Cryptography Homework Help
Hire Cryptography Assignment Help Professionals to Boost Your Grades
Cryptography is characterized as the craft of composing which is utilized for settling codes and further keep them free from any harm. It is quite possibly the most energizing characteristic of software engineering, which is regularly esteemed by researchers, yet on the other hand for some of them; it ends up being a riddle errand to address. Due to the few methods and coding structures in Cryptography, understudies regularly face masses of troubles in making a task and venture. Nonetheless, there could be a misconception in the ideas by the understudy; there are chances that they may score terrible scores in their scholastics.
Cryptography is to trade data or information between at least two members in a way that can't be deciphered by any other individual. Cryptography in this day and age is truly significant and has numerous applications including the military transfer of messages, organization's high worth data trade, putting away of passwords, and different mysteries. As cryptography includes a comprehension of different encryption and unscrambling calculations alongside many codes, understudies discover it an exceptionally testing subject. Cryptography can't be robbed up or learn, it must be perceived and this is the significant motivation behind why understudies request our cryptography task help. Our expert Cryptography task partners far and wide are the exploration researchers who are very much found with information on Cryptography and the entirety of its connected models and degree.
What is Cryptography Explained By Cryptography Assignment Help Expert?
Inside the setting of software engineering and especially the web, cryptography has numerous fundamental applications. These incorporate the capacity to secret phrase secure documents on the circle – pertinent similarly as a lot to an individual business keeping delicate records hidden as to multi-million dollar ventures. For example, the music, film, and computer game businesses depend intensely on encryption, as the creation organizations that make the media need to guarantee it's just open on specific gadgets or after a specific date (ordinarily known as DRM – Digital Rights Management). In Internet exchanges – for example, shopping, web-based banking, or in any event, signing into a website with a secret phrase – encryption ensures that no worker sitting between a worker and a collector can peruse touchy data consequently bargaining the people groups' records or secret word subtleties. The essential thing behind cryptography is to trade data between two gatherings with the goal that it isn't taken by the other. Cryptography is basic in different applications, particularly in the military. Individuals would utilize this cryptography to send messages to the approved beneficiary just without letting the programmers sneak the data in the middle. The organization's data is likewise traded through cryptography.
Significance of Cryptography by Cryptography homework help Experts
Cryptography is viewed as the most secure and safe approach to move private data over the organization. Today, cryptography permits organizations to work together without taking any strain and moving secret information with certainty.
- Confirmation - Electronic distortion is significant wrongdoing that is capable of by numerous individuals in the nation. A few people are utilizing the bogus mark of the other individual and cheating. The cryptography would assist convey with excursion the electronic exchanges safely.
- Web - There are a large number of frameworks that are associated with the organization. The data would pass starting with one framework then onto the next. This is how correspondence happens worldwide. The cryptography will assist individuals in making sure about their sites and transmissions. It is additionally offering to ascend to the development of electronic trade.
- Access control - Cryptography permits you to deal with digital TV and satellite. It evades the programmers from hacking the link organizations and getting free link administrations.
Topics Covered by Our Cryptography Assignment Experts at Urgenthomework
- Semantic security
- Cryptanalysis
- Symmetric key cryptographic
- Security against plaintext attacks
- Symmetric ciphers
- Web security
- Hash function
- Data encryption standard
- Differential and linear cryptanalysis
- Cryptographic natives
- Message authentication codes
- Cryptosystems
- Problems of secret communication
Cryptography Techniques and Approach to Solve The Cryptography Homework Help Questions
Coming up next are the three diverse cryptography procedures that and students should learn as a component of the software engineering course when they need to dominate in
- Public key cryptography - It clarifies the asymmetric encryption where there would be two key cryptosystems used to keep the association secures between the sender and the recipient. If you are stuck recorded as a hard copy of the task on this subject, you can look for our specialists' assistance. We are accessible nonstop to offer you the necessary assistance.
- Secret key cryptography - This procedure would utilize a solitary key. The sender will utilize this key while making an impression on the beneficiary, and a similar key is imparted to the beneficiary so they can disentangle the message and read it. In this sort of method, there is just one key that is utilized for encryption and unscrambling. Numerous students get mistaken for this idea and search for homework help. Without taking weight on you, employ us. We have experts who do broad exploration recorded as a hard copy of the task for you.
- Hash work - The uprightness of the message is checked utilizing the hash capacity to guarantee that a programmer doesn't bargain the information. It utilizes a specific length needs an incentive over a key.
Single-key (symmetric-key) encryption: -
This sort of encryption implies that a similar key is utilized to encode and unscramble a message. There are two sorts of single key calculations (figures):
- Block Cipher: -In a square code calculation, information is isolated into blocks and scrambled each square in turn. The squares are regularly 64-cycle. Notwithstanding, fresher calculations in some cases utilize 128-cycle blocks. An illustration of symmetric-key cryptography incorporates Advanced Encryption Standard (AES), which is a detail set up in November 2001 by the National Institutes of Standards and Technology as a Federal Information Processing Standard. This standard was made to ensure delicate data and was commanded by the US government. It is broadly utilized in the private organization.
- Stream cipher: -This is a kind of symmetric calculation that encodes the information as a flood of pieces, the slightest bit at a time. Our cryptography task assists specialists with welling knowledgeable with every one of these sorts of codes. You can depend on them to create striking answers for tasks in these zones.
Public-key (asymmetric-key) encryption: -
Public key encryption utilizes a couple of keys, public and private keys which are much of the time yet not compatible.
- The public key is related to the maker or sender of the message.
- The private key is utilized for decoding and is known and shared by the sender. A few conventions rely upon lopsided cryptography. This incorporates the conventions that make HTTPS conceivable like:
- Transport Layer Security (TLS)
- Secure Socket Layer (SSL).
- This sort of encryption cycle can be utilized in programming programs that need to build up a protected association over a shaky organization like the web.
- The public key can be utilized by anybody to scramble a message which can be interpreted by the expected beneficiary utilizing their private key. You can utilize the beneficiary's public key to encode a message before sending it if you need to send a scrambled message.
- The message will be decoded utilizing the receiver's private key. Additionally, a sender can scramble a message utilizing their private key; at that point, the beneficiary will utilize the sender's public key.
Cryptographic Algorithms used in Cryptography Assignment Solutions
- Cryptographic algorithms are a bunch of methodologies that are utilized by cryptosystems.
- They are otherwise called figures that are utilized to scramble and unscramble messages. Cryptographic algorithms secure correspondence among PC frameworks, applications, and gadgets, for example, cell phones. In a code suite, there is one calculation for encryption, one for message confirmation, and another for key trade.
- This entire cycle is written in the product and implanted in conventions that a sudden spike in demand for working frameworks and arranged frameworks. It includes private and public key age for information encryption and decryption, advanced marking of the data and confirming the message, and key trade.
Why should students choose our Cryptography assignment help Services?
- Quality of the assignment: - We have a team of experts who have immense information on cryptography programming task help. Our first goal is to fulfill our clients with our mistake-free quality content. This task will help you secure great scores and improve your insight. We are giving mistake-free and quality content in cryptography assignment.
- 100% free Plagiarism: - We present you with a blunder free and 100% counterfeiting free report in cryptography assignment. Our experts will help you with each schoolwork or task with refreshed counterfeiting free programming so the programming task report you get should be outstanding.
- Delivery before Deadline: - Lots of students neglect to convey their tasks on schedule for a bunch of reasons; that is the reason they get programming task help. Students are searching for help from us because in programming tasks giving 100% mistake-free assignment are not excessively much simple. We never neglect to convey their tasks during the cutoff time.
- 24*7 Customer Support: - Our help is consistently accessible (day in and day out) so you can get in contact with us whenever from wherever around the world. Our client care is another reason which makes us the best specialist co-op. On the off chance that you have any uncertainty or ask about our cryptography programming task, you can contact us through talk, mail, or call. Our experts will help you whenever.
- Affordable cost: - We realize that a few students can't manage the cost of costly administrations. The greater parts of the clients are students so all the help given by us to you is at a reasonable cost. Try not to stress over the value; you will procure help with cryptography programming task help at reasonable costs.
- Guarantee for making sure about the great assignment: - We guarantee you that our specialists can offer you the most astounding administrations in cryptography programming tasks to get the ideal characteristics in your scholastics. They help you in making sure about passing marks in your universities and colleges. Our specialists will help you as you required, and this task will help improve your insight also.
Cryptography Sample Assignment Solved by The Experts at Urgenthomework
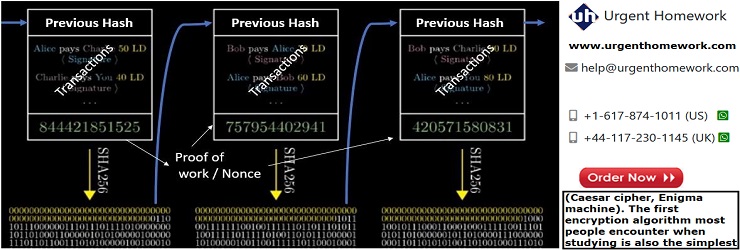
For this task, you will be required to simulate a cryptocurrency system using Python. Cryptocurrencies include two important parts namely: block chaining and block mining. A cryptocurrency network is a decentralized system and there is no central authority to verify transactions. Individuals are free to add new transactions that get broadcasted to the entire network. All transactions must be signed and subsequently verified for legitimacy. Only legitimate transactions are included in new blocks and illegal transactions are rejected. Block miners continuously listen for new legitimate transactions transmitted through the communication network between the participating miners and combine previous hash values and transaction details to compute a unique nonce value that solves the complex computation problem set by the cryptocurrency miner algorithm. The first miner who successfully computes (mines) the correct nonce, broadcasts the new block (previous hash + transactions + proof of nonce calculation work), leading to an update of all transaction entries for all users of the cryptocurrency network. The first successful miner gets rewarded (in cryptocurrency) for the computational effort put in for calculating the correct nonce. Including the hash of the previous block in new blocks is referred to as block chaining. This ensures transactions are not tampered with, as any changes to transactions will change the hash of dependent blocks. The block mining process includes listening for new transactions and combining the hash of previous blocks and the transaction data and then finding the nonce that solves the problem of providing the proof of work. Bitcoin mining or block mining serves to add new blocks as well as release new bitcoins. Furthermore, in a decentralized bitcoin network, adding new blocks to the global blockchain requires the consensus of more than half the mining power. Refer to this YouTube video by 3Blue1Brown to get a better idea of block chaining and cryptocurrencies. The image below shows a sample block-chaining process.
Figure: Blockchaining process illustrated.
This workshop requires you to develop a Python-based cryptocurrency system that has two components:
- Transaction recording program
- Block mining program
Transaction recording program
The main role of this program will be to collect information from the users for new transactions (prompting users to enter the below details through the command prompt) and storing this information into a transaction file. The transaction data should have the following information:
- From (username of the person sending the cryptocurrency amount)
- To (username of the person receiving the cryptocurrency amount)
- Amount
- Timestamp
This program should do the following:
- Loop continuously to prompt the user if a new transaction needs to be added to the chain.
- If yes prompt for FROM name, TO name, and AMOUNT to send.
- Store the transaction details in a transaction file in the current directory.
- Provide an option to quit the program during its flow.
Block mining program
This program constantly checks the transaction file for new transactions. Once new transactions are detected, the mining program combines the hash of the previous block and the transaction data and then calculates the correct nonce for the block. The successful SHA256 hash is added to the blockchain file (BC). The block structure should be as follows:
- Block Index
- Data
- Previous block’s hash (using SHA256)
- Nonce (calculated using a mining function)
When the mining program is first executed, create the first block with an index 0 and an arbitrary previous hash value. The program should comprise the following steps:
- Create a BlockChain (BC) file in the current directory
- Check the BC file to see if any hashes of previous blocks already exist. If not, create the first block with an index = 0, data = “first block”, current timestamp and the SHA-
256 hash of “the first block”. Add the hash of the first block to the BC file.
- When new transaction data is detected, calculate the nonce that produces an SHA-256
(previous block’s hash + transaction data + nonce) hash which contains 14 zeros. (Why
14 zeroes? Because it is an arbitrary number that we have chosen for CSI 2108, and it
adds to the computational work that needs to be done to find the hash value of the above tuple: previous block’s hash + transaction data + nonce). Refer to the nonce calculation pseudocode given below.
- Add the successful hash to the blockchain file.
- Continuously loop through these steps to add blocks comprising new data unless the user wants to exit.
Pseudocode of nonce calculation function:
Create a new block = (index + timestamp + data + previous block’s hash) Initialise a nonce variable to zero Continuous loop: Update block by concatenating the nonce Calculate the SHA-256 of the updated block Check if the message digest has 14 zeros: Update the BC file with the successful hash Break Check if the nonce value exceeds 50000 (this step is performed to prevent an infinite loop): Update the BC file with last produced hash Break Increment the nonce
Requirements
You must include the following with your submission:
- The source code for your implementation of the block chaining a mining system
- Documentation explaining your implementation
- Instructions for running your program to complete the required objectives
Marking key:
- File handling (2)
- Using appropriate hashing libraries from Python (2)
- Block formation (3)
- Nonce calculation (4)
- User interaction (2)
- Correct results (2)
Topics in Programming
- MATLAB Homework Help
- Database Homework Help
- Assembly Language
- Computer virus
- Fortran Homework Help
- Game programming language
- JavaScript
- Java Servlets Help
- Machine Language
- Pascal
- Perl
- PHP
- Python
- Visual Basic
- Matlab
- Ada
- Assembly Language
- BASIC
- Computer virus
- C Programming
- Euphoria
- Fortran Homework Help
- Game programming language
- Java Assignment Help
- JavaScript
- Java Servlets Help
- Machine Language
- Pascal
- Perl
- PHP
- Python
- Ruby
- Servlet Life Cycle
- Smalltalk
- SOAP
- Visual Basic
- COBOL
- Lisp
- Logo Help
- Plankalkul Help
- Prolog
- REBOL
- Rexx
- Scheme Help
- TCL
- ToonTalk Help