SIT763 Cyber Security Assignment Help

Avail High Quality SIT763 Cyber Security Assignment Help from IT Experts
Task:
Assessment 1: individual problem-solving task 1
Problem-Solving Task 1 Details
Learning outcomes
In this assignment, you will be focusing on the following unit learning outcome (ULO):
ULO2: Assess security risks, threats and vulnerabilities to the organisation and implement appropriate information security protection mechanisms by analysing requirements, plans and IT security policies.
This ULO will contribute to three of your Deakin graduate learning outcomes (GLOs) in the form of discipline knowledge (GLO1), critical thinking (GLO4) and problem solving (GLO5).
Brief description of assessment task
This task requires you to demonstrate the ability to conduct an investigation of security management issues in corporate organisations based on the background information provided below and write a report.
In your report, you will be required to follow prescribed procedures to evaluate risk levels and the potential impact of threats and vulnerabilities on a hypothetical organisation. You will be assessed on your ability to identify and prioritise the security risks, threats and vulnerabilities to an organisation.
Background information for Cyber Security Assignment Help From Urgenthomework
In Course 1 of SIT763 you looked at the Cyber Security and SMEs (Small and Medium Sized enterprises).
In light of this, your security company has been hired by a government body to undertake a security review in relation to SMEs.
This body would like you to write a consultancy paper about cyber security risks. Your report should address the following:
- What common cyber security risks, threats and vulnerabilities do SMEs face?
- Based on what we’ve covered so far and your additional research of the literature, what solutions do you propose?
Your task is to assess common security risks, threats and vulnerabilities to a SME and implement appropriate information security protection mechanisms by analysing requirements, plans and IT security policies.
You may also want to reflect on how cyber security issues relating to SMEs are unique
SIT763: IT Security Management by Availing Cyber Security Assignment Help
To prepare your report, you should conduct your research using a variety of sources (including those provided in your prescribed reading list) and reference them.
What do I do now?
- Start collecting and researching information
- Think creatively.
- Develop the report in Microsoft Word format
- Look at the assessment rubric and the unit learning outcomes to ensure that you understand what you are being assessed (and marked) on.
- The problem-solving task should be between 1000-1500 words (not including references).
Answer
Assessment 1: individual problem-solving task 1
Executive summary and description of a SME
Protecting the sensitive data from the hackers needs to be the major priority for businesses of all sizes whether they are small, medium or large enterprises. The threats come in the form of phishing and malware which seeks to infiltrate the corporate network and extract data. The report focuses on security management issues in SMEs and provides an evaluation of risks levels and potential impact of the threats and different vulnerabilities. A hypothetical organisation needs to consider the high-quality services offered to the customers and protecting their data. The clients want to ensure that their information is secured where SMEs focus on ensuring the team members being informed about the current trends of cybersecurity. The assessment is based on developing better plans and IT security policies and proper training of the employees will help in protecting the organisation from the cyber-attacks.
Cyber security risk assessment
Risks: It is the major loss or the damage in SMEs when the threat tends to exploit a vulnerability. Some of the possibilities include the financial loss with disruption in business, privacy, or reputation, with major legal implications that can include the loss of life as well.
- Unprecedented attacks: the valuable information resides in the different sources which grows with time. IoT create unprecedented attacks (Webb et al., 2017).
- Cyber espionage where the SMEs try to store their data in cloud (either in private, public or hybrid cloud technologies), there is a possibility of major loss of data.
- The data privacy and security are at stake when the confidential data is put on the cloud.
Threats
- Internet of Things (IoT) leakage where the real time data collection becomes important. It is important to monitor the traffic and collect the information of patients. The attackers make use of automated programs mainly to locate IoT devices and attackers tend to attempt to connect to the device through default credentials only.
- There are internal attacks which the small business face today. These can be phishing and spear phishing, malware or the spyware or maybe with the actions of disgruntled employee.
- The worms and virus are categorized as threats that tend to harm the organisation mainly through the exposure to the automated attack which is opposed to perpetrations by humans (Tuna et al., 2017).
Vulnerabilities
For SMEs, it refers to the weakness of asset that could be exploited mainly by attackers. For example, if an employee leaves the organisation and his account is not disabled to their access to external accounts, change logins or removing their name from company credit card, then this can lead to the problem of intentional or unintentional threats. The vulnerabilities are mainly due to the automated attackers.There is another possibility in SMEs that they are not able to run antivirus and antimalware software which leads to vulnerability to infections. This fails to routinely update the operating systems or application software with remains of vulnerability to software problems (Baskerville et al., 2018). The user behaviour tends to create opportunities for attackers and system administrator tends to surf the web from account on corporate station could become a victim of the “drive-by” infection of the malicious software mainly.
Security strategy
Cyber security strategy for SMEs that may include
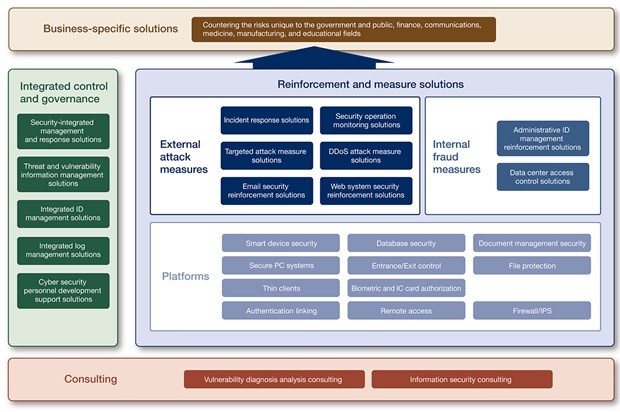
Technical: A proper handling of the external attack measures and internal fraud measures like the DDoS attack measure, web system security reinforcement solution, security operation monitoring solutions, administrative ID management reinforcement solutions could help in handling the technical approach. The firewall, and the IPS is the best platform to authenticate the link and secure the database system. For the security of the system, there are smart device security, a control over the entrance and exist, biometric and IC card authorisation that help in detecting any wrong activity. A proper backup of the system can be an effective measure for the system security (Martellini et al., 2017).
Policy
For the SMEs, the improved cyber security requires a spectrum of defence that builds an approach of prevention control and compliance (Allodi et al., 2017). The cyber resilience includes internal cyber capability, strong governance and proposed a policy for Critical Infrastructure Resilience in July 2015. The strategy stated that the health, safety and prosperity are depending upon certain infrastructure.
Human
In SMEs, the company should keep their employees informed of the trends of cybersecurity and performing regular threat assessments to determine the approach to protect the system and handling the penetration testing that involves the modelling with real world threats. It is important to ensure that the network security antivirus can protect the system, with a data recovery plan in the event of vulnerability being exploited. The risks also need to be assessed which includes the stakeholder perspectives, designating the central group of employees for risk management and determining funding levels for implementing better policies and related controls (Fu et al., 2017).
Governance solutions.
The Privacy and Data Protection Deputy Commissioner handles the information privacy with protective data security (Alassafi et al., 2017). The functions include handling of issuing of protective data security standards and law enforcement data security standards. The development of national cyber defence capabilities is set in regard to broad based collective defence. There is a need to ensure of proper information exchange and cooperation with NATO, and other partners for joint cyber security capabilities, and training opportunities. In cyber security, the digital technology sector and innovation is considered to be the major driving force for a better economic growth, productivity and competitiveness (Deshpande et al., 2017). The digital technology will help in driving innovation and lead to the development of advanced capabilities with growing economy.
Summary of How To Write The Best Cybersecurity Assignment Help
The information technology risks are assessed and measured depending upon the training opportunities given to the people. SMEs needs to ensure the enhancement fight against cybercrime that tends to reduce trust in digital services. The enhancement of detection of cybercrime with law enforcement and raising public awareness could help in preventing cyber threats. The users of e-services are directed to secured solutions and promoting international cooperation against cybercrime (Sadeghi et al., 2017). It is advisable for the people, to change their passwords as soon as they login to the new device. To avoid the large scale cyber incidents, the technological risks pertain to high level of knowledge and risks awareness in developing a state, society and economy. For the SMEs, a standard regulation or an industry framework is important with better information security and oversight responsibilities. A proper integrated control and governance is will help through companywide control and maintaining the security levels as well.
References
Alassafi, M.O., Hussain, R.K., Ghashgari, G., Walters, R.J. and Wills, G.B., 2017. Security in organisations: governance, risks and vulnerabilities in moving to the cloud. In Enterprise Security (pp. 241-258). Springer, Cham.
Allodi, L. and Massacci, F., 2017. Security Events and Vulnerability Data for Cybersecurity Risk Estimation. Risk Analysis, 37(8), pp.1606-1627.
Baskerville, R., Rowe, F. and Wolff, F.C., 2018. Integration of information systems and cybersecurity countermeasures: An exposure to risk perspective. ACM SIGMIS Database: the DATABASE for Advances in Information Systems, 49(1), pp.33-52.
Deshpande, V.M., Nair, D.M.K. and Shah, D., 2017. Major Web Application Threats for Data Privacy & Security–Detection, Analysis and Mitigation Strategies. under review in International Journal of Scientific Research in Science and Technology PRINT ISSN, pp.2395-6011.
Deshpande, V.M., Nair, D.M.K. and Shah, D., 2017. Major Web Application Threats for Data Privacy & Security–Detection, Analysis and Mitigation Strategies. under review in International Journal of Scientific Research in Science and Technology PRINT ISSN, pp.2395-6011.
Martellini, M., Abaimov, S., Gaycken, S. and Wilson, C., 2017. Vulnerabilities and Security Issues. In Information Security of Highly Critical Wireless Networks (pp. 11-15). Springer, Cham.
Sadeghi, A., Jabbari, M., Alidoosti, A. and Rezaeian, M., 2017. Vulnerability and Security Risk Assessment of a Thermal Power Plant Using SVA Technique. Journal of Integrated Security Science, 1(1).
Tuna, G., Kogias, D.G., Gungor, V.C., Gezer, C., Ta?k?n, E. and Ayday, E., 2017. A survey on information security threats and solutions for machine to machine (M2M) communications. Journal of Parallel and Distributed Computing, 109, pp.142-154.
Webb, T. and Dayal, S., 2017. Building the wall: Addressing cybersecurity risks in medical devices in the USA and Australia. Computer Law & Security Review, 33(4), pp.559-563.
Resources
- 24 x 7 Availability.
- Trained and Certified Experts.
- Deadline Guaranteed.
- Plagiarism Free.
- Privacy Guaranteed.
- Free download.
- Online help for all project.
- Homework Help Services
Testimonials
Urgenthomework helped me with finance homework problems and taught math portion of my course as well. Initially, I used a tutor that taught me math course I felt that as if I was not getting the help I needed. With the help of Urgenthomework, I got precisely where I was weak: Sheryl. Read More

