Loading and grading levels alter traffic flows
Information related to the unit of competency
Guidelines and instructions to complete each task and activity
The Student Pack is a document for students to complete to demonstrate their competency. This document includes context and conditions of assessment, tasks to be administered to the student, and an outline of the evidence to be gathered from the student.
Student and trainer details
Qualification and unit of competency
| Qualification/Course/Program Details | |
|---|---|
| Code: | |
| Name: | |
| Unit of competency | |
| Code: | ICTTEN615 |
| Name: | Manage network traffic |
| Releases: | 1.0 |
| Release date: | 19/Jan/2021 |
Assessment Submission Method
Student declaration
|
|---|
Assessment Plan
Completion of the Assessment Plan
Every assessment has a “Feedback to Student” section used to record the following information. Your trainer/assessor must also ensure that all sections are filled in appropriately, such as: |
|---|
Unit Requirements
Pre-Assessment Checklist: Task 1 - Knowledge Test
| The purpose of this checklist |
|---|
| The pre-assessment checklist helps students determine if they are ready for assessment. The trainer/assessor must review the checklist with the student before the student attempts the assessment task. If any items of the checklist are incomplete or not clear to the student, the trainer/assessor must provide relevant information to the student to ensure they understand the requirements of the assessment task. The student must ensure they are ready for the assessment task before undertaking it. |
| Section 1: Information for Students |
☐ Make sure you have completed the necessary prior learning before attempting this assessment. ☐ Make sure that you have access to a computer and the internet (if you prefer to type the answers). ☐ Make sure that you have all the required resources needed to complete this assessment task. |
| Section 2: Reasonable adjustments |
☐ I do require reasonable adjustment ☐ I do not require reasonable adjustment |
☐ I confirm I have accessed and understand the assessment information as provided in the Training Organisation’s Student Handbook. ☐ I confirm I have been given fair notice of the date, time, venue and/or other arrangements for this assessment. |
| Task instructions |
|
Assessment Task 1: Knowledge Test
| Q1: |
|
Satisfactory response | |
|---|---|---|---|
| Yes ☐ | No ☐ | ||
Answer:
|
|||
| Q2: | 2.1. What is system monitoring alerts and alarms. Write your answer in 150-200 words. 2.2. What is route and circuit in computer networks. Write your answer in 50-100 words. 2.7. Explain network traffic engineering. Write your answer in 100-150 words. 2.8. Discuss workplace documentation related to network traffic. Write your answer in 150-200 words. |
Satisfactory response | |
| Yes ☐ | No ☐ | ||
- NMS provide real time monitoring of resources and in-depth analytics of collected data. - It enables a network to grow more by adding some abilities to it. 2.6 The semi-permanent control is applied to control the semi-permanent virtual circuits in a large network. In a large network, multiple paths are available there between a recipient and transmitter. Two types of switching techniques are used to control the semi-permanent circuits, as packet and circuit switching technique. The switching approach will choose the best data transport path. Switching is used to connect systems so that they may communicate with one another. 2.7 The volume of data travelling over a computer network at any particular time is referred to as network traffic. Network traffic, also known as data traffic, is divided into data packets and transmitted over a network before being reassembled by the receiving device or computer. Traffic engineering is the process by which a network operator designs the pathways used to transmit traffic flows that differ from those picked automatically by the routing protocol in use in that network. There are several ways to control network traffic, for example, by creating security policies for authentication or unauthenticated users, specify some rules to allow or deny a user/host, and implementing threat protection to keep safe the network from intrusions. |
|||
| Q3: | Satisfactory response | ||
| Yes ☐ | No ☐ | ||
|
|||
| Q4: |
4.3. Explain the following eight (8) network dimensioning principles:
|
Satisfactory response | |
| Yes ☐ | No ☐ | ||
This type of blocking will create barriers in the network for example, a firewall can allow or block traffic based on IP address or protocol. IP address blocking is a security mechanism that stops a specific or set of IP addresses from connecting to a mail, web, or Internet server. This is often done to prevent any unwanted sites or hosts from entering the server or node and causing harm to the network or individual PCs. While protocol-based blocking uses other low-level network identifiers, such as a TCP/IP port number that might identify a specific program on a server or a kind of application protocol.
Platform-based blocking is an approach that requires the participation of the platform's owner, such as Google or Microsoft. In this strategy, queries to a search engine from a certain group of Internet users will yield a different set of results than the rest of the Internet, filtering away references to information that is, in some manner, offensive. In certain circumstances, the definition of what should be prohibited is based on local regulations and government requirements, but it might also be due to concerns expressed by the search engine operator. A search engine, for example, may restrict links to malware or information deemed improper by its own terms of service.
This principle focusing on recognizing customer needs rather than focusing on the function and features of the LAN. Determine the features and needs of each distinct physical device. Determine the architecture and infrastructure by taking into account the power, bandwidth, and application needs of each endpoint.
At this stage, we can plan to deploy the network and implement it in real-time. Planning of the network is done in the previous step, covering all the assessments, analysis, device identification and network topology. All these components are now implemented in a network design.
When the document is prepared, submitted and approved to be implement, we can proceed with the implementation phase. We will then proceed with the implementation of the network that starts with site survey, cable planning, device placement, making connection, making configuration, testing and monitoring. |
|||
| Q5: |
Write your answer in 150-200 words. |
Satisfactory response | |
| Yes ☐ | No ☐ | ||
5.2 Here is the detail of two types of transmission signals: a. Analogue signal – This is a signal type in which signals will increase and decrease as per the data is being transmitted. Analog signals are a type of continuous time-varying signal that is divided into composite and simple signals. A simple analogue signal is nothing more than a sine wave that cannot be decomposed, whereas a composite analogue signal can be decomposed into multiple sine waves. |
|||
| Q6: |
6.3. What do you understand by switching? Write your answer in 50-100 words. 6.4. Discuss the following three (3) types of switching: 6.5. Explain routing and discuss the types of routing. Write your answer in 150-200 words. 6.6. Discuss the following two (2) network transmission techniques: |
Satisfactory response | |
| Yes ☐ | No ☐ | ||
6.2 Here are the five basic network topologies – a. Bus topology – Bus topology, also known as line topology, is a network topology in which all network devices are connected by a single network cable or coaxial cable. The bus, backbone, or trunk is the single cable through which all data is transmitted between devices. 6.3 Switching is the process of routing packets from one port to another that leads to the destination. When data enters a port, it is referred to as ingress, and when data exits a port, it is referred to as egress. A communication system may consist of several switches and nodes. There are three type sof switching, namely packet, message, and circuit switching. 6.4 Here are the three types of switching: a. Static routing – in this routing type, we have to manually add routes in the routing table. It is the most basic routing method which provide minimal overhead, security and minimal use of bandwidth. b. Default routing – in this routing, a router will send all the packets to the next hope or router. It does not matter that the packets belong to that network or not. Either it forward the packets to the router, configured as a default gateway. |
|||
| Q7: | Answer the following questions regarding the network traffic contingency plans. 7.1. What do you understand by contingency plan. Write your answer in 100-150 words. |
Satisfactory response | |
| Yes ☐ | No ☐ | ||
|
|||
| Q8: | Describe the various network management systems suitable for conducting traffic evaluations. Write your answer in 250-300 words. | Satisfactory response | |
| Yes ☐ | No ☐ | ||
| The purpose of this checklist |
|---|
| The pre-assessment checklist helps students determine if they are ready for assessment. The trainer/assessor must review the checklist with the student before the student attempts the assessment task. If any items of the checklist are incomplete or not clear to the student, the trainer/assessor must provide relevant information to the student to ensure they understand the requirements of the assessment task. The student must ensure they are ready for the assessment task before undertaking it. |
| Section 1: Information for Students |
☐ Make sure your trainer/assessor clearly explained the assessment process and tasks to be completed. ☐ Make sure you understand what evidence is required to be collected and how. ☐ The due date of this assessment task is in accordance with your timetable. ☐ In exceptional (compelling and compassionate) circumstances, an extension to submit an assessment can be granted by the trainer/assessor. Evidence of the compelling and compassionate circumstances must be provided together with your request for an extension to submit your assessment work. |
| Section 2: Reasonable adjustments |
Declaration (Student to complete) ☐ I confirm that the purpose and procedures of this assessment task has been clearly explained to me. ☐ I confirm that I am ready for assessment. Student Name: ______________________________________ |
| Task instructions |
|
Conduct traffic measurements
Develop and implement contingencies to control traffic flow
Activity 2: Interrogate system monitoring alerts and alarms and identify areas of the route and circuit unavailability
Activity 3: Assess planned and unplanned outages to determine network unavailability and verify restoration times
Activity 8: Conduct traffic measurements across all required routes
Activity 9: Analyse results, historical data and traffic volume requirements
Activity 14: Develop contingency plans to allow for problems during network changes
Activity 15: Implement software changes according to planned network strategy
Activity 20: Analyse measurements and provide a report to relevant personnel with recommendations for further changes
Activity 21: Review and monitor strategies and initiate corrective action where required
Activity 26: Identify potential network traffic problems and make recommendations to network planners
Activity 27: Complete reports with recommendations and forward them to relevant personnel.
TrueFort uses an application-centric approach to protect cloud, hybrid, and legacy environments from hidden risks. They believe the largest, most-targeted part of the enterprise cyberattack is its application environment—and it aims to secure that by using telemetry from a client’s existing agents to deliver solutions to its infrastructure, thereby improving risk postures. The platform also supports an open ecosystem model that allows clients to use agents from tools including CrowdStrike and Carbon Black. Its full-stack cloud workload capabilities, patented advanced behavioural analytics, policy automation, real-time insight into the application environment, and bring-your-own-agent approach have solidified it as a lead competitor in the space.
New Project along with organisational requirements:
Evaluate network capacity and traffic congestion
Develop traffic control strategies
The purpose of this assessment task is to conduct the management of network traffic on at least two network systems.
This assessment task will be completed in your training organisation’s IT lab. Your trainer/assessor will supervise you in performing this assessment task.
| Work details, Planned network strategy and Scope | |||
|---|---|---|---|
Planned network strategy for LAN (Local Area Network) at both computer labs:
|
|||
| Customer Complaints | |||
| Planned and Unplanned outages | |||
Planned outages for lab1:
|
|||
| Security arrangements | |||
a) Firewall – Monitoring of web traffic or even traffic between 2 internal networks allows you to detect and control abnormal and harmful It can help you block all the traffic that is unnecessary for business needs. An active firewall policy not only limits the unbeneficial traffic but also stops the traffic moving from all malicious sites, thereby protecting the network and enterprise data. While there are many firewall solutions out there, select the one that suits your organization’s needs. Here the depth and breadth of the protection required will form the key parameters for firewall selection. |
|||
| Legislation | |||
Data Protection and the APPs The Privacy Act APPs comprise legally binding obligations for APP entities for:
Industry Standard codes relating to Data and technology are further divided into the following categories by committee: |
|||
| Standards and Regulations | |||
In July 2019, APRA issued CPS 234 on Information Security. This regulation requires APRA-regulated financial, insurance and superannuation entities to comply with legally binding minimum standards of information security, including by:
APRA-regulated entities are required to externally audit their organisation’s compliance with CPS 234 and report to APRA in 2021. If organisations are non-compliant, they may be required to issue breach notices and create rectification plans. If organisations are unable to comply with the standards following this process, APRA may undertake a more formal enforcement process which may include enforceable undertakings or court proceedings. Data Protection The Privacy Act APPs provide a legally binding framework for APP entities to the collection, processing, use, storage and dissemination personal information. "Personal information" under the Privacy Act is defined broadly as information or an opinion about an identified or reasonably identifiable individual. Personal information also includes "sensitive information", which includes information or opinions on an individual’s race, ethnicity, politics, religion, sexual orientation, health, trade associations and criminal records. Sensitive information is often afforded a higher level of protection than other personal information. The Privacy Act applies to "APP entities" which, subject to some exceptions, including federal government agencies, private sector organisations with an annual turnover of over AUD3 million and smaller entities with data-intensive business practices (including private health providers, businesses that sell or purchase personal information and service providers to the federal government).
|
|||
| Funding Parameters | |||
| Maximum Grant | $15000 | ||
| Maximum total project cost | $8500 | ||
| Minimum % of overall match that must be cash | 10% | ||
| Budgeted levels | |||
| Use of funds in % | 50% | ||
| Cash | $10000 | ||
| Plan amendments | |||
|
|||
| Enterprise network management policy | |||
The Calsoft Solutions Network Management Policy applies to individuals who are involved in the configuration, maintenance, or expansion of the Calsoft Solutions network infrastructure. Policy Appropriate technical solutions must be implemented to protect Confidential information from the unauthorised transfer, modification, or disclosure (i.e. next-gen firewalls, IDS/IPS, DLP). A map or diagram of the network and data flow, including external connections, must be maintained. This map or diagram must be updated after any changes to the network occur. This diagram should be reviewed every 6 months to ensure it continues to represent the network architecture Resource usage must be monitored to ensure the required system performance. Information processing facilities must address redundancy sufficient to meet availability requirements. Network devices must be installed and configured following Calsoft Solutions implementation standards. The use of departmental network devices is not permitted without the written authorisation from Calsoft Solutions IT Management. Wireless networks must be segmented using appropriate technical controls. Authentication settings (passwords, encryption keys, etc.) must be changed periodically as well as anytime it is suspected that such information has been compromised or if anyone with knowledge of the information leaves the organisation. Calsoft Solutions wireless network users must not tamper with network access points or security settings. Users must not connect to another wireless network and the Calsoft Solutions wireless network simultaneously. Personnel found to have violated this policy may be subject to disciplinary action, up to and including termination of employment and related civil or criminal penalties. Any vendor, consultant, or contractor found to have violated this policy may be subject to sanctions up to and including removal of access rights, termination of the contract(s), and related civil or criminal penalties. |
|||
You will identify potential network traffic problems and make recommendations
You will provide information for capacity planning.
Conduct traffic measurements
Develop and implement contingencies to control traffic flow
Activity 2: Interrogate system monitoring alerts and alarms and identify areas of the route and circuit unavailability
Activity 3: Assess planned and unplanned outages to determine network unavailability and verify restoration times
Activity 8: Conduct traffic measurements across all required routes
Activity 9: Analyse results, historical data and traffic volume requirements
Activity 14: Develop contingency plans to allow for problems during network changes
Activity 15: Implement software changes according to planned network strategy
Activity 20: Analyse measurements and provide a report to relevant personnel with recommendations for further changes
Activity 21: Review and monitor strategies and initiate corrective action where required
Activity 26: Identify potential network traffic problems and make recommendations to network planners
Activity 27: Complete reports with recommendations and forward them to relevant personnel.
To obtain work details, planned network strategy and scope from the relevant personnel and arrange for site access in compliance with required security arrangements, legislation, codes, regulations and standards
To interrogate system monitoring alerts and alarms and identify areas of the route and circuit unavailability
To activate and deactivate semi-permanent controls active in the network regularly to simulate irregular traffic
To conduct traffic measurements across all required routes
To develop strategies for recovery where traffic congestion occurs
To develop contingency plans to allow for problems during network changes
To conduct monitoring of changes and take measurements to assess outcomes of variations
To analyse measurements and provide a report to relevant personnel with recommendations for further changes
To predict future potential traffic trends and requirements using data on current and historical traffic patterns
To identify potential network traffic problems and make recommendations to network planners
Activity 1: Obtain work details, planned network strategy and scope from the relevant personnel and arrange for site access in compliance with required security arrangements, legislation, codes, regulations and standards.
This part of the activity requires you to obtain work details, planned network strategy and scope from the relevant personnel and arrange for site access in compliance with required security arrangements, legislation, codes, regulations and standards and document the outcomes using ‘Template 1’.
The trainer/assessor must observe the student conducting the meeting.
After preparing the meeting agenda, you are then required to send an e-mail to the meeting participants to invite them to the meeting.
After e-mailing the meeting agenda to the participants of the meeting, you are then required to conduct a meeting with them.
| Before the meeting |
|
|---|---|
| During the meeting |
|
| After the meeting | 2. Document the discussions using ‘Template’ provided based on the feedback received, if any. |
Meeting script:
| Work details, Planned network strategy and Scope (150-200 words) | |
|---|---|
In this task, we are assigned the task of conducting network traffic management for the two local area networks (LANs). These LANs are installed in two computer labs. We must undertake traffic measurements, develop and implement contingency plans to control traffic flow, identify potential network traffic problems, offer recommendations, and give data for capacity planning. Planned network strategy for LAN (Local Area Network) at both computer labs: |
|
| Security arrangements (300-350 words) | |
a) Firewall – These are the security devices used to monitor network traffic between two internal LANs. It controls harmful and abnormal traffic based on pre-configured firewall rules. It can assist you in blocking all unneeded traffic for commercial purposes. An active firewall policy not only limits unbeneficial traffic but also prevents traffic from all harmful sites from entering the network, thereby securing the network and company data. There are numerous sorts of firewall solutions available to keep us safe. b) Powerful antivirus – As there are so many antiviruses are available which offer good level of security. Depending up on the organization’s requirements, we can select the best antivirus for them that is capable of remote monitoring, support cloud hosting, and practically capable of secure the entire infrastructure. |
|
| Legislation (100-150 words) | |
| There are two legislations are applicable on the given case study organization. The data protection APP act is a legal obligation applicable on monitoring of a network and compromising with some personal details of a user. There are a total of thirteen parts of this APP legislation that are applied on the organization. Another applicable legislation includes some industry standard codes which help in determining and provide and standard approach to select and install hardware and software equipment like cable, technology, broadcast setting, graphic, and all other recommended networking devices. both of these legislations will help in safeguarding user privacy, a legal binding with applicable laws and security and availability of service due to the use of standard devices according to the industry standard. | |
| Codes for cyber security operations (50-100 words) | |
| In respect to the cyber security operations, there are two legislations are applicable on the given scenario. These applicable cyber security codes are data protection act, APP, and some industry standard codes. There are thirteen APP codes (range from 1 to 13) are applicable to protect user’s privacy and personal details while monitoring. Some industry standard codes are also applicable, which include some committee codes related to cabling, broadcasting service, ethernet technology, ACA standards, and information security. | |
| Standards (400-450 words) | |
Data protection standards – When developing rules for the collection, use, and storage of specific information, organizations should consider their obligations under the Privacy Act, Archives Act 1983 (Archives Act), and TIA Act. The OAIC's Privacy Framework, as described in Section 3.2 Consensus or Commonly Applied Framework, may be regarded as a de facto norm for data protection.
|
|
| Regulations (250-300 words) | |
Here are the regulations applicable on data protection: NDB scheme – These laws are applicable on the organizations dealing with personal information in Australia. Here are the applicable laws:
|
|
Meeting agenda template:
Venue: Zoom meeting Date: 01/07/2022 10:00 AM |
|||
|---|---|---|---|
| No. | Points Discussed | Actions Suggested | Target Date |
| 1 | Scope of the project | Scope is defined for the work | 03/07/2022 |
| 2 | Work details | Work details are analysed and recorded | 06/07/2022 |
| 3 | Strategic network planning | Complete the network planning and results are recorded | 10/07/2022 |
| 4 | Compliances and regulations | Regulatory compliances are searched and develop to meet the project requirements | 14/07/2022 |
| 5 | Security policies and codes | Search and noted down the security codes and applicable policies | 19/07/2022 |
| 6 | Standards, regulations and codes applicable | Search the relevant codes, standards and regulations and recorded properly | 23/07/2022 |
Performance Criteria/Performance Checklist: Activity 1
This activity requires you to interrogate system monitoring alerts and alarms and identify areas of the route and circuit unavailability.
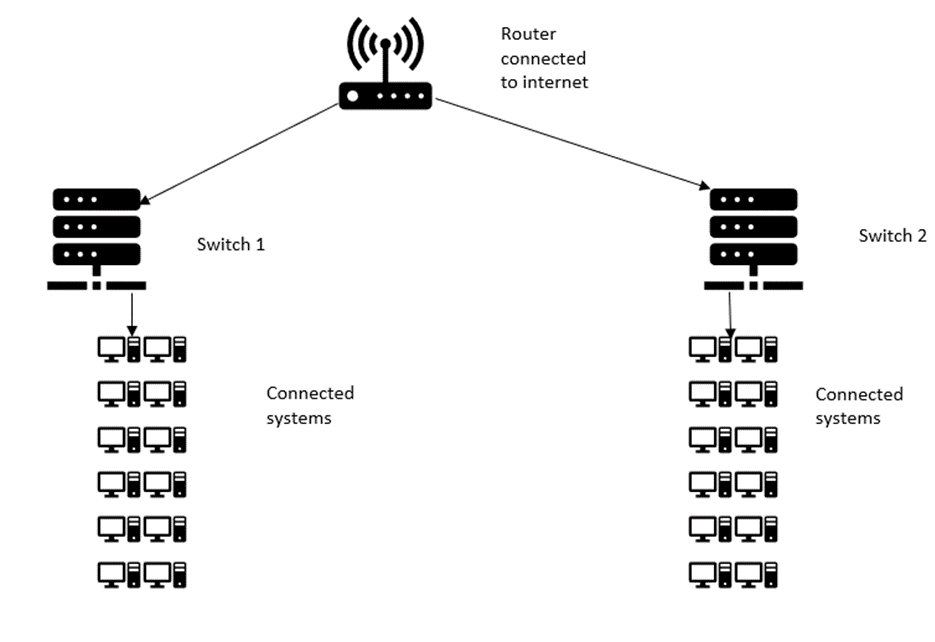
This activity is required to be performed at both LAN network systems of both computer labs.
High CPU or memory usage
Overloaded or crashed servers
Ethernet ports (Check the ethernet ports are working, and traffic is flowing through)
Further, you must:
| System monitoring alerts and alarms for the below issues using Solarwinds tool (250-300 words) | |
|---|---|
| Response time delays | The maximum response time delay detected with the server is 1400 milliseconds. While the minimum response time delay is 700 milliseconds. |
| High CPU or memory usage | |
| Overloaded or crashed servers | The server was overloaded, as per detected logs, many time while access amdb database service. The max CPU time is 14696.65 milli seconds. |
| Failures of critical hardware like routers, switches, gateways, and proxies | There are no logs found for failure of any hardware like switch, router, gateway or proxies. |
| Areas of the route and circuit
unavailability (50-80 words) |
|
| The IP address of the system | IP address of the system is 172.17.160.1 (PGSQL) |
| Hub or Switch | No hub or switch is configured in the network |
| Ethernet ports | No wired connectivity detected in the network, among devices. So no ethernet ports are there. |
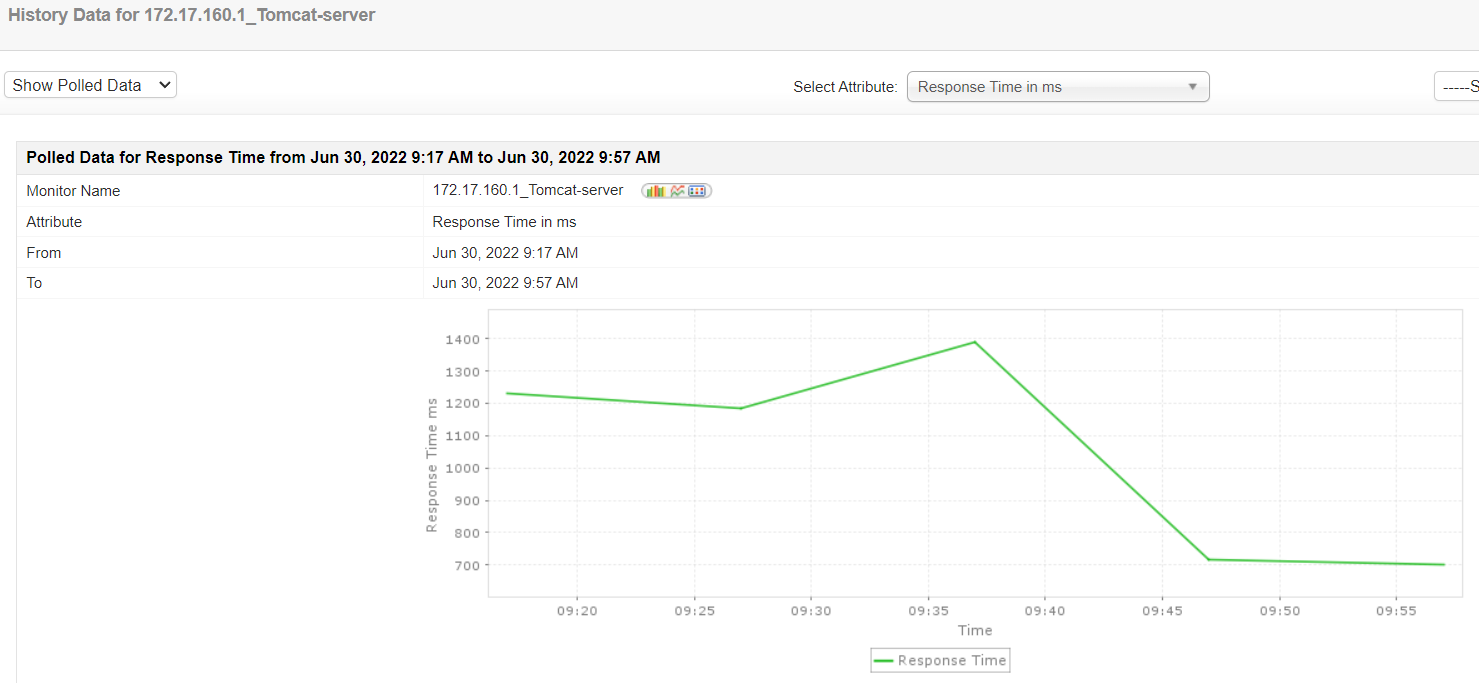
Response time delay
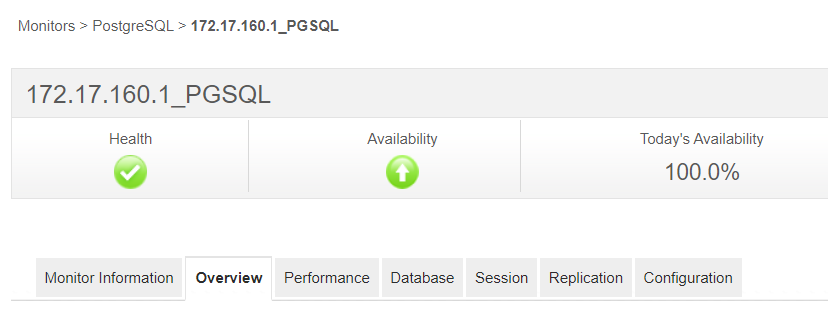
IP address of the system
Activity 3: Assess planned and unplanned outages to determine network unavailability and verify restoration times.
This activity is required to be performed at both LAN network systems of both computer labs.
To do so, you need to:
| Planned and Unplanned outages (40-80 words) |
|---|
According to the given scenario, planned outage will be 2 minutes when the whole system will go down. Planned outages for lab2: |
Performance Criteria/Performance Checklist: Activity 3
Description of the activity
This activity is a continuation of Activity 3.
Obtain and interrogate network management system for the below issues and document using Template 4:
Poor network performance.
Take a screenshot of each step implemented to obtain and interrogate the network management system and identify traffic status and submit it to the trainer/assessor.
This task cannot be done due to the lack of networking resources, required for this task.
| Obtain and interrogate network management system for the below issues (100-150 words) |
|---|
| Identify traffic status using Solarwinds tool (100-150 words) |
Performance Criteria/Performance Checklist: Activity 4
Activity 5: Analyse system alert and identify real and potential traffic problems.
This part of the activity requires you to analyse system alerts and identify real and potential traffic problems, and document the outcomes using ‘Template 5’.
To do so, you need to:
Analyse system alert from system logs and events and document using Template 5.
Template 5: Analyse system alert and identify real and potential traffic problems.
| System alert from logs and events (50-100 words) |
|---|
| Real and potential traffic problems (30-50 words) |
Real traffic problems |
Activity 6: Analyze customer complaints and traffic measurement data to identify network problems.
This part of the activity requires you to analyses customer complaints and traffic measurement data to identify network problems and document the outcomes using ‘Template 6’.
This activity requires you to use the Solar winds tool.
To do so, you need to:
Local Network is Unable to Connect to the internet
Unable to Connect to Local File or Printer Shares
Duplicate IP Addresses
Template 6: Analyse customer complaints and traffic measurement data to identify network problems.
| Customer complaints (100-150 words) |
|---|
|
| Traffic measurement data (100-150 words) |
| While analyzing traffic using Solar Winds, we detected that high network traffic is flowing in the local and external network. This could be a result of slower network speed, dis-connectivity or no connectivity issue. For this reason, when a new user trying connecting to the network, it shows an error of IP address exhausted. This error is due to the exhausted IP address limit of DHCP server and it will not able to connect a greater number of systems in the network. The IP address conflict error was detected due to same IP address is assigned to two users and both are not able to communicate in the local network to any other system. |
| Network problems (50-100 words) |
IP Address Exhaustion Duplicate IP Addresses Service not available |
Performance Criteria/Performance Checklist: Activity 6
Description of the activity
This activity is a continuation of Activity 6.
OpenCommand Prompt, right-click the top result, and select Run as administrator.
Type the following command to identify the name of the adapter you want to enable and press Enter:
Document the outcomes using Template 7.
Submit the outcomes to the trainer/assessor.
| Activate and deactivate semi-permanent controls active in the network regularly to simulate irregular traffic (300-350 words) |
|---|
Netsh interface set interface Wi-Fi enable |
Performance Criteria/Performance Checklist: Activity 7
This activity requires you to conduct traffic measurements across all required routes.
This activity is required to be performed at both computer labs.
Passive measurement of traffic
Document the outcomes using Template 8.
| Traffic measurement approaches (150-200 words) |
|---|
Passive Measurement of Traffic |
Performance Criteria/Performance Checklist: Activity 8
This part of the activity requires you to analyse results, historical data and traffic volume requirements and document the outcomes using ‘Template 9’.
Description of the activity
To do so, you need to:
Analyse results and historical data obtained from Activity 8.
Further, you must:
Document the outcomes of test conducted using Template 9.
| Analyse results, historical data and traffic volume requirements (150-200 words) | |
|---|---|
| Network Availability Testing | |
| Network Speed Testing | |
| Bandwidth Usage Testing | |
This part of the activity requires you to determine specific thresholds, loading and grading levels to alter traffic flows and document the outcomes using ‘Template 10’.
Description of the activity
Review the results from Activity 9.
Determine specific thresholds, loading and grading levels to alter traffic flows.
Template 10: Determine specific thresholds, loading and grading levels to alter traffic flows.
| Thresholds, Loading and Grading levels | |
|---|---|
| Thresholds | |
| Loading | |
| Grading levels | |
Performance Criteria/Performance Checklist: Activity 10
Description of the activity
This activity is a continuation of Activity 10.
Template 11: Obtain funding parameters and budgeted levels, and determine plan amendments.
| Funding Parameters | |
|---|---|
| Maximum Grant | $150,000 |
| Maximum total project cost | $260,000 |
| Minimum % of overall match that must be cash | 50% |
| Budgeted levels | |
| Use of funds in % | 31% |
| Cash | $58,000 |
| Plan amendments (30-50 words) | |
Execution of the plan will be done as per plan. |
|
Activity 12: Confirm that traffic control strategies to prevent traffic problems.
This activity is required to be performed at both computer labs.
To do so, you need to:
Template 12: Confirm that traffic control strategies to prevent traffic problems.
| Confirming Traffic control strategies to prevent traffic problems using the below techniques (250-300 words) |
|---|
Open Loop Congestion Control |
This activity requires you to develop strategies for recovery where traffic congestion occurs.
This activity is required to be performed at both computer labs.
Use a CDN (Content Delivery Network) that will optimise resources by placing more requests on edge servers
Prioritise traffic on your network (for instance, VoIP services is always high-priority)
Check for any attack attempts in your connection logs
Use a VPN such as Private Internet Access to bypass congestion (if the issue is on your ISP’s side)
| Strategies for recovery where traffic congestion occurs (100-150 words) |
|---|
Performance Criteria/Performance Checklist: Activity 13
This activity is a continuation of Activity 13.
This activity requires you to develop contingency plans to allow for problems during network changes.
Determine probability of each risk identified.
Determine and document response to each risk identified.
| Contingency plans (300-350 words) |
|---|
Performance Criteria/Performance Checklist: Activity 14
Description of the activity
This activity is a continuation of Activity 14.
Implement software changes according to planned network strategy and document using Template 15:
Configuration of SNMP capability.
| Implement Software changes (50-100 words) | |
|---|---|
| Configuration of SNMP capability. | |
| Shutting down the problematic software | |
| Updating device’s firmware | |
This part of the activity requires you to develop short-term ad hoc solutions where only a temporary solution is required and document the outcomes using ‘Template 16’.
Description of the activity
To do so, you need to:
Develop short-term ad hoc solutions and document using Template 15:
Traffic optimisation following tariff plan
Template 16: Develop short-term ad hoc solutions where only a temporary solution is required.
| Develop short-term ad hoc solutions (250-300 words) |
|---|
Description of the activity
This activity is a continuation of Activity 16.
Implement one of the temporary solutions developed in Activity 16.
Remove the solution after 1 hour and confirm it can be reversed.
| Confirm that reversal action can be initiated (200-250 words) |
|---|
Activity 18: Implement contingency plan where required according to organisational requirements.
This activity is required to be performed at both computer labs.
This activity requires you to use the Solarwinds tool.
Recovery phase
Document the outcomes using Template 18.
| Steps to obtain sign off on final business solution (300-350 words) |
|---|
Performance Criteria/Performance Checklist: Activity 18
This part of the activity requires you to conduct monitoring of changes and take measurements to assess outcomes of variations and document the outcomes using ‘Template 19’.
Description of the activity
To do so, you need to:
Conduct monitoring of changes and take measurements and document using Template 19.
| Conduct monitoring of changes and take measurements (50-100 words) |
|---|
Activity 20: Analyse measurements and provide a report to relevant personnel with recommendations for further changes.
This activity is required to be performed at both computer labs.
This activity requires you to use the Solarwinds tool and Ms Word.
TCP NewReno
TCP CUBIC
| Recommendations to use the below techniques for future changes (50-100 words) |
|---|
| Template to Write an email (250-300 words) |
Performance Criteria/Performance Checklist: Activity 20
This activity requires you to review and monitor strategies and initiate corrective action where required.
This activity is required to be performed at both computer labs.
Further, you must take a screenshot of each step implemented and submit it to the trainer/assessor via e-mail.
Template 21: Review and monitor strategies and initiate corrective action where required.
| Initiate corrective action (80-100 words) |
|---|
This part of the activity requires you to measure and analyse traffic loads to assess congestion problems and determine possible impact, and document the outcomes using ‘Template 22’.
Description of the activity
To do so, you need to:
Measure and analyse traffic loads to assess congestion problems and document using Template 22:
Determine possible impact and document using Template 22:
Packet Loss
Template 22: Measure and analyse traffic loads to assess congestion problems and determine possible impact.
| Measure and analyse traffic loads to assess congestion problems (100-150 words) |
|---|
Poor Network Design/Mis-Configuration |
| Determine possible impact (100-150 words) |
Packet Loss Jitter |
This part of the activity requires you to control traffic flow and prevent processor overloads, and document the outcomes using ‘Template 23’.
Description of the activity
To do so, you need to:
Control traffic flow and prevent processor overloads and document using Template 23.
| Control traffic flow and prevent processor overloads. (100-150 words) |
|---|
Activity 24: Evaluate potential traffic increases for impact on the network and develop contingencies to control traffic flow if required.
This part of the activity requires you to evaluate potential traffic increases for impact on the network and develop contingencies to control traffic flow if required, and document the outcomes using ‘Template 24’.
This activity requires you to use the Solarwinds tool.
To do so, you need to:
Client or Server Health
Develop contingencies to control traffic flow considering the below practices and document using Template 24:
Program Improvement
Template 24: Evaluate potential traffic increases for impact on the network and develop contingencies to control traffic flow if required.
| Evaluate potential traffic increases for impact on the network (400-450 words) |
|---|
| Develop contingencies to control traffic flow (150-200 words) |
1. Program Management 2. Planning |
This part of the activity requires you to predict future potential traffic trends and requirements using data on current and historical traffic patterns and document the outcomes using ‘Template 25’.
Description of the activity
To do so, you need to:
Analyse current and historical traffic patterns obtained in previous activities using the below methods and document using Template 25:
Template 25: Predict future potential traffic trends and requirements using data on current and historical traffic patterns.
| Current and historical traffic patterns (80-100 words) |
|---|
Poisson’s Model: |
| Future potential traffic trends and requirements (80-100 words) |
This activity requires you to identify potential network traffic problems and make recommendations to network planners.
This activity is required to be performed at both computer labs.
Too many devices
Bandwidth hogs
| Potential network traffic problems (80-100 words) |
|---|
Outdated or non-compatible hardware Too many devices |
| Make recommendations to network planners (80-100 words) |
This part of the activity requires you to complete reports with recommendations and forward them to relevant personnel, and document the outcomes using ‘Template 27’.
Description of the activity
Future potential traffic trends and requirements
Potential network traffic problems
| Template to Write an email (250-300 words) |
|---|
Potential network traffic problems Reports with recommendations |
Assessment Results Sheet
| Outcome |
Outcome (make sure to tick the correct checkbox): Satisfactory (S) ☐ or Not Satisfactory (NS) ☐ Date: _______(day)/ _______(month)/ _______(year) |
|
|---|---|---|
| Student Declaration |
|
|
| Student Signature | ||
| Date | ||
| Trainer/Assessor Name | ||
| Trainer/Assessor Declaration |
I declare that I have conducted an assessment of this student’s submission. The assessment tasks were deemed current, sufficient, valid and reliable. I declare that I have conducted a fair, valid, reliable, and flexible assessment. I have provided feedback to the student. |
|
| Trainer/Assessor Signature | ||
| Date | ||
| Office Use Only |
| Reasonable Adjustment Strategies Matrix (Trainer/Assessor to complete) | ||
|---|---|---|
| Category | Possible Issue | Reasonable Adjustment Strategy (select as applicable) |
| LLN | Verbal assessment Presentations |
|
| Non-English Speaking Background | Reading Writing |
Use short sentences that do not contain large amounts of information Clarify information by rephrasing, confirm understanding |
| Indigenous | Knowledge and understanding Flexibility |
Flexible delivery Using group rather than individual assessments |
| Age | Trainer/Assessor should refer to the student’s experience Ensure that the time available to complete the assessment takes account of the student’s needs Changes to course design, e.g. substituting an assessment task Modifications to the physical environment, e.g. installing lever taps, building ramps, installing a lift |
|
| Educational background | Discuss with the Student previous learning experience Ensure learning and assessment methods meet the student’s individual need |
|
| Disability | Limited study skills and/or learning strategies |
Identify the issues Changes in teaching practices, e.g. wearing an FM microphone to enable a student to hear lectures Supply of specialised equipment or services, e.g. a note-taker for a student who cannot write |
| Trainer/Assessor Name | |
|---|---|
| Trainer/Assessor Declaration | I declare that I have attached all relevant evidence to provide reasonable adjustment. The training package guidelines and criteria have not been compromised in the process of providing reasonable adjustment to the student. I declare that I have conducted a fair, valid, reliable, and flexible assessment. I have provided explanation of reasonable adjustments strategy used, as required. |
| Trainer/Assessor Signature | |
| Date |
Please complete this evaluation form as thoroughly as you can, in order for us to continuously improve our training quality. The purpose of the evaluation form is to evaluate the areas below:
logistics and support
| No. | Criteria/Question |
|
|
|||
|---|---|---|---|---|---|---|
| B | Trainer/Assessor Evaluation | |||||
| 1 | The trainer/assessor was prepared and knowledgeable on the subject of the program | |||||
| 2 | The trainer/assessor encouraged student participation and input | |||||
| 3 | The trainer/assessor made use of a variety of methods, exercises, activities and discussions | |||||
| 4 | The trainer/assessor used the material in a structured and effective manner | |||||
| 5 | The trainer/assessor was approachable and respectful of the learners | |||||
| 6 | The trainer/assessor was punctual and kept to the schedule | |||||
| 7 | The trainer/assessor was easy to understand and used the correct language | |||||
| Additional Comments on Training | ||||||