Identity and Access Management Part 1
Kelly School of Business Indiana University Information Systems Graduate Programs
Part 1: Introduction and Concepts
Access Control Definition
- The process of allowing only authorized users, programs, or other computer systems to observe, modify, or otherwise take possession of the resources of a computer system
Access Control
- Access controls are a collection of mechanisms, processes, or techniques that work together to protect the assets on an enterprise by reducing exposure to unauthorized activities and providing access to information and systems to only authorized entities
- Who or what is accessing the assets?
- Identify
- Authenticate
- Authorize
- Monitor
- Access control is the backbone of information security
Actors in Access Control
- A subject is an active entity (generally an individual, process, or device) that causes information to flow among objects or changes the system state. It can be the user, requestor, or mechanism acting on behalf of the user or requestor
- An object is a passive information system-related entity containing or receiving information. It can be the resource or requested entity, as well as anything upon which an operation may be performed by a subject including data, applications, services, devices, and networks
- An operation is the execution of a function at the request of a subject upon an object. Operations include read, write, edit, delete, author, copy, execute, and modify
- Policy is the formal representation of rules or relationships that define the set of allowable operations a subject may perform upon an object in permitted environment conditions
Source: NIST Special Publication 800-162
- Physical access controls
- Control access to spaces
- Grant or restrict access to facilities, buildings, floors, and rooms
- Logical access controls
- Limit users’ access to information and restrict their access on the system to only what is appropriate for them
- Access controls enable management to:
- Specify which users can access the system Specify what resources they can access
- Specify what operations they can perform
- Enforce individual accountability
- Determining Users
- Who can access a particular system or specific information?
- Giving access involves a trust relationship
- Consistency in access is very important
- Defining resources
- What resources does the user need access to?
- Based on need/role
- Role Based Access Control
- Specifying use
- The level of use and actions permitted by a user of a specific resource
- Common permissions are (RWX)
- Accountability
- Provide evidence for forensics
Access Control Policy
- Access control policy should be based on
- Separation of duties
- Principle of Least privilege
Separation of Duties
- Prevent fraud and errors
- Makes collusion a requirement for committing fraud
- No individual acting alone can compromise the system
- Requires defining the elements of a business process or a job function
Least Privilege
- A user or process should be given no more privilege than necessary to perform a job
- Limits users and processes to access only those resources necessary to perform that job
- Requires that users job be clearly defined
Access Control Requirements
- Reliability – consistent results
- Transparency – reduce user interaction with security system (seen as obstacle to getting work done)
- Scalability/Maintainability
- Integrity/Auditability – provable performance
- Secured Authentication Data
Identity and Access Lifecycle
- Provisioning
- Involves the process when new or existing users require additional access to a resource
- Review
- Involves regular monitoring of the access rights and usage in the form of automated checks and manual audits
- Revocation
- Involves removing some of all of the access rights of an user
Information Classification
- Evaluating the risk level of information to ensure appropriate level of protection
- Establishing a data classification program
- Depends on nature of organization and nature of information in the organization
- Labeling and marking
- Public, internal use only, confidential, restricted
- Data Classification Assurance
- Testing the data classifications
Access Control Threats
- Denial of service
- Distributed denial of service
- Buffer overflows
- Mobile code
- ActiveX, Java applets, scripts
- Malicious software
- Password crackers
Access Control Threats
- Spoofing/masquerading
- Sniffers/Eavesdropping
- Emanations
- Shoulder surfing
- Tapping
- Object reuse
Access Control Threats
- Data remnants
- Unauthorized targeted data mining
- Dumpster diving
- Backdoor/trapdoor
- Theft
- Intruders
- Social Engineering
Physical Controls
- Each zone (area) must have specified physical security controls
- g. perimeter security, data center security, research lab security
- Safe exit must be possible in case of emergency
- Physical entry controls
Technical Controls
- User controls
- Network access
- Remote access
- System access
- Application access
- Malware control
- Encryption
Centralized vs. Decentralized Control
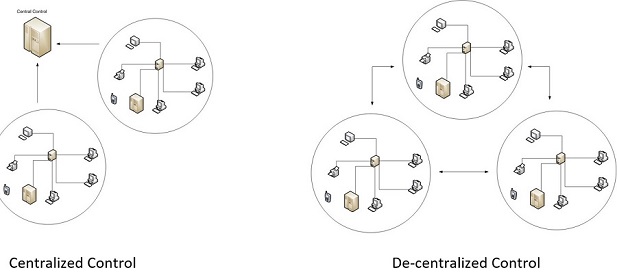
Centralized Control De-centralized Control
Security Domains
- A security domain is based on trust between resources or services in realms (zones) that share a single security policy and single management
- Supports a hierarchical relationship
- The security policy defines the set of objects each user can access
Summary
Cyber Security Homework Help
- Ethical Hacking
- Networking Basics homework assignment help
- Inter process Communication/Threads homework assignment help
- Introduction, Framing homework assignment help
- Error Detection homework assignment help
- Flow Control, Reliability homework assignment help
- Wireless - 802.11 homework assignment help
- Wi-Fi Wireless homework assignment help
- DSL homework assignment help
- PACKET SWITCHING (Network Layer) homework assignment help
- Routing - Link State and homework assignment help
- Distance Vector homework assignment help
- ATM homework assignment help
- PROTOCOL homework assignment help
- Network Hardware homework assignment help
- Internet Connection homework assignment help
- TCP Extensions and homework assignment help
- Performance Enhancements homework assignment help
- TCP/IP Networking homework assignment help
- Bridge homework assignment help
- IPv4, IPv6, ICMP, ARP homework assignment help
- IP Routing - CIDR, OSPF homework assignment help
- Proxy Server / Lists homework assignment help
- Multicast homework assignment help
- DNS homework assignment help
- VPN homework assignment help
- CONGESTION CONTROL homework assignment help
- Congestion Avoidance homework assignment help
- peer to peer (P2P) homework assignment help
- Virtual Clock homework assignment help
- Windows Network homework assignment help
- Bluetooth homework assignment help
- Free Practice Test homework assignment help

