ICTNWK529 Install and Manage Complex ICT Networks Assessment
ICT50118 Diploma of Information Technology
Assessment Plan
Assessments for this unit have been developed by taking into account assessment guidelines as provided in the training package and evidence requirements stipulated in this unit of competency. Assessment is an ongoing process of gathering evidence to determine what each student/learner knows, understands and can do in order to inform teaching and support learning of the intended curriculum.
The purposes of this assessment are;
- To collect evidences that demonstrate competency in the performance criteria of the unit and satisfy skill, knowledge and employability skills requirements
- To provide feedback to the learners/trainees indicating the areas of improvement and professional development
- To measure the effectiveness of the delivery plan and evaluate the learning outcomes The required assessment criteria are provided in each assessment task for learner’s information.
Assessment Method
Assessment in this unit is based on assessment and evidence guidelines provided in the unit of competency and the training package. The evidence is generated through summative assessment tasks. However, the role of Formative Tasks is crucial in developing the required skills and knowledge in completing the summative tasks. Formative tasks enable the trainers to evaluate their own delivery and adjust their facilitation based on the outcomes from these tasks. The role of formative assessments is to improve learning and adapt to student needs.
These tasks and activities usually take place throughout the unit and planned in accordance with the summative assessment plan/schedule. The formative tasks are generally referred to as “Portfolio” tasks. Portfolio is a collection of all the formative tasks completed during the learning sessions. The portfolio can be used by students as an evidence of participation or example of work completed as part of their learning.
Formative tasks are not assessed.
For summative tasks, the following assessment methods are available to collect the aforementioned evidence to demonstrate satisfactory performance in this unit;
- Written Assessment Tasks
- Practical/Analytical Tasks
- Test/Examinations
- Projects
- Observation
- Integrated Assessment
The WrittenAssessment Tasks and Tests have been developed to address various parts of Performance Criteria as well as Required Knowledge.
The Practical Tasks are developed to demonstrate competence in Required Skills. These assessment tasks and activities are mostly designed as in-class assessments, enabling the trainers to observe the work being undertaken and completed (i.e. demonstration of a specific/required skill). Practical tasks may also include use of online learning tools, equipment, activities, or use of software. Instructions for practical tasks are generally provided within the task description. However, trainers/assessor may set certain conditions for conducting and observing these tasks.
The Project (Individual or Group based) addresses various aspects of competency standard including Performance Criteria, Required Skills and Employability Skills. The role of the project in assessment strategy is to measure student/trainee competence as a form of Summative Assessment. It demonstrates the efficacy of instructions and learning in the prescribed delivery period by assessing the overall performance of the students/trainees for the purpose of grading/final results.
The Test/Exam is generally designed to test the Required Knowledge component of the unit of competency. It may also be used to reinforce learning and test specific aspects of other part of competency where knowledge of certain processes/procedures is required. A knowledge test may be verbal or written as specified in the task description. Examinations are conducted under set conditions.
Observation forms part of in-class activities, participation in designated group processes, presentation and provides an option where specific skills need to be demonstrated to the assessor.
Some of the assessments in this course may be used as Integrated Assessments; i.e. to use evidence created in one unit/task to determine competency in another unit/task. The concept behind the design of the integrated assessment is to limit repetitive tasks that test the same or similar competency elements in different units of competency.
Assessment can be both a formative and summative process. Formative assessment is used to provide feedback to students and teachers to promote further learning. Summative assessment contributes to the judgement of student learning for competency/award purposes.
Submission of Work
Material submitted for assessment—Word processed reports, essays, projects, etc. must contain student’s name, ID course name. Students are encouraged to name the files according to established procedure. This would typically include a course or unit code, assessment or submission code, and in the case of multiple files an alphanumeric identifier. Multiple files may also be required to be submitted within an enclosing folder (with similar, appropriate naming conventions) or archive format—e.g. zip or rar. Follow submission guidelines in each assessment task for specific instructions. Work submitted for “approval” within this context must demonstrate care and attention to detail, such that the student inspires confidence that the work is being undertaken competently.
Assessment Tasks and Schedule
|
# |
Type |
Assessment Method | |
|
1 |
Design a Network |
Individual |
Observation |
|
2 |
Part A: Configure Cisco Routers for Syslog, NTP, and SSH Operations |
Individual |
Written |
|
Part B: Configure a Network for Secure Operation |
Individual |
Written | |
|
3 |
Install and Manage a Network |
Individual |
Written |
These assessment tasks/activities have been described in detail in the following section. Task schedule to be advised by trainer/assessor based on the lesson and session plans.
Prescribed Text and Resources
Cannon K., Caudle K., and Chiarella A.V., 2008, CCNA Guide to Cisco Networking Fundamentals, CISCO
Lammle T., 2011, CCNA Cisco Certified Network Associate Study Guide (7th Ed.), CISCO
Angelescu S., 2010, CCNA Certification All-In-One For Dummies, For Dummies Online Resources
Cisco Learning Network: https://learningnetwork.cisco.com
Assessment Task 1
Description:
This assessment task is essentially the first part of the overall assessment in this unit. This task is followed by subsequent/progressive tasks leading to the major task of installing and managing a complex network. As such, it is critical that these tasks are undertaken in a prescribed order and in conjunction with learning sessions. Consider the following business scenario and complete the given tasks.
Scenario
ABX is a Legal and Accounting firm with approximately 200 local and international clients ranging from large businesses with complex financial and legal needs to individuals with a modest financial holding. In line with business and statutory requirements there is a formal set of organisational procedures for keeping data secure, confidential and safe. The IT Department has been relatively stable for about six months since the last major upgrade, but some key staffs have moved on and a number of systems admin tasks have built up.
The company has two offices; a 3-story, freestanding headquarters building and a suburban branch office. At the HQ, there’s a cafeteria and conference room on the ground floor, Legal on the second floor and
Accounting on the first floor. There is an open plan work environment, with at least two closed offices on each floor for senior management. There is a workstation in the reception area and in each closed office, and four workstations in the conference room. Individual workstations are scattered around the open plan office to meet business needs.
Until now the HQ and other two offices have had their independent networks. However, with a focus on aligning resources and expanding the client base, the company has decided to set up a Virtual Private Network (VPN) linking HQ to suburban offices. The network will also allow some of the employees to work from home and access company’s network from remote locations.
You have been given the task to design a network design for the company including;
- Hardware requirements
- Software requirements
- Network security requirements
You task will be to;
- Conceptualise and design a network topology for all three sites (3x) identifying all the equipment and protocols
- Research vendor sites for product/equipment specifications and recommend appropriate equipment
- List and articulate network services to be provided
- Identify requirements for implementing the network solution
- Analyse requirements for internal and external security
Ensure that you provide information sheets/specifications of equipment downloaded from vendor sites. Links/references to the sites visited should also be clearly mentioned. Compile all the required information and convert into a service proposal (word processed), with your trainer/assessor playing the role of the client.
Assessment Criteria
The following assessment criteria will be used for marking this assessment task. Ensure that you have addressed all of the criteria in your work;
- The proposal is appropriately structured and presented as a formal document reflecting a real-life practice
- Appropriate headings and sub-headings are used to structure the contents
- The content flow covers all the required elements of the analysis and contains a logical sequence of the topics
- Scope of proposal demonstrates the required extent of research conducted to gather and summarise information
- Network topology takes into consideration company locations and I/O devices
- Separate topologies are developed for each site with an explanation of how these networks integrate and align
- Hardware devices are accurately identified and added based on the network requirements
- Interface, IP Address and Subnet masks are suggested for each device used
- The proposal articulates sources of internal and external security threats and functions and features of available technologies
- Researched and compared vendors to source software or hardware security solutions
- Made recommendations for appropriate equipment with the relevant rationale/justification
- Described network services (e.g. DHCP, FTP, IMAP, POP, NTP, SMB etc.) and related them to business functions (i.e. why and how they will assist business operations)
- Devised strategies for implementing/installing the proposed network solution with a list of resources and timeline
- Provided copies/information sheets are references where available and presented a cohesively written plan within the case scenario context
Submission Guidelines
The proposal must be submitted in a professional, word-processed layout using the document structure suggested above as a guide for key headings.
- Word processed Plan with an assignment cover sheet
- Any supporting documents (e.g. product features, costs etc.) downloaded from external sources Students should upload the assessment tasks on the MEGA Student Portal in the respective unit.
Assessment Task 2
Part A: Configure Cisco Routers for Syslog, NTP, and SSH Operations
Description:
In this task, you will be configuring Cisco Routers for Syslog, NTP, and SSH Operations. Based on the topology diagram and plan completed in Assessment Task 1, you will be required to install and connect at least two of the planned networks.
A sample network diagram is provided below. You may use it as it is in your network design. However, the task context and requirements will apply to any topology used. Accordingly, the given addressing table may be changed according to your network topology. Same equipment labels must be used where possible.
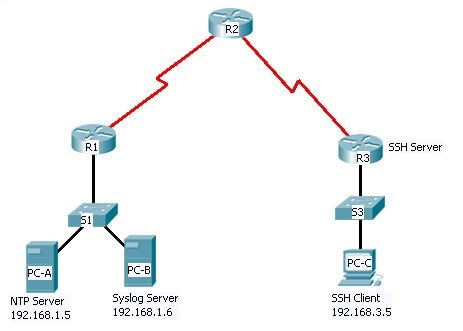
The network topology shows three routers. You will configure NTP and Syslog on all routers. You will configure SSH on R3. Network Time Protocol (NTP) allows routers on the network to synchronise their time settings with an NTP server. The NTP Server is the master NTP server in this lab. You will configure the routers to allow the software clock to be synchronized by NTP to the time server. The Syslog Server will provide message logging in this lab. You will configure the routers to identify the remote host (Syslog server) that will receive logging messages.
R2 is an ISP connected to two remote networks: R1 and R3. The local administrator at R3 can perform most router configurations and troubleshooting; however, since R3 is a managed router, the ISP needs access to R3 for occasional troubleshooting or updates. To provide this access in a secure manner, the administrators have agreed to use Secure Shell (SSH).
You will use the CLI to configure the router to be managed securely using SSH instead of Telnet. The routers have been pre-configured with the following:
- Enable password: ciscoenpa55
- Password for vty lines: ciscovtypa55
- Static routing
Addressing Table
|
Device |
Interface |
IP Address |
Subnet Mask |
Default Gateway |
Switch Port |
|
R1 |
FA0/1 |
192.168.1.1 |
255.255.255.0 |
N/A |
S1 FA0/5 |
|
S0/0/0 (DCE) |
10.1.1.1 |
255.255.255.252 |
N/A |
N/A | |
|
R2 |
S0/0/0 |
10.1.1.2 |
255.255.255.252 |
N/A |
N/A |
|
S0/0/1 (DCE) |
10.2.2.2 |
255.255.255.252 |
N/A |
N/A | |
|
R3 |
FA0/1 |
192.168.3.1 |
255.255.255.0 |
N/A |
S3 FA0/5 |
|
S0/0/1 |
10.2.2.1 |
255.255.255.252 |
N/A |
N/A | |
|
PC-A |
NIC |
192.168.1.5 |
255.255.255.0 |
192.168.1.1 |
S1 FA0/6 |
|
PC-B |
NIC |
192.168.1.6 |
255.255.255.0 |
192.168.1.1 |
S2 FA0/18 |
|
PC-C |
NIC |
192.168.3.5 |
255.255.255.0 |
192.168.3.1 |
S3 FA0/6 |
Note: If a different network topology is used, create your own Addressing table for this task.
Tasks
- Configure routers as NTP clients
- Configure routers to update the hardware clock using NTP
- Configure routers to log messages to the syslog server
- Configure routers to timestamp log messages
- Configure local users
- Configure VTY lines to accept SSH connections only
- Configure RSA key pair on SSH server
- Verify SSH connectivity from PC client and router client
Assessment Criteria
Note: Ideally, the same equipment labels as in the sample diagram must be used. However, if different labels are used, the following criteria must be manually altered for respective student works.
The following assessment criteria will be used for marking this assessment task. Ensure that you have addressed all of the criteria in your work;
- Tested Connectivity
- Pinged from PC-C to R3
- Pinged from R2 to R3
- Telnet from PC-C to R3; Exited the Telnet session
- Telnet from R2 to R3; Exited the Telnet Session
- Verified client configuration using the command show ntp status
- Configured R1, R2 and R3 to periodically update the hardware clock
- Configured timestamp service for logging on the routers
- Configured the routers to identify the remote host (Syslog Server) that will receive logging messages
- Verified logging configuration using the command show logging
- Configured a domain name
- Configured users for login from the SSH client on R3
- Configured the incoming VTY lines on R3
- Erased existing key pairs on R3
- Generate the RSA encryption key pair for R3
- Verified the SSH configuration
- Verified that the authentication timeout and retries are at their default values of 120 and 3
- Configured SSH timeouts and authentication parameters
- Attempted to connect to R3 via Telnet from PC-C (this connection should fail, since R3 has been configured to accept only SSH connections on the virtual terminal lines)
- Connected to R3 using SSH on PC-C
- Connected to R3 using SSH on R2
- Checked results and ensured complete functionalities between routers
Submission Guidelines
This is a practical task and must be completed in presence of an assessor on the designated sessions.
Assessments will be marked by observation; Assessor is satisfied that all the tasks are completed as required.
Part B: Configure a Network for Secure Operation
Description:
Consider the following network diagram. This topology is provided as a sample, which will be replaced by your own topology developed in Assessment Task1. You may use it as it is in your network design. However, the task context and requirements will apply to any topology used. Accordingly, the given addressing table may be changed according to your network topology. Same equipment labels must be used where possible.
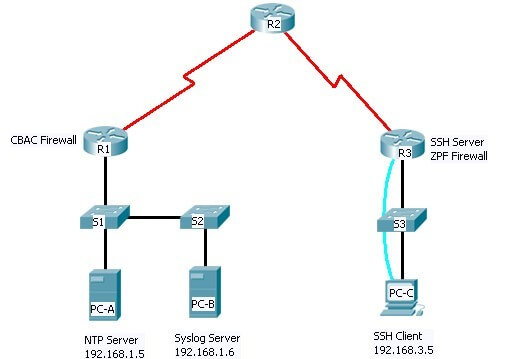
Task
In this comprehensive practice activity, you will apply a combination of security measures;
- Secure the routers with strong passwords, password encryption and a login banner
- Secure the console and VTY lines with passwords
- Configure local AAA authentication
- Configure SSH server
- Configure router for syslog
- Configure router for NTP
- Secure the router against login attacks
- Configure CBAC and ZPF firewalls
- Secure network switches
In the topology, R1 is the edge outer for the Company A while R3 is the edge router for Company B. These networks are interconnected via the R2 router which represents the ISP. You will configure various security features on the routers and switches for Company A and Company B. Not all security features will be configured on R1 and R3.
The following pre-configurations have been made:
- Hostnames on all devices
- IP addresses on all devices
- R2 console password: ciscoconpa55
- R2 password on VTY lines: ciscovtypa55
- R2 enable password: ciscoenpa55
- Static routing
- Syslog services on PC-B
- DNS lookup has been disabled
- IP default gateways for all switches
Addressing Table
|
Device |
Interface |
IP Address |
Subnet Mask |
Default Gateway |
Switch Port |
|
R1 |
FA0/1 |
192.168.1.1 |
255.255.255.0 |
N/A |
S1 FA0/5 |
|
S0/0/0 (DCE) |
10.1.1.1 |
255.255.255.252 |
N/A |
N/A | |
|
R2 |
S0/0/0 |
10.1.1.2 |
255.255.255.252 |
N/A |
N/A |
|
S0/0/1 (DCE) |
10.2.2.2 |
255.255.255.252 |
N/A |
N/A | |
|
R3 |
FA0/1 |
192.168.3.1 |
255.255.255.0 |
N/A |
S3 FA0/5 |
|
S0/0/1 |
10.2.2.1 |
255.255.255.252 |
N/A |
N/A | |
|
PC-A |
NIC |
192.168.1.5 |
255.255.255.0 |
192.168.1.1 |
S1 FA0/6 |
|
PC-B |
NIC |
192.168.1.6 |
255.255.255.0 |
192.168.1.1 |
S2 FA0/18 |
|
PC-C |
NIC |
192.168.3.5 |
255.255.255.0 |
192.168.3.1 |
S3 FA0/6 |
Note: If a different network topology is used, create your own Addressing table for this task.
Assessment Criteria
Note: Ideally, the same equipment labels as in the sample diagram must be used. However, if different labels are used, the following criteria must be manually altered for respective student works.
The following assessment criteria will be used for marking this assessment task. Ensure that you have addressed all of the criteria in your work;
- Tested Connectivity and Verify Configurations
- Verified IP addresses
- Verified routing tables
- Tested connectivity
- Secured the Routers
- Configured an enable secret password on router R1 and R3
- Encrypted plaintext passwords
- Configured the console lines on R1 and R3
- Prevented console messages from interrupting command entry
- Configured vty lines on R1
- Set the login authentication to use the default AAA list
- Configured login banner on R1 and R3
- Configure the local user database
- Enabled AAA services
- Implemented AAA services using the local database
- Configured NTP
- Enabled NTP authentication on PC-A
- Configured R1 as an NTP Client
- Configured routers to update hardware clock
- Configured R1 as Syslog Client
- Configured R1 to timestamp log messages
- Configured R1 to log messages to the syslog server
- Secured Router against Login Attacks
- Logged unsuccessful login attempts to R1
- Telnet to R1 from PC-A
- Telnet to R1 from PC-A and check syslog messages on the syslog server
- Configured SSH on R3
- Configure a domain name
- Configure the incoming vty lines on R3
- Configure RSA encryption key pair for R3
- Configured SSH timeouts and authentication parameters
- Configured CBAC on R1
- Created an inspection rule to inspect ICMP, Telnet and HTTP traffic
- Configured ZPF on R3
- Created the firewall zones
- Created an ACL that defines internal traffic
- Created a class map referencing the internal traffic ACL
- Specified and applied firewall policies
- Secured the Switches
- Secured trunk ports on S1 and S2
- Tested SSH configuration
- Verified timestamps, NTP status for R1 and PC-A
- Verified port security
- Checked and verified all results
Submission Guidelines
This is a practical task and must be completed in presence of an assessor on the designated sessions.
Assessments will be marked by observation; Assessor is satisfied that all the tasks are completed as required.
Assessment Task 3
Description:
This summative task combines all the work done is Assessment Tasks 1&2. In this final task, you will use the topologies installed in Assessment Tasks 2 (part A&B) to finalise your integrated network comprising multiple network services. Ensure that when setting up the network, you resolve the interoperability issues. For the purpose of this task, you trainer/assessor will play the role of your supervisor and provide inputs and advice where needed.
In this task, you will be required to install and test a Virtual Private Network (VPN) using SSH and PPP. Ideally, you will use SSH to create a tunnel connection, and then use PPPD to run TCP/IP traffic through it. An example network is provided below.
\ \
-------- / / --------
Remote ______| Client |______\ Internet \_____| Server |______ Private
Network | Router | / / | Router | Network
-------- \ \ --------
/ /
Client Router
----------------------------------------------------
| /-> 10.0.0.0/255.0.0.0 \ |
Remote | |--> 172.16.0.0/255.240.0.0 |--> Tunnel >---\ |
Network >---|--|--> 192.168.0.0/255.255.0.0 / |--|----> Internet
192.168.12.0 | | | |
| \-----> 0.0.0.0/0.0.0.0 --> IP Masquerade >--/ | ----------------------------------------------------
Server Router
----------------------------------------------------
| /-> 10.0.0.0/255.0.0.0 \ |
| /--> Tunnel >--|--> 172.16.0.0/255.240.0.0 |--|----> Private
Internet >--|--| \--> 192.168.0.0/255.255.0.0 / | Network
| | | 172.16.0.0/12
| \-----> 0.0.0.0/0.0.0.0 -----> /dev/null | 192.168.0.0/16
----------------------------------------------------
Security is very important for a VPN. Ideally, you should be disallowing all passwords and instead do all authentication on the network via SSH's public key authentication system. Accordingly, you will need to configure SSHD.
Note: There might be alternative ways to create a VPN (e.g. IP Sec, PPTP, CIPE). Discuss your plan with your trainer/assessor and obtain prior approval for your implementation. VPN design may also depend on the equipment available in the lab.
Task
Ensure that you address the following requirements;
- Check and install cabling and associated components
- Install and configure servers, routers, switches or other devices to provide internet protocol (IP) addressing, routing, name resolution, and the required network services
- Give each remote office a class C network range to allow them to expand as necessary (e.g. Reserve the 192.168.10.0 and 192.168.11.0 nets)
- Reserve another class C (e.g. 192.168.40.0) to allow each employee/client their own internal IP 5. Set routes on the Cisco such that traffic headed to these reserved nets goes to your VPN server (e.g. 192.168.40.254)
- Name the external interface of the server vpn.company.com, and the internal vpninternal.company.com
- Analyse and resolve interoperability issues
- Rectify networking and security conflicts arising from integrating services
- Install and use appropriate network management tools to evaluate network performance
- Once the VPN setup is completed, set a VoIP service using a CISCO DSL VoIP router (Enable PPPoE on the router's web-based setup page)
- Test network functionality
- Write a brief report on your network design, network services, functionality, and security aspects
Assessment Criteria
The following assessment criteria will be used for marking this assessment task. Ensure that you have addressed all of the criteria in your work;
- Connected all the equipment and assets as per the network topology
- Network topology is according to assumed branch/company locations a
- Separate topologies are developed for each site with an explanation of how these networks integrate and align
- Hardware devices are accurately identified and installed based on the network requirements
- Checked and secured all the cabling
- Essential network services including internet protocol (IP) addressing, routing, name resolution, are verified and tested
- Set up and named the VPN as required
- The network is fully functional
- Tested network protocols, connectivity and resolved issues, if any, including interoperability issues
- Provide the required class C network ranges for branches offices and individual employees
- Used the available network management tool to evaluate and test network performance
- Captured and analysed network performance data
- Implemented network and security policies as defined
- Tested network security and optimised settings, if needed
- Installed appropriate network management tools to optimise and enhance the network
- Conducted network functionality test and recorded the test data
- Provided a concise report on network services, functionality, and security aspects
- Demonstrated the ability to research, collect, analyse and use technical information and specifications
- Demonstrated the ability to design, install and test a complex network

