Managing Complex ICT Networks
Qualification Code/Title
{`ICT50415 : Diploma of Information Technology Networking
National Code/Title
ICTNWK529 - Install and manage complex ICT networks`}
Attempts ALL Questions
PART A - ANALYTICAL SECTIONS
- WAN Design
Please fill out the appropriate boxes in the flowchart with the correct statement from the column on the right side.
2. Network Address Translation
Determine the correct IP Address and place into the NAT Translation table. Host-A and Host-B are both communicating with the WWW server. Router-A is using dynamic NAT with a pool of address assigned by the ISP.
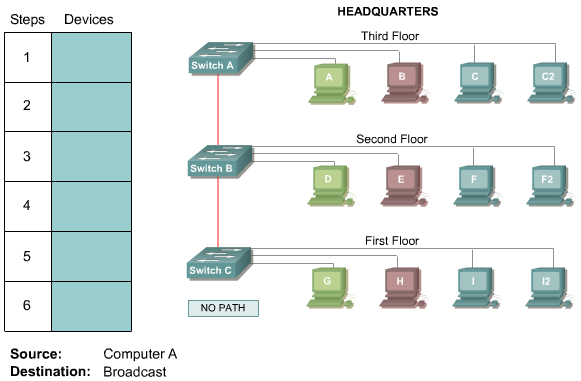
3. VLAN Operation
Complete the boxes with the appropriate device name to determine the path the packet would take from the source to the destination. Select no path if no path is available.
4. Part of the AHIC network is shown below:
Based on the diagram shown above, what kind of cable should be used to make each connection that is identified by the numbers shown?
5. You work as a network administrator at an ABC office. Your boss, Mr Robin, is interested in the CLI commands. Match the commands with the appropriate functions. Not all options are used.
PART B - Short Questions
- List and discuss any two examples of Web Server
- Describing Issues in a Poorly Designed Network.
- What is brute force attack? What policies should you take to minimize this attack?
- List the at least three factors that helps you to evaluate the Network infrastructure.
- Write a Short Notes on:
VOIP
Network Management tools
PART C – Case Study
Scenario 1:
You are working in ABC Company as a Network Engineer. You need to choose a routing protocol for use in
the ABC network that meets the following requirements:
- Routing update authentication
- An addressing scheme that conserves IP addresses
- Multiple Vendors
- A network with Over 50 routers
Which routing protocol fulfils these requirements? Explain it.
Scenario 2:
Nubex Pty Ltd was established just over 6 years ago. Currently, they have employed approximately 200 staff members. They have recently opened an additional office in Canberra in order to expend the business. Due to distance, Company is looking for some solution for remote communication using VOIP so that company can organise meeting using Video conference.
As an IT expert, you need to do following Tasks:
Task 1: Find the appropriate VOIP software that can be installed in Business
Task 2: Install and Configure Appropriate Software and Demonstrate it how to use it for voice chat, Video Conference and Instant Message.
Scenario 3:
In this task you will use a network monitoring tool named Wireshark (formerly known as Ethereal) to read and analyse network trace files. Wireshark is a powerful program to generate and analyse trace files in a network. It has extensive support for a huge number of Internet protocols.
Visit a web site that is password-protected and examine the sequence of HTTP message exchanged for such a site. The URL: https://ahi-elearning.mywisenet.com.au/login/index.php is password protected.
As an IT Expert, you need to do following tasks:
Task 1: Download, install and start up the Wireshark packet sniffer. You can download the Wireshark software from the following link:
https://www.wireshark.org/
Task 2: Make sure your browser’s cache is cleared, and restart your browser.
Task 3: Choose the active interface and ‘Start’ packet sniffing.
Task 4: Enter the following URL into your browser https://ahi-elearning.mywisenet.com.au/login/index.php, type the user name and password into the pop up box.
Task 5: Stop Wireshark packet capture, and enter “http” in the display-filter-specification window, so that only captured HTTP messages will be displayed later in the packet-listing window.
If the username and password that you entered are encoded in the string of characters (d2lyZXNoYXJrLXN0dWRlbnRzOm5ldHdvcms=) following the “Authorization: Basic” header in the clients HTTP GET message. While it may appear that your username and password are encrypted, they are simply encoded in a format known as Base64 format. The username and password are not encrypted! To see this, go to http://www.base64decode.org/ and enter the base64-encoded string d2lyZXNoYXJrLXN0dWRlbnRz into the "Decode from base64" text box and press "Go". Voila! You have translated from Base64 encoding to ASCII encoding, and thus should see your username! To view the password, enter the remainder of the string Om5ldHdvcms= and press decode. Since anyone can download a tool like Wireshark and sniff packets (not just their own) passing by their network adaptor, and anyone can translate from Base64 to ASCII (you just did it!), it should be clear to you that simple passwords on WWW sites are not secure unless additional measures are taken.
Student must demonstrate all Tasks in class and also take the screen shoot of all Tasks as Evidence
Scenario 4:
You are working as IT Support Officer in Nubex Pty Ltd. Due to work load, you are not able to scan antivirus in regular basis. IT Manager has advised you to implement automated virus checking option to the computer.
You need to setup the option to scan computers every Sunday without user interaction.

