IT Risk and Controls Homework Help
What is Risk?
- Risk is a measure of the extent to which an entity is threatened by a potential circumstance or event, and is typically a function of: (i) the adverse impacts that would arise if the circumstance or event occurs; and (ii) the likelihood of occurrence.
- Information security risks are those risks that arise from the loss of confidentiality, integrity, or availability of information or information systems and reflect the potential adverse impacts to organizational operations (i.e., mission, functions, image, or reputation), organizational assets, individuals, other organizations, and the Nation.
http://csrc.nist.gov/publications/nistpubs/800-30-rev1/sp800_30_r1.pdf
Multi-tiered Risk Management
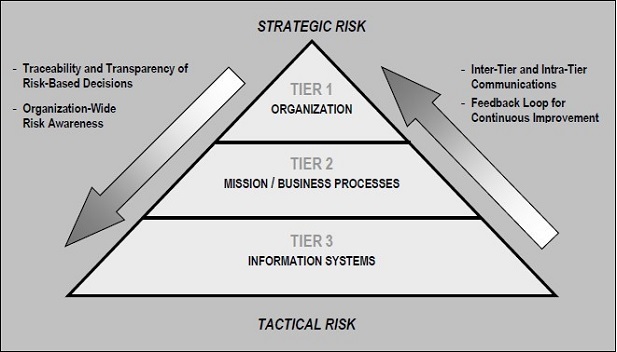
The Risk Management Process
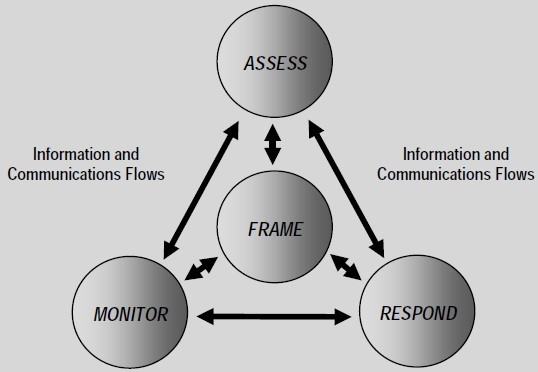
Risk management processes include: (i) framing risk
- assessing risk
- responding to risk and
- monitoring risk
http://csrc.nist.gov/publications/nistpubs/800-30-rev1/sp800_30_r1.pdf
Risk Assessment
- Risk assessment is the process of identifying, estimating, and prioritizing information security risks
- Risk Assessment/Risk Analysis evaluates:
- Threats to assets
- Vulnerabilities present (Vulnerability Assessment)
- Likelihood that a threat will be realized by taking advantage of an exposure
- The impact of the exposure on the organization
- Countermeasures available
- Residual risk
- Risk Assessment can be qualitative or Quantitative
Implemented Controls and Residual Risk
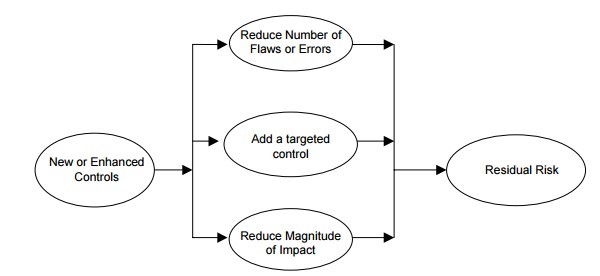
Source: http://csrc.nist.gov/publications/nistpubs/800-30/sp800-30.pdf
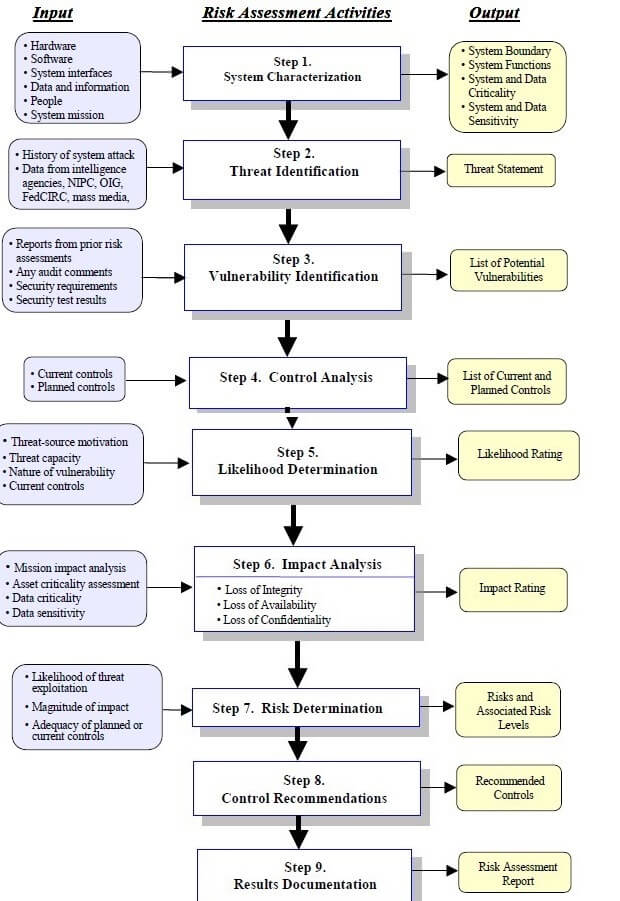
NIST risk assessment methodology flowchart
Risk Factors
- A vulnerability is “a flaw or weakness in system security procedures, design, implementation or internal controls that could be exercised (accidentally triggered or intentionally exploited) and result in a security breach or violation of the systems security policy” (from NIST)
- A threat is “a potential for a particular threat-source to exercise a particular vulnerability” (from NIST)
- The likelihood of occurrence is a weighted risk factor based on an analysis of the probability that a given threat is capable of exploiting a given vulnerability (or set of vulnerabilities)
- The level of impact from a threat event is the magnitude of harm that can be expected to result from the consequences of unauthorized disclosure of information, unauthorized modification of information, unauthorized destruction of information, or loss of information or information system availability.
- Risk Management reduces risks by defining and controlling threats and vulnerabilities
(ISC2)
http://csrc.nist.gov/publications/nistpubs/800-30-rev1/sp800_30_r1.pdf
Likelihood
- A weighted factor based on a subjective analysis of the probability that a given threat is capable of exploiting a given vulnerability or a set of vulnerabilities.
- Likelihood is measured by the capabilities of the threat and the presence or absence of countermeasures (from NIST)
- Likelihood along with impact determines risk
Impact
- Impact Level: The magnitude of harm that can be expected to result from the consequences of risk
- Impact Value: The assessed potential impact resulting from a compromise of the confidentiality, integrity, or availability of an information type, expressed as a value of low, moderate, or high.
- Define terms (i.e. definitions of impact to the organization – loss of life, loss of prestige, loss of money, loss of market share etc)
- Loss of life is the highest priority and is always given the highest impact rating
Rating Likelihood and Impact/Consequences
Likelihood and Consequences rating
|
Likelihood |
|
Consequence |
|
|
Rare (very low) |
E |
Insignificant (low – no business impact) |
1 |
|
Unlikely (low) |
D |
Minor (low – minor business impact, some loss of confidence) |
2 |
|
Moderate (medium) |
C |
Moderate (Medium – business is interrupted, loss of confidence) |
3 |
|
Likely (high) |
B |
Major (High – business is disrupted, major loss of confidence) |
4 |
|
Almost Certain (very high) |
A |
Catastrophic (High – business cannot continue) |
5 |
Likelihood Qualification – how to arrive at a likelihood rating
|
How to Qualify Likelihood |
Rating |
|
Skill (High skill level required à low or no skill required) |
1 = high skill required à 5 = no skill required |
|
Ease of Access (very difficult to do à very simple to do) |
1 = very difficult à 5 = simple |
|
Incentive (high incentive à low incentive) |
1 = low or no incentive à 5 = high incentive |
|
Resource (requires expensive or rare equipment à no resources required) |
1 = rare/expensive à 5 = no resource required |
|
Total (add rating and divide by 4) |
1 = E, 2 = D, 3 = C, 4 = B, 5 = A |
Source: CISSP CBK
Rating likelihood and consequences
Risk Levels
|
|
Consequence: |
| ||||
|
Insignificant |
Minor |
Moderate |
Major |
Catastrophic | ||
|
Likelihood: |
1 |
2 |
3 |
4 |
5 | |
|
A (almost certain) |
H |
H |
E |
E |
E | |
|
B (likely) |
M |
H |
H |
E |
E | |
|
C (possible) |
L |
M |
H |
E |
E | |
|
D (unlikely) |
L |
L |
M |
H |
E | |
|
E (rare) |
L |
L |
M |
H |
H | |
|
E |
Extreme Risk: Immediate action required to mitigate the risk or decide to not proceed |
| ||||
|
H |
High Risk: Action should be taken to compensate for the risk |
| ||||
|
M |
Moderate Risk: Action should be taken to monitor the risk |
| ||||
|
L |
Low Risk: Routine acceptance of the risk |
| ||||
CISSP CBK: ANZ 4360 risk levels
Risk Responses
- Risk Avoidance Risk Transfer
- Risk Mitigation
- Risk Acceptance
- Risk Ownership
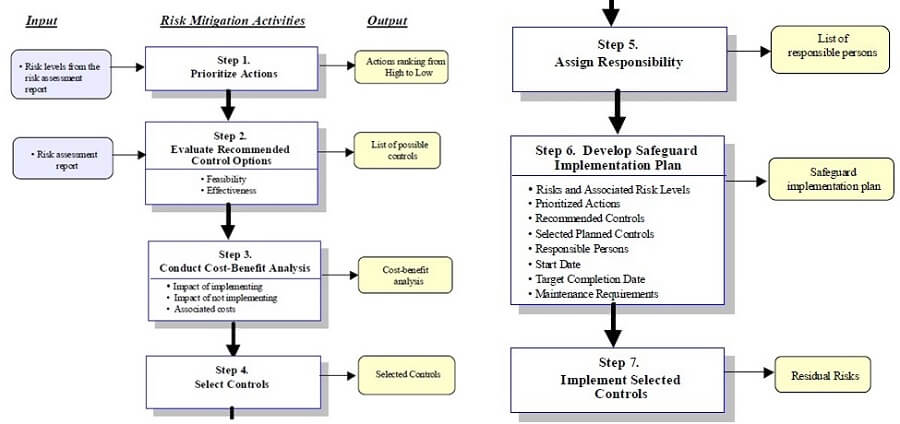
NIST Risk Mitigation action points
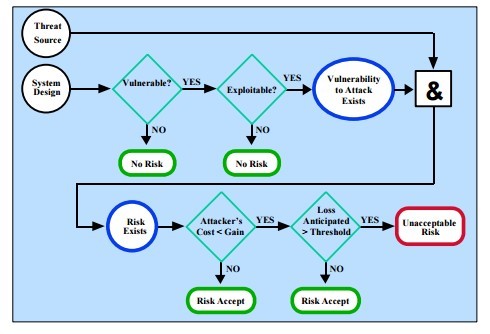
NIST Risk Mitigation methodology flowchart
Due Care and Due Diligence
- Due care describes the care that a “reasonable person” would exercise under given circumstances.
- Lack of due care is often considered negligence and can be prosecuted.
- In other words, neglecting to follow legally mandated requirements may lead to legal exposure.
- Due diligence is a pre-emptive measure made to avoid harm. Due diligence leads to due care.
- Due diligence should be adopted as a core principle by security professionals.
Security Policies
- The security policy defines what the organization needs to accomplish at a high level and serves as management’s intentions to control the operation of the organization to meet business objectives
- Policy summary statement – says why the policy exists
Security Policy Best Practices
- Clearly defined process for policy initiation, creation, review, approval, distribution and communication
- Use forceful, directive wording
- Avoid technology references, technical jargon, specificity and implementation details
- Provide links to supporting documentation
- Conduct management review and signoff
- Employees should explicitly acknowledge policies
- Define policy exception rules
- Review incidents and adjust policies as needed
- Periodic review
- Sanctions for non-compliance
Types of Security Policies
- Organizational or security program policy
- g. protection of PII
- Functional, Issue specific policies
- g. internet usage
- System specific policies
- g. Modifying fields in a check printing application
Lower level/specific policies require frequent updates
Standards
- Standards define the specific requirements for all systems in an organization
- Selected hardware and software mechanisms for controlling security risks.
- Standards ensure consistence and interoperability
- Security standards are the hardware and software security mechanisms selected as the organization’s method of controlling security risks
Security Baselines
- Baselines are descriptions of how to implement the security configuration of hardware and software such that these implementations are consistent across the enterprise
- Baselines are the specific rules necessary to implement the security policy and related organizational standards
- Must be reviewed and tested periodically
Procedures
- Procedures are step by step instructions in support of the policies, standards, guidelines and baselines
- The procedures indicate how the policy will be implemented as well as the responsibilities of the individuals concerned
- Procedures must be documented in a consistent fashion
Guidelines
- Guidelines are optional or discretionary controls used to give individuals a basis to make judgments with respect to security actions
- Anything that is required should not be a guideline. It should be part of the policy or the baseline
- Industry practice documents
- COBIT, CMM, ISO 17799, security guidelines from NSA, NIST
Security Policies, Procedures, Standards, Guidelines and Baselines
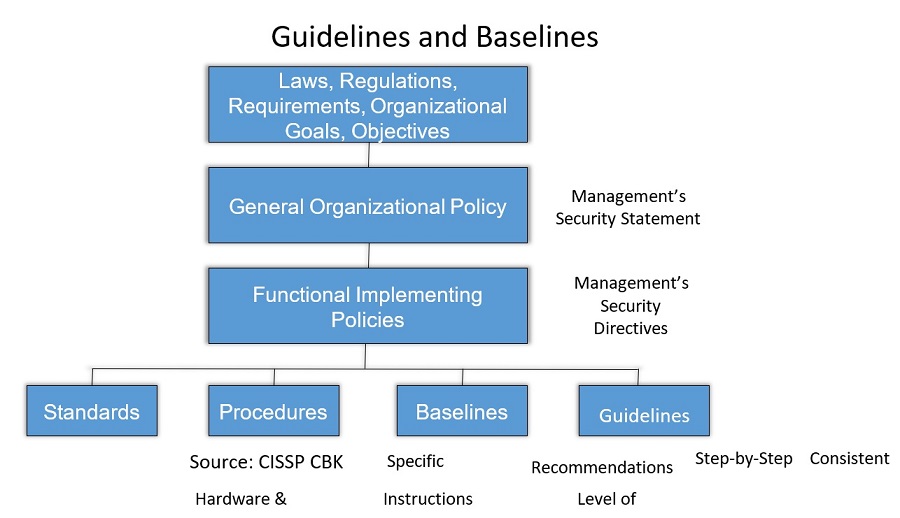
Source: CISSP CBK Step-by-Step Consistent Recommendations
Hardware & Instructions Level of
Software Security
Figure 3.3 Relationships among policies, standards, procedures, baselines, and guidelines
IT CONTROLS
Based on:
Official (ISC)2 Guide to the CISSP CBK
NIST Special Publication 800-53 Revision 4
©Bipin Prabhakar. All rights reserved.
Tier 3 Risk Management Framework
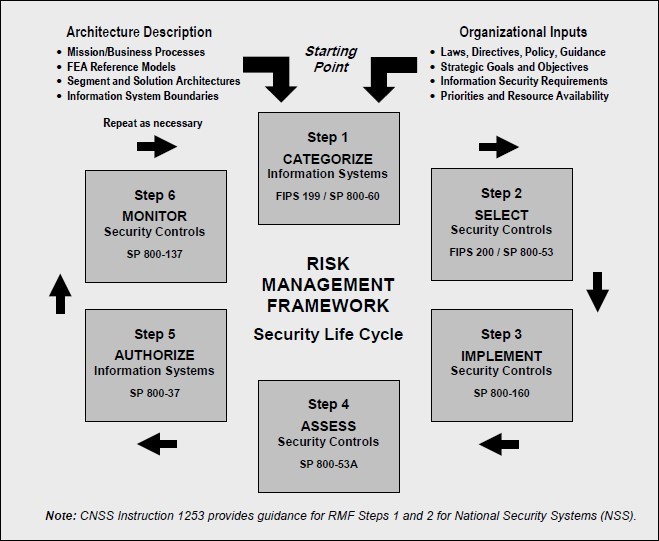
Addressing Tier 3 Risk
- Categorize the information system based on a impact analysis
- Select an initial set of baseline security controls for the information system based on system impact level
- Implement the security controls and document the design, development, and implementation details for the controls
- Assess the security controls to determine the extent to which the controls are implemented correctly, operating as intended, and producing the desired outcome with respect to meeting the security requirements for the system
- Authorize information system operation based on a determination of risk resulting from the operation and use of the information system and the decision that this risk is acceptable
- Monitor the security controls in the information system and environment of operation on an ongoing basis to determine control effectiveness, changes to the system/environment, and compliance to legislation, policies, regulations, and standards.
http://csrc.nist.gov/publications/drafts/800-53-rev4/sp800-53-rev4-ipd.pdf
Security Control Structure
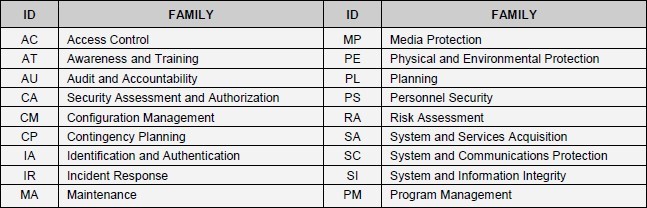
- Security controls have a well-defined organization and structure. They are classified into management, operational, and technical controls, and are organized into 18 families
- They may involve aspects of policy, oversight, supervision, manual processes, actions by individuals, or automated mechanisms implemented by information systems
Security Control Identifiers and Classes
|
Identifier |
Family |
Class |
|
AC |
Access Control |
Technical |
|
AT |
Awareness and Training |
Operational |
|
AU |
Audit and Accountability |
Technical |
|
CA |
Certification, Accreditation, and Security Assessments |
Management |
|
CM |
Configuration Management |
Operational |
|
CP |
Contingency Planning |
Operational |
|
IA |
Identification and Authentication |
Technical |
|
IR |
Incident Response |
Operational |
|
MA |
Maintenance |
Operational |
|
MP |
Media Protection |
Operational |
|
PE |
Physical and Environmental Protection |
Operational |
|
PL |
Planning |
Management |
|
PS |
Personnel Security |
Operational |
|
RA |
Risk Assessment |
Management |
|
SA |
System and Services Acquisition |
Management |
|
SC |
System and Communications Protection |
Technical |
|
SI |
System and Information Integrity |
Operational |
http://csrc.nist.gov/publications/drafts/800-53-rev4/sp800-53-rev4-ipd.pdf
Security Control Structure (contd.)
- Consists of the following components:
- Control section: Prescribes specific security-related activities or actions to be carried out by organizations or by information systems
- Supplemental guidance section: Provides non-prescriptive, additional information for a specific security control
- Control enhancements section: provides statements of security capability to add functionality/specificity to a control and/or increase the strength of a control
- References section: Includes a list of applicable federal laws, policies, regulations, standards, and guidelines relevant to a particular security control
- Priority and baseline allocation section: Provides the recommended priority codes used for sequencing decisions during security control implementation, and the initial allocation of security controls and control enhancements to the baselines
Security Control Baselines
- Baseline controls are the starting point for the security control selection process and are chosen based on the security category and associated impact level of information systems
- NIST 800-53 Rev 4
- Appendix D provides a listing of baseline security controls.
- Appendix F provides a comprehensive catalog of security controls for information systems and organizations, arranged by control families.
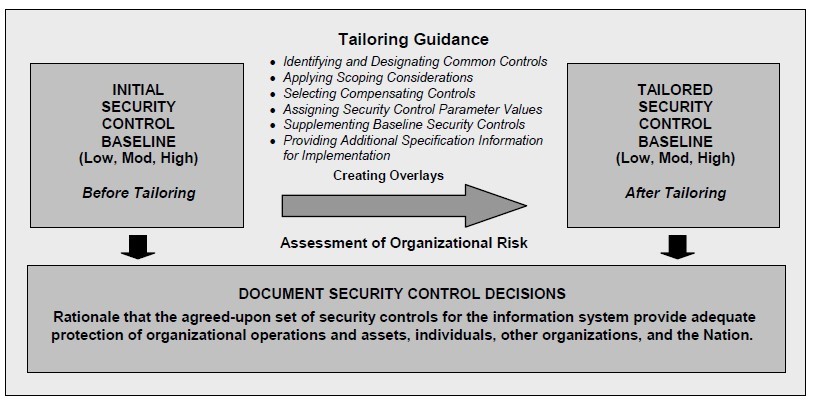
Tailoring Security Control Baselines
- Tailoring guidance helps organizations to customize the security control baselines selected using the results from organizational assessments of risk
- Baseline tailoring actions include:
- identifying and designating common controls
- applying scoping considerations
- selecting compensating controls
- assigning specific values to security control parameters
- supplementing initial baselines with additional security controls or control enhancements
- providing additional information for control implementation
Security Control Designations
- Security Control Designations define
- The scope of applicability for the control ii. The shared nature of the control
iii. The responsibility for control development, implementation, assessment, and authorization
- Security Control Designations include
- Common controls
- System specific controls
- Hybrid controls
Common Controls
- Security controls that are inheritable by one or more organizational information systems
- Security controls are inheritable when the systems / components receive protection from controls but the controls are developed, implemented, assessed, authorized, and monitored by entities other than those responsible for the systems/components
- Controls needed to protect organizational information systems (e.g., security awareness training, incident response plans, physical access to facilities, rules of behaviour) are excellent candidates for common control status
System Specific and Hybrid Controls
- Security controls not designated as common controls are considered system-specific or hybrid controls
- Organizations assign a hybrid status to security controls when one part of the control is common and another part of the control is system-specific
- For example, an organization may choose to implement the Incident Response Policy as a hybrid control, with the policy portion designated as common and the procedures portion designated as system-specific
Controls Types
Controls can be categorized by method of implementation
- Directive or administrative controls
- Physical or operational controls
- Technical or logical controls
Directive Controls
- Provide guidance to personnel as to the expected behavior with respect to security within the organization
- Also known as administrative controls
- The most common examples of directive controls are the organization’s security policies and procedures, personnel security, monitoring, user management, and privilege management
Physical Controls
- Protect the organization’s people and physical environment, such as locks, fire management, gates, and guards
- Physical controls may be called “operational controls” in some contexts
- Physical security is based on the notion of establishing security zones or concentric areas within a facility that require increased security as you get closer to the valuable assets inside the facility
Technical Controls
- Electronic hardware and software solutions implemented to control access to information and information networks.
- Also referred to as logical controls
- Examples are user controls, network access, remote access, system access, application access, malware control, and encryption
Primary technical controls
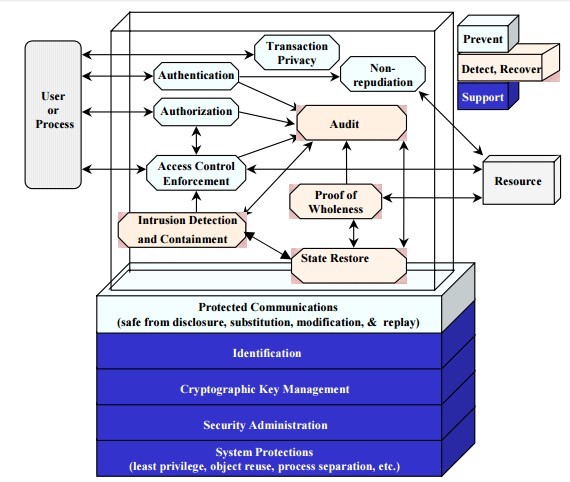
- Support - Supporting controls are generic and underlie most IT security capabilities. These controls must be in place in order to implement other controls.
- Prevent - Preventive controls focus on preventing security breaches from occurring in the first place.
- Detect and Recover - These controls focus on detecting and recovering from a security breach
Source: http://csrc.nist.gov/publications/nistpubs/800-30/sp800-30.pdf
Control Categories
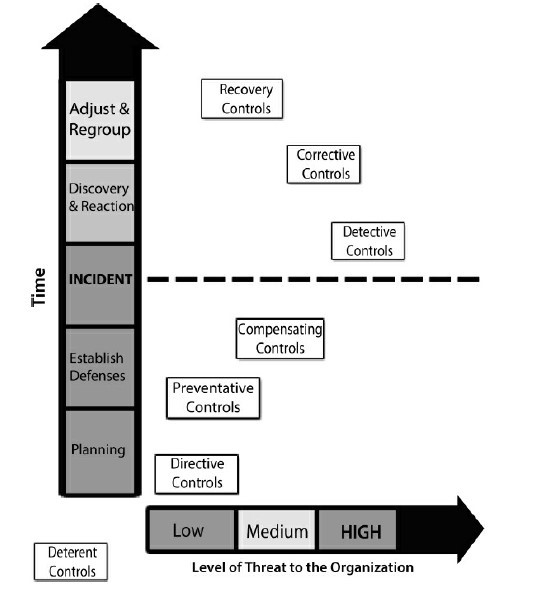
- Deterrent
- Preventive
- Compensating
- Detective
- Corrective
- Recovery
Deterrent Controls
- Controls that act as a deterrent to threats and attacks because the existence of the control is enough to keep some potential attackers from attempting to circumvent the control
- The effort required to circumvent the control is far greater than the potential reward if the attacker is successful, or, conversely, the negative implications of a failed attack (or getting caught) outweigh the benefits of success
- For example, by forcing identification and authentication, the potential for unwanted incidents can be reduced
Preventative Controls
- Controls that keep a user from performing some activity or function
- Differ from deterrent controls in that the control is not optional and cannot be bypassed
- The only way to bypass the control is to find a flaw in the control’s implementation
Compensating Controls
- Introduced when the existing capabilities of a system do not support the requirement of a policy or when a primary control does not mitigate the risk to a level lower than the acceptable risk
- When an existing system does not support the required controls, compensating controls are introduced to supplement the existing environment, closing the gap in controls, meeting policy requirements, and thus reducing overall risk
Detective Controls
- Detective controls warn when something has happened, and are the earliest point in the post-incident timeline
- Detection aspects of access control can range from evidentiary, such as post incident investigations, to real-time alerting of inappropriate activities
- Examples are intrusion detection systems, virus controls, web filtering, network operations administration, and logs and audit trails
Corrective Controls
- When a security incident occurs, corrective controls are applied that alter the security posture of an environment to correct any deficiencies and return the environment to a secure state
- They can range from “quick fix” changes like new firewall rules, router access control list updates, and access policy changes, to more longterm infrastructure changes like the introduction of encryption, movement from single-factor to multifactor authentication for remote access, or the introduction of smart cards for authentication
Recovery Controls
- Recovery controls are applied to ensure that any changes to the control environment get accurately reinstated and returned to normal operations after an incident occurs
- Events can include system outages, attacks, project changes, technical demands, administrative gaps, and full-blown disaster situations
Security Control Selection Process
Trustworthiness
- Trust is the belief that a security-relevant entity will behave in a predictable manner when satisfying a defined set of security requirements under specified conditions/circumstances and while subjected to disruptions, human errors, component faults and failures, and purposeful attacks that may occur
- Trust is usually determined relative to a specific security capability and can be decided relative to an individual system component or the entire information system
- Trustworthiness expresses the degree to which the systems can be expected to preserve the confidentiality, integrity, and availability of the information systems
Security Functionality and Assurance
- Two fundamental components affecting the trustworthiness of information systems are security functionality and security assurance
- Security functionality is typically defined in terms of the security features, functions, mechanisms, services, procedures, and architectures implemented within organizational information systems or the environments in which those systems operate
- Security assurance is the measure of confidence that the security functionality is implemented correctly, operating as intended, and producing the desired outcome with respect to meeting the security requirements for the system
Trustworthiness
Questions?
ERM frameworks
- COSO’s ERM – Integrated Framework
- Australia/New Zealand Standard – Risk Management
- ISO Risk Management - Draft Standard
- The Combined Code and Turnbull Guidance
- A Risk Management Standard by the Federation of European Risk Management Associations (FERMA)
Appendix - Sources
- Official (ISC)2 Guide to the CISSP CBK
- NIST Special Publication 800-53 Revision 4
Information Technology (IT) Resources
- Management information systems
- E-business
- Intranet strategies
- Database management system
- Data warehousing
- Data Mining
- Document warehousing
- Customer relationship management (CRM)
- Sales force management system
- Enterprise content management (ECM)
- Enterprise resource planning (ERP)
- Enterprise Workplace
- Human Resource Management Systems (HRMS)
- Business performance management
- Project management software
- Groupware and collaborative systems
- Information systems development
- Product Lifecycle Management (PLM)
- Computer-aided design (CAD)
- Computer-aided manufacturing (CAM)
- Knowledge management (KMS)
- Business Technology Management (BTM)
- Decision support system (DSS)
- Electronic data processing (EDP)
- Geographic information system
- Material requirements planning
- Strategic enterprise management
- Supply chain management
- Virtual management
- U-commerce

