Disadvantages: not necessarily more secure than on-premise systems, companies have a lack of control over system, problems with the system are fixed by the vendor and therefore are not fixed quickly enough
ENTERPRISE APPLICATION INTEGRATION
Used in place of ERP when process of converting from existing system is considered too tiring.
What can go wrong?
Delay in the receipts of products or a delay in a shipment
The system tracks all of the events that occur within each process
The system stores all the documents created in a centralised database that is readily available when needed
Reports
Exception reports – include only information that falls outside certain thresholds (management creates performance standards and then identifies exceptions to this performance standard), e.g. report that shows sales that fell short of the set quota
CHAPTER 4: CUSTOMER RELATIONSHIP MANAGEMENT & SUPPLY CHAIN MANAGEMENT
Defining Customer Relationship Management
CRM helps build a long term, sustainable relationship with customers that brings value to the org
Organisational Goal: to maximise number of high-value repeat customers and minimise customer churn Minor increase in customer satisfaction major increase in company’s overall value
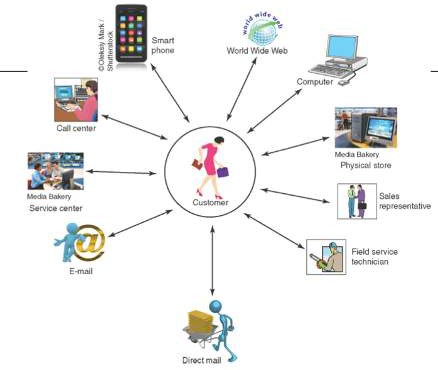
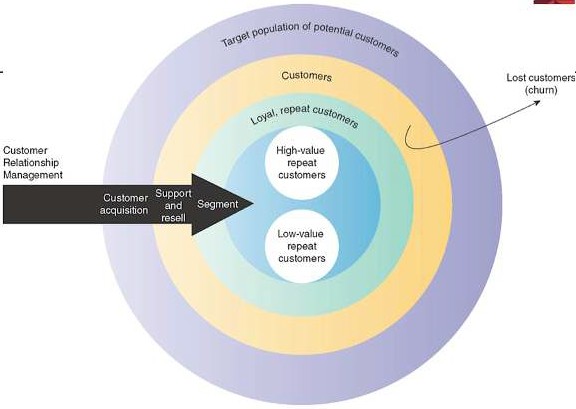 Customer Touch Points
Customer Touch Points
Traditional customer touch points – telephone contact, direct mailings, actual physical interactions
Organisational CRM has created new touch points – email, websites, communication via smartphones
Data Consolidation
Operational Customer Relationship Management Systems
A 360-degree view of each customer
The ability of sales and service employee to access a complete history of customer interaction with the organisation, regardless of the touch point
Two Major Components
Contact management system (list of all contacts with customers)
Sales lead tracking system (list of potential customers)
Marketing – CRM applications can sift through customer data – data mining – to develop purchasing profile
Cross Selling – marketing additional related products to customers, e.g. selling camera and showing accessories
Search and Comparison Capabilities
Technical and Other Information and Services, e.g. websites with downloadable product manuals
Customised Products and Services
Personalised Web Pages
FAQs
Analytical Customer Relationship Management Systems
Other types of Customer Relationship Management Systems
On-Demand CRM Systems
∆ Hosted by external vendor in the vendor’s data centre, organisations rent CRM systems from vendors
∆ Pros – Cheaper, less effort, quicker
Mobile CRM Systems
Open Source CRM Systems
∆ Pros – favourable pricing, easy to customise
∆ Cons – risks involving quality control
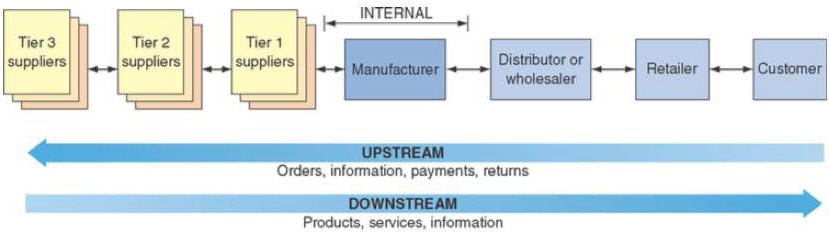
Supply Chains
Structure and Components of Supply Chains
Select suppliers, develop pricing, delivery, payment processes between company and suppliers
Internal – processes
Managers coordinate receipt of orders, develop network of data warehouses, select carrier to deliver products and develop invoicing systems to receive payments from customers
Supply Chain Management
Five Basic Components of Supply Chain Management
DELIVER (Logistics) – Managers coordinate receipt of orders, develop network of data warehouses, select carrier to deliver products and develop invoicing systems to receive payments from customers
RETURN – SC managers must create flexible network for receiving defective, returned or excess products from their customers
Compress the cycle time involves in fulfilling business transactions
Eliminate paper processing and its associated inefficiencies and costs
The Push Model vs. the Pull Model
PULL MODEL (make-to-order) – companies make only what the customer wants
Closely aligned with mass customisation, e.g. Dell laptops
Problems along the Supply Chain
|
|
||
|---|---|---|---|
Solutions to Supply Chain Problems
Information Sharing – along the supply chain
Vendor-managed inventory – when supplier manages the entire inventory process for product(s)
Information technology Support for Supply Chain Management
Definition Internal Control
Why Internal Control systems?
Provides reasonable assurance
Reliability of financial reporting
Internal Control Systems
Internal Control System Objectives
Safeguard assets
Check accuracy and reliability of accounting data
COSO Internal Control – Integrated Framework
COSO Cube 1992 – What makes up Internal Control
Control environment
It is all about top management. If management is asking you to do things that should not be done, then there is no hope for the organisation because it is always top management that makes the big decisions about the firm.
∆ Method of organizing and developing employees
Risk Assessment
Control Activities
» Policies and procedures to protect company assets based on risk assessment e.g. CCTV, gates that beep
To follow the path of data recorded in transaction from the initial source document to final disposition of data on a report or from the report back to the source document
Purpose of Audit Trail
Some controls:
Vacations can be good to uncover fraud while the fraudulent employee is away
SEPARATION OF DUTIES
Good internal controls demand that no single employee be given too much responsibility. An employee should never be in a position to perpetrate and conceal fraud and unintentional errors.
Inventory Controls
Stored in a safe location with limited access, e.g. locks
Use fireproof safes or rented storage vaults offsite
Cash control
Good audit trail of cash disbursements is essential to avoid errors or irregularities
REVIEWS OF OPERATING PERFORMANCE
Duties of Internal Auditors
Operational audits of each department or subsystem in the organisation
Regular reviews of internal control systems
Inform employees about controls
Managers must inform employees about their roles and responsibilities in regards to the control systems
Initiate corrective action when necessary Monitor to see if these controls are effective
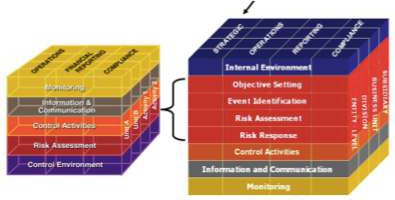 2004 COSO
ERM (Enterprise Risk Management) Framework
2004 COSO
ERM (Enterprise Risk Management) Framework
Modified version of COSO cube that includes 3 other components – total of nine.
Objective Setting
Risks tied to what we want to achieve. What are some of the risks around what we want to achieve?, e.g. we want zero injuries in the month, what are some of the risks that will not allow us to achieve this objective
Operations – day-to-day efficiency, performance, and profitability
Event identification & Risk Response
∆ Analyze risks
∆ Implement cost-effective countermeasures
2012 COBIT, Version 5
Meet stakeholders needs
Cover enterprise end-to-end
Identify the source of risks
Determine the impact of risks

Types of Controls
Preventive Controls – are designed to stop errors or irregularities from occurring
Preventing errors and fraud is far more cost-effective than detecting and correcting problems after they occur
IT access authorizations to ensure access is appropriate
The use of passwords to stop unauthorised access to systems/applications
Detective Controls – will not prevent errors from occurring but rather they alert those using the system to error and anomalies
Review your payroll receipts
Compare transactions on reports to source documents
Corrective Controls – designed to correct an error or irregularity after it has occurred
Submit corrective journal entries after discovering an error
Complete changes to IT access lists if individual’s roles changes
Evaluating Controls
Cost Benefit Analysis
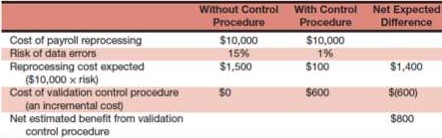
Only the controls whose benefits > costs are implemented. Another alternative is to measure the expected annual loss:
Risk Matrix
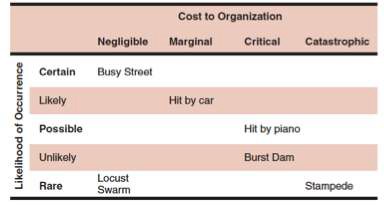
TOPIC 5: REVENUE CYCLE
Strategic Implications of the Revenue Cycle
WHY IS THE REVENUE CYCLE SO IMPORTANT?
The level of sales drives all other activity levels within the organisation
Retail sell product to customer, record sale, collect cash, update inventory
Manufacturer/distributor sell product to other companies, deliver goods, bill customers at a later date, collect payment
Revenue Process Activities (revenue cycle steps)
|
|
|
|
|
|||
|
|
|

10 Source Documents
∆ Credit application – form prepared by new customer applying for credit, shows they financial position
∆ Sales order – formal document prepared using customer order form, multiple copies made for shipment and payments received by customers
∆ Remittance advice – shows cash receipt from customer, outlines nature of payment by customer to accounting or finance unit
∆ Customer service log – used by customer service personnel to record customer enquiries and actions taken to address customer concerns
Technologies Underpinning the Revenue Cycle
CRM (Customer Relationship Management) – improves understanding of customers and their interaction with the organisation (store historical revenue data arranged by customer data mining, trend analysis)
Barcode scanning – reduces error levels by automating data input, scanned data immediately uploaded
Data and Decisions in the Revenue Cycle
Accounts Receivable data (details of payments received, invoices created, cash receipts data)
Sales data (contains details of each sale made)
|
|
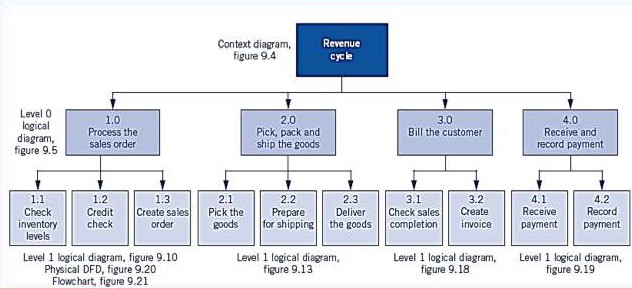
 Revenue Cycle
Documentation
Revenue Cycle
Documentation
|
||||
|---|---|---|---|---|
|
||||
|
||||
|
|
|||
|
||||
|
||||
|
||||
|
|
|||
|
|
|
||
|
||||
|
||||
|
|
Hash totals: a total that is similar to a batch total but the number that is added has no meaning by itself, e.g. a hash total of customer numbers
5.6 Measuring Revenue Cycle Performance
How to make sure the revenue cycle is achieving its set objectives. To monitor performance a range of metrics need to be employed along with some realistic targets.
Purchasing Phase – Objective is to procure the right goods at the right amount and to receive those goods at the right time
Do this by ensuring approved and authorised purchases, getting goods from authorised suppliers, recording all purchase commitments accurately, accepting goods that meet quality and delivery specification
Strategic Implications of the Expenditure Cycle
A well controlled expenditure cycle can provide a competitive advantage by acting to contain costs or by providing high quality products and services which in turn translates to an opportunity for higher product pricing
Failure to correctly manage purchasing can lead to systematic problems that impact revenue and production
Expenditure Process Activities
Source Documents
∆ Vendor List – list of authorised vendors that offer quality goods and services at reasonable prices (part of organisational database)
∆ Purchase Invoice – details and amounts due and payment terms and conditions (prepared by vendor)
Technologies Underpinning the Expenditure Cycle
ERP (Enterprise Resource Planning) – integrated software that records and manages many different types of transactions within a single integrated database, e.g. SAP, Oracle
Improves the integration of enterprise-wide data
EDI is a system or method for exchanging business documents (integrating data from documents into internal systems) with external entities
Without EDI – lost revenue, lost reputation, lost opportunities
E.g. RFID tags used to keep track of pets and livestock (cattle)
SCM (Supply Chain Management) – Improves the planning and execution of orders through supplier and customer integration and detailed supply chain analytics
Data and Decisions in the Expenditure Cycle
|
|
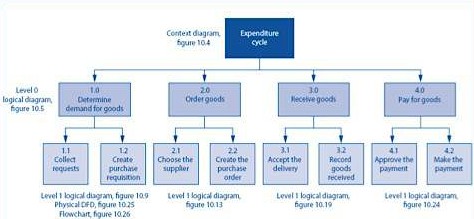 Expenditure Cycle Documentation
Expenditure Cycle DocumentationExpenditure Cycle Activities & Related Risks and Controls

|
|
|
||
|
|
|||
|
|
|
||
|
||||
|
|
|||
|
||||
|
|
|||
|
||||
|
||||
|
|
|||
|
|
|||
|
Measuring Expenditure Cycle Performance
A range of metrics (measure used for a specific purpose) are used to monitor performance against expenditure cycle objectives. Examples of metrics or KPIs for the expenditure cycle objectives include:
|
|
|
|
|
TOPIC 7: HR MANAGEMENT & PAYROLL CYCLE
HR Management Phase – employee recruitment, performance management, management of employee termination
Objective: recruit right people, ensure they are performing at the right standard and manage staff exits in the right manner
Strategic Implications of the HR Management & Payroll Cycle
In order to survive, organisations must not only attract high-performing individuals, but also retain their services for as long as required
HR Management & Payroll Cycle Process Activities (EPPE)
Source Documents
∆ Termination letter – states the terms (date, payout, etc.) of termination of employment
∆ Employee performance review – employers use this form to review an employee’s job performance
Technologies Underpinning the HR Management & Payroll Cycle
Links relevant areas of the organisation, e.g. revenue, production and general ledger
Integrates enterprise-wide data
Online banking facilities improve transparent and reconciliation of transactions – less cash handling
Data and the HR Management & Payroll Cycle
A range of data produced and consumed by activities within the HR management and payroll cycle.
Job vacancies
Current period production cycle data
Accounts payable data
HR Management & Payroll Cycle Business Decisions
|
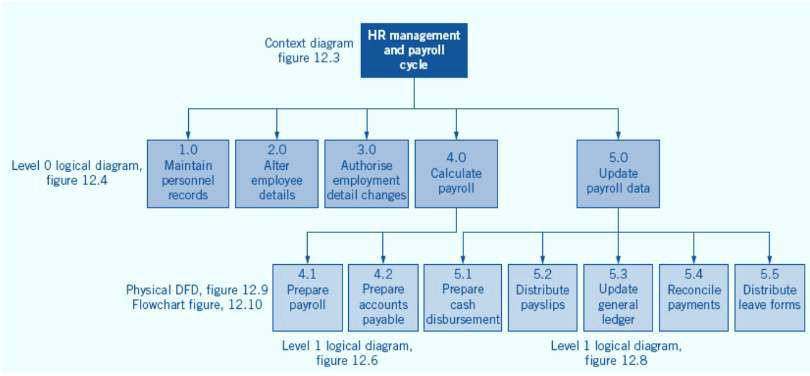 HR Management & Payroll Cycle
Documentation
HR Management & Payroll Cycle
Documentation
|
||||
|---|---|---|---|---|
|
||||
|
|
|||
|
||||
|
||||
|
|
|
|
|
|
|
|||
|
||||
|
||||
|
||||
|
|
|||
|
|
8.6 Measuring HR Management & Payroll Cycle Performance
Strategies for Acquiring IT Applications
Number of stages may vary but often includes five main stages with the specified tasks and deliverables in each
The stages are to be completed sequentially, one after the other in a linear progression
Alternative Methods and Tools for Systems Development
General Ledger & Financial Reporting Cycle Overview & Key Objectives
Finalised budgets are used as a control measure to help ascertain and monitor desirable behaviour by managers within the organisation
Variance analysis: budget estimates compared to actual results (must identify root cause of variance)
Strategic Implications of the General Ledger & Financial Reporting Cycle
Poorly arranged reported data misleading to users
Therefore high quality decision-making requires good data and comprehensible reports.
|
||
|---|---|---|
|
||
|
||
|
||
|
Technologies Underpinning the General Ledger & Financial Reporting Cycle
Activities in the general ledger and financial reporting cycle are supported by these technologies:
ERP (Enterprise Resource Planning) – integrated software that records and manages many different types of transactions within a single integrated database, e.g. SAP, Oracle
Helps to monitor and reconcile cash transactions easily and allows for automatic bank reconciliations
Can compare statements by downloading them straight from the bank website
Benefits: reduced costs, improved access to financial information, increased productivity, improved data quality and validity and fluidity of shared information
Example of how XBRL is used to add meaning to text data:
Data and the General Ledger & Financial Reporting Cycle
Transactional data extracted from:
Subsidiary ledgers – Accounts receivable ledger and Accounts payable ledger
Payroll data store (contains details of salary and wage transactions)
General Ledger & Financial Reporting Cycle Business Decisions
|
|
|---|---|
|
|
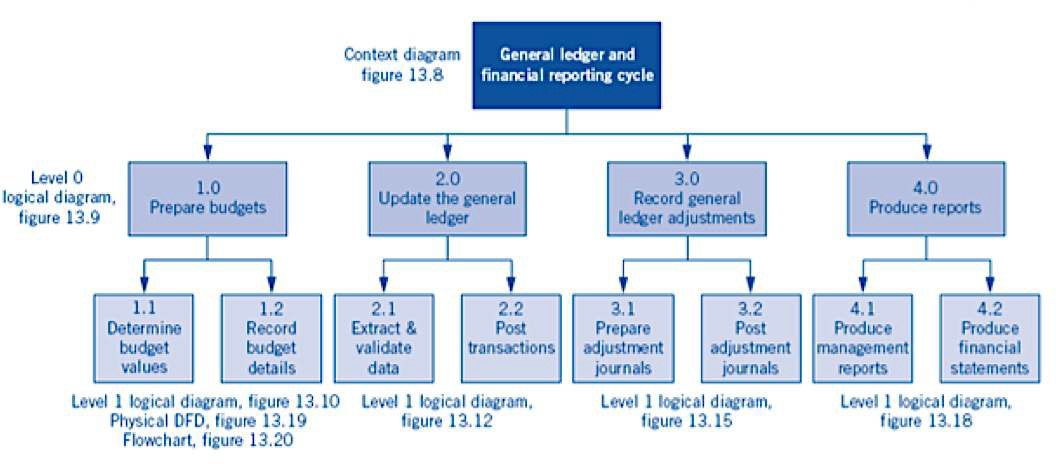 General Ledger & Financial Reporting
Cycle Documentation
General Ledger & Financial Reporting
Cycle Documentation
General Ledger & Financial Reporting Cycle Activities & Related Risks and Controls
|
|
|||
|---|---|---|---|---|
|
|
|||
|
|
|
||
|
|
|||
|
|
|
||
|
||||
|
|
|
Measuring General Ledger & Financial Reporting Cycle Performance
 A range of metrics (measure
used for a specific purpose) are used to monitor performance against
general ledger and financial reporting cycle objectives. Examples of
metrics/KPIs for this cycle objectives include:
A range of metrics (measure
used for a specific purpose) are used to monitor performance against
general ledger and financial reporting cycle objectives. Examples of
metrics/KPIs for this cycle objectives include:
|
|
|
Ethical theories (Perspectives)
Consequence-based – Utilitarianism, e.g. Trolley problem
Are moral decisions made based on the outcome or about the manner in which you achieve them?
|
|
|---|---|
|
|
Deontological Perspectives (Non-consequentialist Ethics)
This is an approach to ethics that judges the morality of an action based on the action’s adherence to a rule(s)
Deontologists look at rules and duties. This perspective focuses on the action to take and does not consider the consequences of the action
Teleological Perspective (Consequentialist Ethics)
Limitations of Utilitarianism (Consequence-based)
If the consequence is to our benefit – this is considered unethical.
Ethical Decision Making Model
Recognise an ethical issue (privacy issue, accuracy issue, property issue, accessibility issue)
Do I have sufficient information to make a decision?
Which individuals and/or groups have an important stake in the outcome?
Evaluate alternative actions
Which option best serves the community as a whole and not just some members? (the common goods approach)
Make a decision and test it – consider all approaches, which option best addresses the situation?
Act and reflect on the outcome of decisions
Ethics & Information Technology
PRIVACY ISSUES
This involves collecting, storing and disseminating information about individuals.
What information about one’s self or one’s associations must a person reveal to others, under what conditions and with what safeguards?
Information Privacy and Issues
|
|
|---|---|
|
Why is information privacy important? – Because it can lead to identity theft…
How to Maintain Information Privacy
Choose websites monitored by independent organisations
Avoid having cookies left on your machine
Visit sites anonymously
Use caution when requesting confirm email
Use separate email account from normal to protect information from your employer, sellers, and anyone using your computer
Use a VPN (virtual private network)
Using a non-descriptive email address (doesn’t include name), e.g. flyingbananas2023@gmail.com
ACCURACY ISSUES
This involves authenticity, fidelity and correctness of information that is collected and processed.
Who is responsible for authenticity, fidelity and accuracy of information?
Information Accuracy
Sources of Information Errors:
Errors in computer output can come from 2 primary sources:
PROPERTY ISSUES
What are the just and fair prices for its exchange?
How should we handle software piracy (copying copyrighted software)?
How should experts who contribute their knowledge to create expert systems be compensated?
E.g. Your last paper has been copied and handed in as if it were from another person. The computer game has been copied without the programmer receiving proper compensation for his/her effort.
Information Property
Internal use – used within organisation only
External use – can be sold to outside parties
ACCESSIBILITY ISSUES
Who is allowed to access information?
How much should companies charge for permitting access to information?
Information Accessibility
Employers – they can legally limit, monitor and access activities on company-owned computers or networks as long as policy has been distributed to employees
Case Study: San Bernardino Shooting and Apple
Ethical Issues for businesses with an AIS
CUSTOMER PROTECTION & PRIVACY
∆ Users of websites can be profiled without their knowledge
∆ The Web is being used more for marketing and selling products
Ethical Issues in E-Commerce and M-Commerce
Where did they go after?
Which IP (Internet address)?
Cookies
Risks of businesses increasing their reliance on technology
Number of cyber attacks are growing each year…
Motives Behind Cyber attacks:
Financial losses
Cybercrime
Cybercrime is often used interchangeably with terms such as: Computer crime, Computer-related crime, E-crime, High tech crime, Cyber fraud, Internet crime
∆ Audits, internal and external auditing including IT Audits
Easier way to protect yourself from cyber threats? – Have good passwords
Ethics in the Corporate Environment
TOPIC 12: CLOUD COMPUTING AND AIS
Definitions of Cloud Computing
∆ It runs on a shared data centre and you just need to plug in Gmail vs. Microsoft
∆ You don’t need servers or storage, technical team, upgrades – it can be up and running in a few days
Types of Cloud Services
Types of applications include development and testing, application platform, integration, database, general,
e.g. Google App Engine, Oracle, Palantir, WindowsAzure AppFabric (cloud companies)
Advantages and Disadvantages of Cloud Computing
Advantages of Cloud Computing - Why is everyone choosing cloud computing?
Lower total cost of owning (cheaper)
Secure storage management
Disadvantages of Cloud Computing
x Reliability on internet connection x Data security measures of provider x Quality of service
x Reliability of service provider
Easy deployment
Independent of devices
Characteristics of Cloud Environments
Multi-tenant – deliver shared services (your information is comingled with information of other companies) meaning one app is being used by multiple companies, everyone customises it for their specific needs
Per-usage based pricing model – only pay for what you need
Why do companies use it?
COST SAVINGS
Pay only for the apps you use
DEPLOYMENT SPEED (Spotify: download sign up pay you have access to the service – very quick)
SECURITY
Secure data centers
Automatic backups, cloud service companies back up data more often
Cloud Computing Challenges
∆ Cloud Security policy/procedure transparency
∆ CSP business viability
∆ Disaster recovery
Note: CSP – cloud service provider