BIT232 Systems Design And Development
Assignment 3 - System Design Report
EXECUTIVE SUMMARY
The Spring Breaks ‘R’ US Travel service (SBRU) is an online travel service that is designed to book the trips for springs break for university students. Many students book the trips through this conventional system but due to change in technology the business is shifted towards the online service system. The basic idea for such a system is that to facilitate the students in booking a room in resort for making their breaks awesome and enjoyable. There are tons of states with which SPRU contract with, in-order to book a resort for the students. Its website gives the information about the resorts, their prices, rooms that are available, resort information updates and other special features. Students can search for the room of their choice and place the order. It also gives the travel information for students who booked a resort after they are login into the system. There is also need for resort to access information from the SBRU system. They need to update regard the weekly booking orders, type of room that are booked, price details etc. before the season starts they should enter information of resorts, their prices and other features. They are also responsible to make a report for the damage created by the spring breakers during their stay.
FIRST-CUT DESIGN CLASS DIAGRAM (DCD):
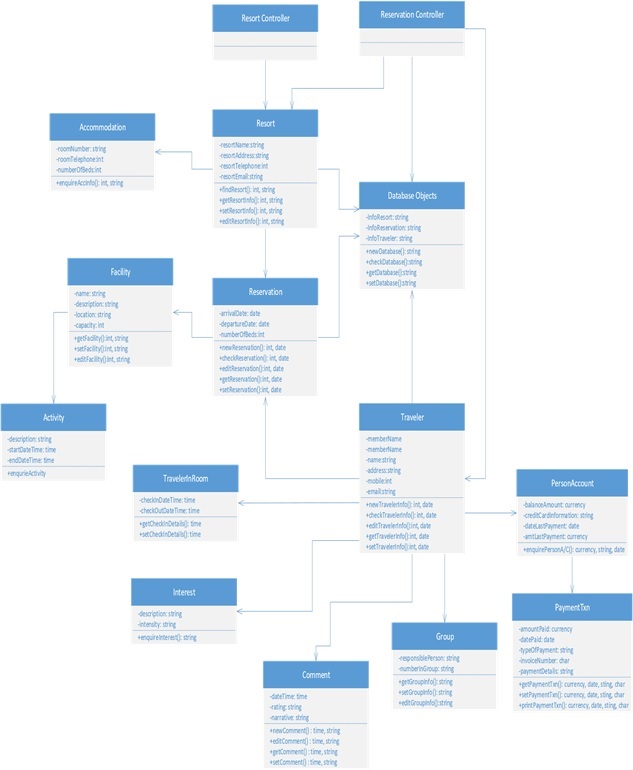
First-cut design class diagram for Spring Breaks ‘R’ Us (SBRU) system using domain classes:
- The class belong to the use cases of the SBRU system identified in Assignment 1 is elaborated as First-cut DCD.
- The first-cut DCD is created by elaborating the attributes in the classes with their type information.
- Then, by providing some logical navigation visibility between the classes, the first-cut DCD can be developed efficiently.
- Navigation visibility is provided using arrow between the classes in the first-cut DCD.
FIRST-CUT CLASS DIAGRAM SBRU:
BOOK A RESERVATION ➔
EXPLANATION:
The above first-cut DCD consists of two controllers, they are:
o Resort Controller o Reservation Controller
The classes belong to the SBRU system’s First-DCD diagram are:
- Resort
- Accommodation
- Reservation
- Facility
- Traveller
- Comment
- Group
- Person Account
- Payment Txn
- Traveller In Room
- Interest
- Activity
Resort Controller Class:
- The controller Resort Controller is the class which communicates with the actor and Resort class.
Reservation Controller Class:
- The controller Reservation Controller is the class which communicates with the system classes Resort and Traveller of the SBRU system.
Resort Class:
- The Resort class returns the name, address, telephone and email ID of the resort.
- This class should be visible to controller classes Resort Controller and Reservation Controller to return the information.
Accommodation Class:
- The Accommodation class returns the room number, telephone number, and number of beds in the resort to the Resort class.
- This class should be visible to Resort class to return the information.
Facility Class:
- The Facility class returns the facility name, description, location and capacity of the facility to the Resort class.
- This class should be visible to Resort class to return the information.
Activity Class:
- The Activity class returns the description about the activity, starting and ending date and time information to the Facility class.
- This class should be visible to Facility class to return the information.
Reservation class:
- The Reservation class returns the traveller’s arrival and departure date and number of beds they needed to the Resort class.
- This class should be visible to Resort class to return the information.
Traveller Class:
- The Traveller class returns the traveller’s name, address, telephone and email ID to the Resort class.
- This class should be visible to Resort class to return the information.
Person Account Class:
- The Person Account class returns the balance amount, commission check information, last payment date and last payment amount to the Traveller class.
- This class should be visible to Traveller class to return the information.
Payment Txn Class:
- The PaymentTxn class returns the amount paid by the traveller, date of amount paid, mode of payment, and then payment details to the Person Account class.
- This class should be visible to Person Account class to return the information.
Traveller In Room Class:
- The Traveller In Room class returns the check in and check out information to the Traveller class.
- This class should be visible to Traveller class to return the information.
Interest Class:
- The Interest class returns the description and intensity of the students to Traveller class.
- This class should be visible to Traveller class to return the information.
Comment Class:
- The Comment class returns the date and time of travel, ratings about the resort and feedback of the resort to Traveller class.
- This class should be visible to Travellers Account class to return the information.
Group Class:
- The Group class returns the responsible person of the student’s group and number of students in the group to the Traveller class.
- This class should be visible to Traveller class to return the information.
ADD A RESORT ➔
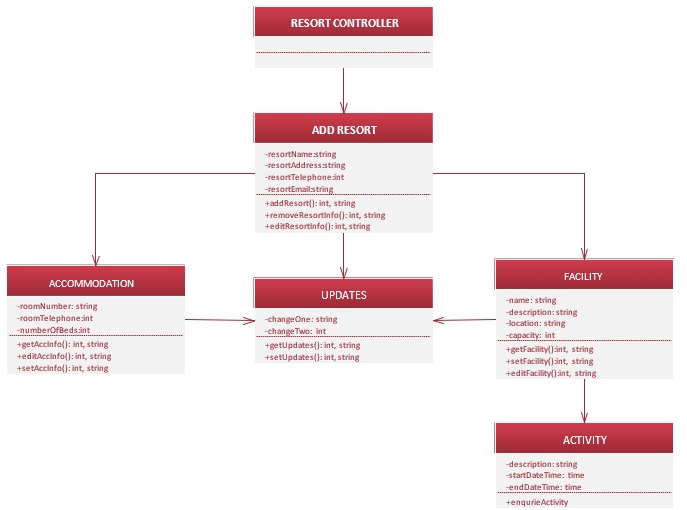
EXPLANATION:
The above first-cut DCD consists of one controllers, it is:
o Resort Controller
The classes belong to the SBRU system’s First-DCD diagram are:
- Add Resort
- Accommodation
- Facility
- Activity
- Updates
Resort Controller Class:
- The controller Resort Controller is the class which communicates with the actor and Resort class.
Add Resort Class:
- The Resort class returns the name, address, telephone and email ID of the resort.
- This class should be visible to controller classes Resort Controller and Reservation Controller to return the information.
Accommodation Class:
- The Accommodation class returns the room number, telephone number, and number of beds in the resort to the Add Resort class.
- This class should be visible to Add Resort class to return the information.
Facility Class:
- The Facility class returns the facility name, description, location and capacity of the facility to the Add Resort class.
- This class should be visible to Add Resort class to return the information.
Activity Class:
- The Activity class returns the description about the activity, starting and ending date and time information to the Facility class.
- This class should be visible to Facility class to return the information.
Updates Class:
- The Updates class returns the changes of the facility and accommodation to the Add Resort class.
- This class should be visible to Add Resort class to return the information.
FIRST-CUT DESIGN SEQUENCE DIAGRAM OF SBRU SYSTEM:
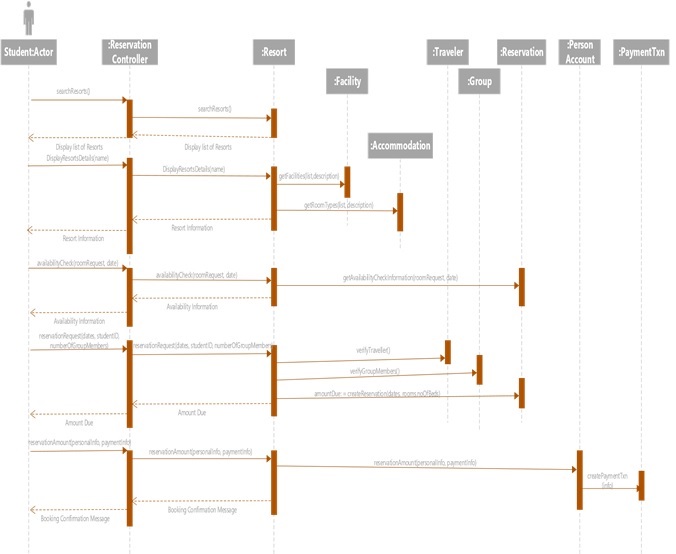
SEQUENCE DIAGRAM FOR BOOKING SYSTEM:
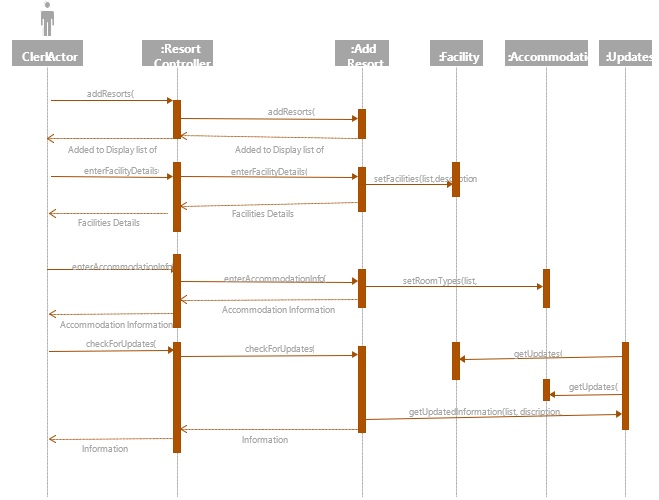
SEQUENCE DIAGRAM FOR ADD RESORT SYSTEM:
SECURITY
Security is a big concern currently in information technology more than ever. As more and more tasks are performed online it is making life easier. At the same time risk as data theft and identity theft are increased as well. Spring Breaks R Us are going to use social networking to benefit their business same as any other company nowadays. To provide a secure and trustworthy experience to the customers here are some suggestion from security point of view.
Security will be providing to Spring Breaks U Us by implementing integrity controls and security controls.
INTEGRITY CONTROLS
Integrity controls are associated with the applications and database. Integrity control make sure the system is functioning in a right manner. It achieves it by rejecting and or preventing invalid and unauthorized data input. It protects data and application from malicious attacks. It allows only appropriate and correct business transactions. Ensures that the transactions are processed correctly and recorded accordingly. It protects the asset of the organization.
Integrity control achieves its goal by implementing following controls in the organization.
INPUT CONTROLS:
It controls the data input in the system and application. It ensures only valid data is being entered by users. It is generally implemented on application or database schema.
ACCESS CONTROLS:
Access control basically restrict a person or program to make changes to data which they are not authorized to access or edit. Access control implemented in DBMS applies control each time when an attempt is made to edit or read any data.
TRANSACTION LOGGING:
Transaction logging keeps a track of all the changes made to the database with the relevant information such as user id, time, date, data input etc. Generally, it is stored separately to keep track of changes made to the database and look for any irregularities in the data. Transaction logging achieves two important goals, one it prevents malicious database changes as it will be recorded in the log. And the other is providing a recovery point. Transaction logging can provide an exact time and date where data was manipulated so it makes it easy to recover unaltered data.
BACKUP
Backup of data can be partial or full. It copies data from the database and store in a removable storage offsite. It can’t be accessed by application software. When In need for a recovery of data back up is being used and the data from the backup is transferred to the database.
OUTPUT CONTROLS
Output controls manage the output of the data whether its been printed physically or displayed on an output device. It ensures that output is being displayed at the current location and is not being accessed by an authorized person.
SECURITY CONTROLS
Security controls are associated with operating systems and network. It ensures the security and integrity of network and operating systems. It mainly focuses on external threats to the organization. It protects information and transactions across the internet. Security controls use following to ensure the security of data in network.
ACCESS CONTROLS
Access control is a part of security control as well. It allows authorized users to use servers, files, database etc accordingly to their privileges. Access control rely on some of these processes. Authentication, access control list (White list), authorization.
ENCRYPTION
Encryption Users will be providing their sensitive information such banking details, date of birth, address, phone numbers and such. In this case all the data must be protected from unauthorized use. Encryption is a security technique to secure such data from malicious use. Encryption is a process to convert the data from its original format to encrypted format using encryption algorithm and encryption keys. Encrypted data can only be accessed by authorized users with a decryption key to decrypt the data to its original format.
SECURE TRANSACTIONS
Secure transactions of data is possible with protocols and methods like Transport layer Security, IP Security and Secured Hypertext Transport Protocol.
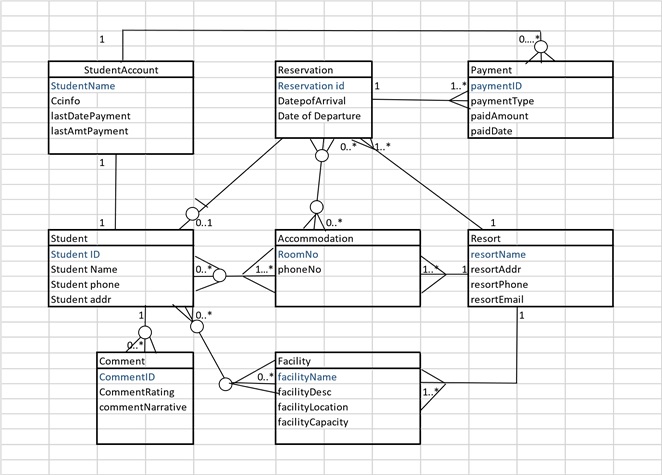
DATABASE SCHEMA
IMPLEMENTATION
During changeover, a new system and an existing system run side by side for an agreed period. This should be long enough to ensure that all aspects of the new system have been confirmed that it can work properly. Both input the same data and perform the same processes. This will compare their output and prove the reliability of the new system. If the new system is accepted, the existing system will stop running and will be replaced by the new one. If both old and new systems are computerized, the input data can be held on a disk or tape and run concurrently on both systems.
DIRECT CONVERSION
As students must deal with the new system so these are the following instructions they need to follow:
All the old data need to be backup into hard drive or into the cloud.
Multiple servers should be installed, so if the server went down they can use the other one.
A different type of room is needed because sometimes a student need to be added due to the change of group size
Payment method should be secure and need to be under peer to peer transaction using 256 bitencryptions to prevent attacks from hackers.
A secure internet connection is needed so that student can get access to the internet all the time and it won’t affect their performance
ADVANTAGES
Allow backups of data to be taken and easy restore.
To prevent all the system from failing down risk should be reduced.
DISADVANTAGES
Budget failure can affect the project.
Server breakdown.
PROJECT MANAGEMENT
RISK TABLE
Risk1 Old data may loss as they have no backup
Risk2 Possibility of redundancy as there has no unique ID when any student get register with website
Risk3 There is no perfect design for social networking
Risk4 Server breakdown
Risk5 Lost of recent student data
Risk6 Budget risk
Risk7 Lack of security
Risk8 Accounting and financing bank transfer hack chances
As there are few risks we are going to focus on reducing its impact and chance of occurring.
MITIGATION OF RISKS
Risk1: In order to avoid data loss, we can enter the entries into the database of old students while going on web services
Risk2: In order to avoid redundancy every student must represent by unique primary key which should be always different for each student
Risk3: If we want a social networking feature into your system. It is very complex process. As it requires whole new design and the process is expensive. we need to re-code whole system with new backup servers
Risk4: There are huge possibilities of server breakdown with numerous possibilities like wires getting broken or some servers or some hardware problems so, there always should be a backup of server on cloud storage.
Risk5: To prevent this risk day by day backup should be needed or all the data should be save in secure hard drives
Risk6: There is a possibility to go over budget we should control the budget and prevent it from going over the limits
Risk7: In order to prevent website from breakdown and other threating attacks from hackers. There should be use of better form of fire-walls and SSID certificates
Risk8: While making transactions it should always be peer to peer transaction using 256 bit-encryption
EFFECT OF RISK
Risk1 Once data loss if you do not have backup will resulting in loosing all the information and bank transactions resulting in huge loss of money Risk2 Possibility of redundancy.
Risk3 if there is no social networking it will be hard to run a system.
Risk4 Server breakdown leads to website crash and may even have possibilities to loss all the database
Risk5 Lack of security leads to stealing of confidential data
Risk6 Budget failure can collapse the project
Risk8 If there is no proper encrypte and look whole into network can give chance to hackers to steal money from student bank accounts
REFERENCES
Satzinger, J., Jackson, R. and Burd, S. (2012). Systems analysis and design in a changing world. Boston, MA: Course Technology, Cengage Learning
Altshuler, Y. (2014). Security and privacy in social networks. [Place of publication not identified]: Springer
Buy BIT232 Systems Design And Development Answers Online
Talk to our expert to get the help with BIT232 Systems Design And Development to complete your assessment on time and boost your grades now
The main aim/motive of the management assignment help services is to get connect with a greater number of students, and effectively help, and support them in getting completing their assignments the students also get find this a wonderful opportunity where they could effectively learn more about their topics, as the experts also have the best team members with them in which all the members effectively support each other to get complete their diploma assignments. They complete the assessments of the students in an appropriate manner and deliver them back to the students before the due date of the assignment so that the students could timely submit this, and can score higher marks. The experts of the assignment help services at urgenthomework.com are so much skilled, capable, talented, and experienced in their field of programming homework help writing assignments, so, for this, they can effectively write the best economics assignment help services.
Get Online Support for BIT232 Systems Design And Development Assignment Help Online
Resources
- 24 x 7 Availability.
- Trained and Certified Experts.
- Deadline Guaranteed.
- Plagiarism Free.
- Privacy Guaranteed.
- Free download.
- Online help for all project.
- Homework Help Services
Testimonials
Urgenthomework helped me with finance homework problems and taught math portion of my course as well. Initially, I used a tutor that taught me math course I felt that as if I was not getting the help I needed. With the help of Urgenthomework, I got precisely where I was weak: Sheryl. Read More

