Opportunities making business with mobile computing
- Introduction
- Objectives of the project
- Scope of the project
- Literature review
- Research Questions
- Research design and methodology
- Limitations of the research
- Time plan (Refer to Appendix)
- Conclusion
- Reference list
- Appendix
1. Introduction
The enhancement in the field of technology has increased the opportunities for the business organizations to have competitive edge in the global market. Therefore, Gikas and Grant (2013) said that, the business organizations are mainly shifting towards the technological advancement in order to enhance their level of productivity. Earlier, the organizations used the different web-based applications to maintain their business process. However, the increased use of Smartphone brings the use of mobile technology into their business operations. The main aim of this study is to evaluate the importance of the mobile computing in the different business processes of an organization. The study provides a brief description regarding the scope of the entire project along with the proper research design and the methodology that needs to be used in order to conduct the study successfully. In addition to that, the study also provides a detail description regarding the time that is required in order to complete the study. The limitations for the successful conduction for the study have also provided. Go to top
2. Objectives of the project
- To understand the concept of mobile computing
- To evaluate the importance of mobile computing in regards of business firms
- To understand the opportunities of the mobile computing concept regarding the different business firms
- To identify the challenges regarding the mobile computing for the different business firms
- To provide certain solutions regarding the challenges of the mobile computing for the business firms Go to top
3. Scope of the project
As the technology is upgrading day by day, therefore the introduction of the mobile computing has been essential for the business organizations. The organizations need to implement this particular technology in order to enhance their business performance (Rahimi et al. 2014). This particular project mainly enhances the level of knowledge regarding the use of the mobile computing devices and regarding the fact, that how the devices can be helpful for the business organizations. Along with that, the project also provides with a good range of mobile computing devices that can be used in the upcoming days. Moreover, the study also provides the limitations regarding the use of the mobile computing devices along with their advantages. According to Wolf (2014), it mainly allows the business personnel to have a handy amount of knowledge regarding the mobile computing devices and regarding the fact that how these devices can enhance their business performance in the competitive world. Go to top

4. Literature review
The term mobile computing technology is understood as the technology that is being used in the smartphones. However, based on the study of Pejovic and Musolesi (2015), it has been found that the smartphones are the part of the mobile computing technology. Mobile computing is considered as the technology that is mainly used in order to transmit the voice and a set of data through the portable devices by using the wireless networks. It is mainly a distributed system that is mainly used for the communication purpose. This provides the business organizations an ample amount of mobility and the ability to have the computing system at anywhere at any time. There are mainly different sectors where this particular technology can be used such as the E-commerce sites can use this technology for the credit card verification system (Mitra et al. 2015). Along with that, the cabs are also getting booked these days by using the smartphones or the mobile applications. In addition to that, this technology is also getting used in the health sector by developing smart wearable devices that can be used in order to monitor the health condition of an individual.
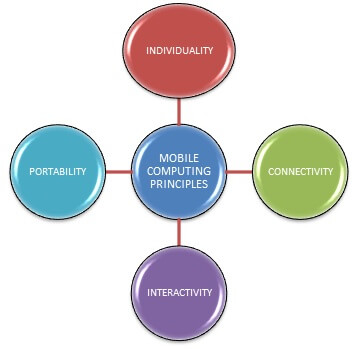
Figure 1: Principles of mobile computing system (Source: Shiraz et al. 2014)
The mobile computing comes with the various principles. Shiraz et al. (2014) said that, one of them is the portability. That signifies the fact that the devices that are connected to the mobile computing system have the feature of mobility. Along with that, the connectivity is another fact that comes under the consideration. It mainly defines the quality of the service regarding the network connectivity. Every mobile computing environment needs to have high network connectivity in order to maintain the smoothness in their processing. In addition to that, the nodes that are connected to the mobile computing environment should have the feature of interactivity. That means they needs to communicate with each other and can have an effective communication process by maintain a healthy transmission of the data set. According to Kim et al. (2013) the mobile computing environment also needs to have the feature regarding the individuality. The system should be able to grasp the technology in order to meet with the individual needs.
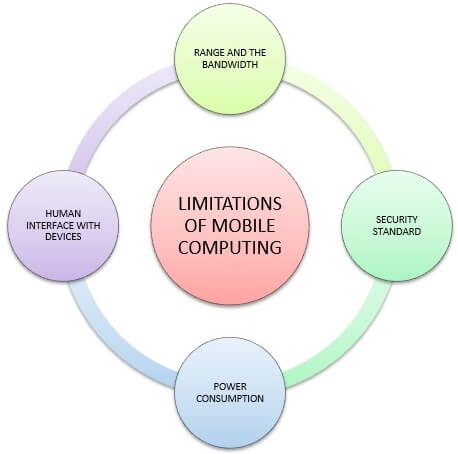
Figure 2: Limitations of the mobile Computing system (Source: Wang et al. 2015)
The mobile computing system has an ample amount of limitations. One of them is regarding the range and the bandwidth of the system. Along with that, the security standard is another factor that needs to be taken under the consideration. While working on the mobile platform, the users are dependent on the public networks and they require a proper use of the VPN. According to Wang et al. (2015), the VPN is vulnerable enough that anyone can attack the VPN as a large number of networks are interconnected to it. In addition to that, the mobile computers are entire dependent on the battery power when there is no availability of the portable generator. Along with that, the screens and the keyboards are getting smaller day by day and that makes it hard to use the device for the users. However, there are alternative actions available regarding these operations such as the speech recognition and the handwriting recognition (Cui et al. 2013).
All the smartphones along with the computers are the target of attacks. The security threats can also exploit the vulnerabilities regarding the software that is used in the mobile devices. Along with that, Yang et al. (2014) said that some malicious software can easily break into a system and take out all the important information regarding an individual or a business organization. However, in order to mitigate the different security issues, the technology is upgrading regularly and it has developed such software products that make the mobile computing environment safe enough for the individuals and the business organizations. According to Cheng et al. (2013), the use of different antivirus can lead to the mitigation of the different security-related issues; however, the software vendor needs to be reliable enough regarding the privacy and the security issues. Go to top
5. Research Questions
Primary question
- Why do the business organizations need to implement the mobile computing technology in their business functions?
Secondary question
- What is the importance of the mobile computing technology regarding the business operations?
- What are the different types of opportunities the business organizations may have after having the mobile computing technology?
- What are the challenges regarding the use of the mobile computing technology?
- What are some possible solutions regarding the challenges of the mobile computing technology? Go to top
6. Research design and methodology
Silverman (2016) said that the research methodology mainly defines the usage of the different tools and the techniques in order to conduct the study successfully. The proper methodology can help the researcher to make the path smooth enough to conduct the study. The researcher should use the proper research philosophy in order to complete the study. The researcher should use the positivism philosophy because of the fact that it is based on the different scientific principles. Along with that, the impact of the mobile computing can be easily evaluated by using the positivist philosophy. In addition to that, the researcher should choose the descriptive design as the appropriate research design. According to Flick (2015), the descriptive design mainly helps the researcher to deal with a large amount of data set that would be gathered from the different primary and secondary sources. The exact presence of the different materials regarding the concept of mobile computing can be properly analyzed by using the descriptive design. When it comes to choosing the research approach, the researcher should use the deductive approach. In this particular approach, the study starts from a general point that is the use of mobile computing and the result is mainly focused on getting the exact reaction regarding the impact of using the mobile computing technology in the different business firms (Taylor et al. 2015).
Qualitative research
When it comes to the qualitative research, the researcher should gather the data set from the managers of the organizations by interviewing them. The researcher should three managers who can provide a proper set of data in order to conduct the study. Therefore, for the qualitative researcher, the sample size would be three managers. The HR Manager, the IT manager and the PR Manager would be those three managers to whom the researcher should go for collecting the data. The researcher should gather the transcripts from the managers and based on that they should analyze the set of data. Along with that, the data that should be gathered from the managers are very much reliable so that the researcher can easily analyze those set of data.
Quantitative research
The quantitative research should be done through the surveys. The surveys needs to be done over the employees of the organization that uses the mobile computing technology in order to enhance their business performance. The researcher should distribute a set of survey questionnaire to the employees that consists the close-ended set of questions. The researcher should use the different statistical tools in order to analyze the collected set of data. After receiving the feedback from the survey questions, the researcher can easily analyze the view of the employees regarding the opportunities of mobile computing technology in the business operations. According to Mackey and Gass (2015), the researcher needs to select a proper sample size, as it is not possible for the researcher to distribute the survey questionnaire to such a large number of populations. The standard sample size would be 50 employees in the organization who have the knowledge regarding the use of the mobile computing technology. As the data that would be gathered from the survey is the primary data, therefore it would be enough authenticate in order to analyze the fact regarding the usage of the mobile computing technology. Go to top
7. Limitations of the research
In order to complete the study, there is certain amount of limitations that needs to be faced by the researcher. Eshet and Bouwman (2015) said that, one of them is the limitation regarding the time frame. In order to analyze the huge set of data that would be gathered from the different primary and secondary sources requires an ample amount of time. Along with that, the process of survey also takes a lot of time. In addition to that, the accessibility to the managers would also be a critical factor. Moreover, in order to conduct the study, it requires a certain amount of budget. It is also considered as a limitation that would be faced during the project period. As the project would use the different expensive quantitative techniques in order to analyze the gathered set of data, therefore it would require a proper funding in order to complete the study. In addition to that, sometimes the managers did not want to provide the proper answers regarding the questions as they have a fear regarding the consequences of the fact. Go to top
8. Time plan (Refer to Appendix)
9. Conclusion
After summing up the entire study, it can be evaluated that the researcher can conduct the study successfully if the proper process has been maintained. Along with that, the study also provides the proper aim of the study along with the objectives and the questions that may arise during the project period. In addition to that, the researcher has also done the analysis of the existing literature in order to gather an ample amount of valuable knowledge regarding the concept of mobile computing in the business firms. It mainly helps the researcher to have depth knowledge regarding the different principles along with the various advantage and the limitations of the mobile computing that may have over the business processing of the organizations. Moreover, the data collection and the analysis of the collected set of data are significant enough to conduct the study successfully. Go to top
10. Reference list
Cheng, X., Huang, X. and Du, D.Z. eds., (2013). Ad hoc wireless networking (Vol. 14). Springer Science & Business Media.
Cui, Y., Ma, X., Wang, H., Stojmenovic, I. and Liu, J., (2013). A survey of energy efficient wireless transmission and modeling in mobile cloud computing. Mobile Networks and Applications, 18(1), pp.148-155.
Eshet, E. and Bouwman, H., (2015). Addressing the Context of Use in Mobile Computing: a Survey on the State of the Practice. Interacting with Computers, 27(4), pp.392-412.
Flick, U., (2015). Introducing research methodology: A beginner's guide to doing a research project. Sage.
Gikas, J. and Grant, M.M., (2013). Mobile computing devices in higher education: Student perspectives on learning with cell phones, smartphones & social media. The Internet and Higher Education, 19(1), pp.18-26.
Kim, C., Park, T., Lim, H. and Kim, H., (2013). On-site construction management using mobile computing technology. Automation in construction, 35(1), pp.415-423.
Mackey, A. and Gass, S.M., (2015). Second language research: Methodology and design. Routledge.
Mitra, K., Zaslavsky, A. and Åhlund, C., (2015). Context-aware QoE modeling, measurement, and prediction in mobile computing systems. IEEE Transactions on Mobile Computing, 14(5), pp.920-936.
Pejovic, V. and Musolesi, M., (2015). Anticipatory mobile computing: A survey of the state of the art and research challenges. ACM Computing Surveys (CSUR), 47(3), p.47.
Rahimi, M.R., Ren, J., Liu, C.H., Vasilakos, A.V. and Venkatasubramanian, N., (2014). Mobile cloud computing: A survey, state of art and future directions. Mobile Networks and Applications, 19(2), pp.133-143.
Shiraz, M., Ahmed, E., Gani, A. and Han, Q., (2014). Investigation of runtime partitioning of elastic mobile applications for mobile cloud computing. The Journal of Supercomputing, 67(1), pp.84-103.
Silverman, D. ed., (2016). Qualitative research. Sage.
Taylor, S.J., Bogdan, R. and DeVault, M., (2015). Introduction to qualitative research methods: A guidebook and resource. John Wiley & Sons.
Wang, Y., Chen, R. and Wang, D.C., (2015). A survey of mobile cloud computing applications: perspectives and challenges. Wireless Personal Communications, 80(4), pp.1607-1623.
Wolf, M., (2014). High-performance embedded computing: applications in cyber-physical systems and mobile computing. Newnes.
Yang, S., Kwon, D., Yi, H., Cho, Y., Kwon, Y. and Paek, Y., (2014). Techniques to minimize state transfer costs for dynamic execution offloading in mobile cloud computing. IEEE Transactions on Mobile Computing, 13(11), pp.2648-2660. Go to top
11. Appendix
| Activities during research | 1st Week | 2nd Week | 3rd Week | 4th Week | 5th Week | 6th Week | 7th Week |
| Selection of research topic | ✔ | ||||||
| The composition of the literature review | ✔ | ||||||
| The methodology followed in the research | ✔ | ||||||
| Collection of primary data for the research | ✔ | ✔ | |||||
| Data analysis and interpretation | ✔ | ✔ | |||||
| Findings | ✔ | ||||||
| Conclusion and Recommendation for the research study | ✔ | ||||||
| Final submission of the research report | ✔ |
Table 1: Timeline of the project Go to top

